A newly discovered information stealer named Arcane is being distributed through YouTube videos advertising game cheats.
According to a Kaspersky report, the malware is capable of stealing account credentials from popular VPN services, gaming clients, network utilities, and cryptocurrency wallets. The campaign, active since late 2024, initially relied on another stealer called VGS before switching to Arcane, which has since evolved with frequent updates.
Discovery and distribution
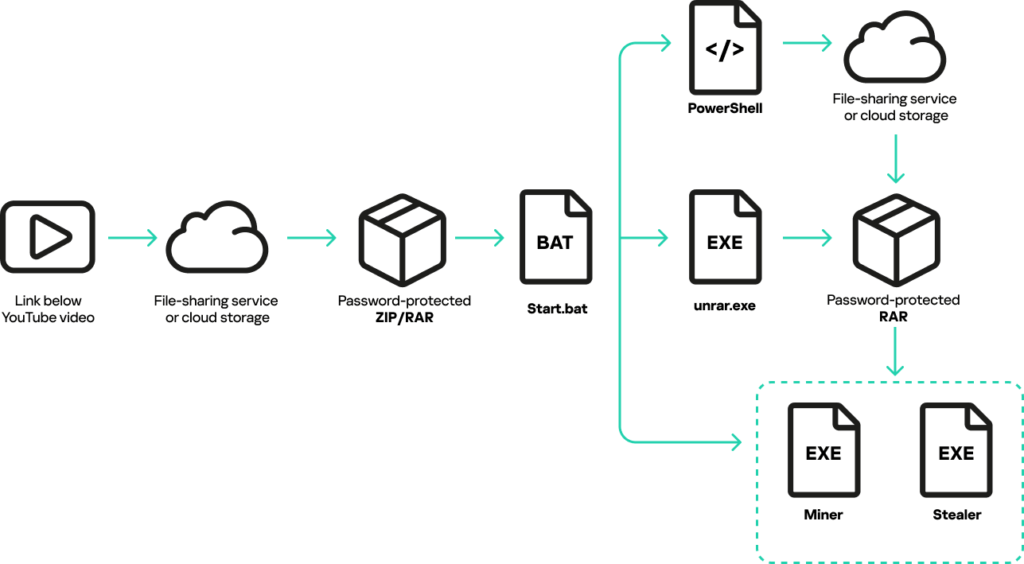
The malware campaign was identified by Kaspersky researchers in late 2024 while investigating malicious YouTube content. Attackers posted videos promoting gaming cheats and cracks, providing links to password-protected archives. Upon extraction, the archive contained a batch file (start.bat) and a utility (UnRAR.exe) designed to execute malicious commands.
The batch file was heavily obfuscated, with its primary function being to download a second password-protected archive via PowerShell, extract it, and execute a miner and a stealer. The malware also modifies Windows registry keys to disable Microsoft SmartScreen, and adds all drive root folders to Windows Defender exclusion lists, ensuring it remains undetected.
Kaspersky
Evolution from VGS to Arcane
Prior to Arcane, the Phemedrone-based VGS stealer was used in the same campaign. However, in November 2024, Arcane replaced VGS. While it borrows elements from other known stealers, Kaspersky found no direct attribution to any specific malware family. The name “Arcane” comes from ASCII art embedded within the malware's code.
Unlike its predecessor, Arcane receives frequent updates, continuously refining its stealing techniques and expanding its target scope.
Broad data theft
Arcane has an extensive list of targets, including:
- VPN Clients: OpenVPN, Mullvad, NordVPN, IPVanish, Surfshark, ProtonVPN, CyberGhost, ExpressVPN, and others.
- Network Utilities: ngrok, Playit, Cyberduck, FileZilla, DynDNS.
- Messaging Apps: Discord, Telegram, Skype, Signal, ICQ, Pidgin, Element, Viber.
- Gaming Clients: Steam, Epic Games, Ubisoft Connect, Riot Client, Roblox, Battle.net, Minecraft launchers.
- Email Clients: Outlook.
- Cryptocurrency Wallets: Zcash, Armory, Bytecoin, Jaxx, Exodus, Ethereum, Electrum, Atomic, Guarda, Coinomi.
In addition to stealing credentials, Arcane collects system information such as:
- OS version, installation date, and license key.
- Usernames, computer names, and geographical location.
- CPU, memory, and graphics card details.
- List of installed antivirus solutions and web browsers.
- Wi-Fi network credentials stored in the system.
- Screenshots of the infected device.
The malware also exploits the Data Protection API (DPAPI) to extract saved passwords, cookies, and autofill data. It also utilizes an embedded Xaitax utility to decrypt browser encryption keys.
Additionally, Arcane can extract cookies from Chromium-based browsers by enabling remote debugging. It secretly launches a browser instance with the “remote-debugging-port” flag, connects to it, and retrieves authentication cookies from websites like Google Drive, Gmail, Twitter, YouTube, Steam, Roblox, Ozon, and Avito. This method allows Arcane to bypass password prompts and hijack sessions.
A new delivery method
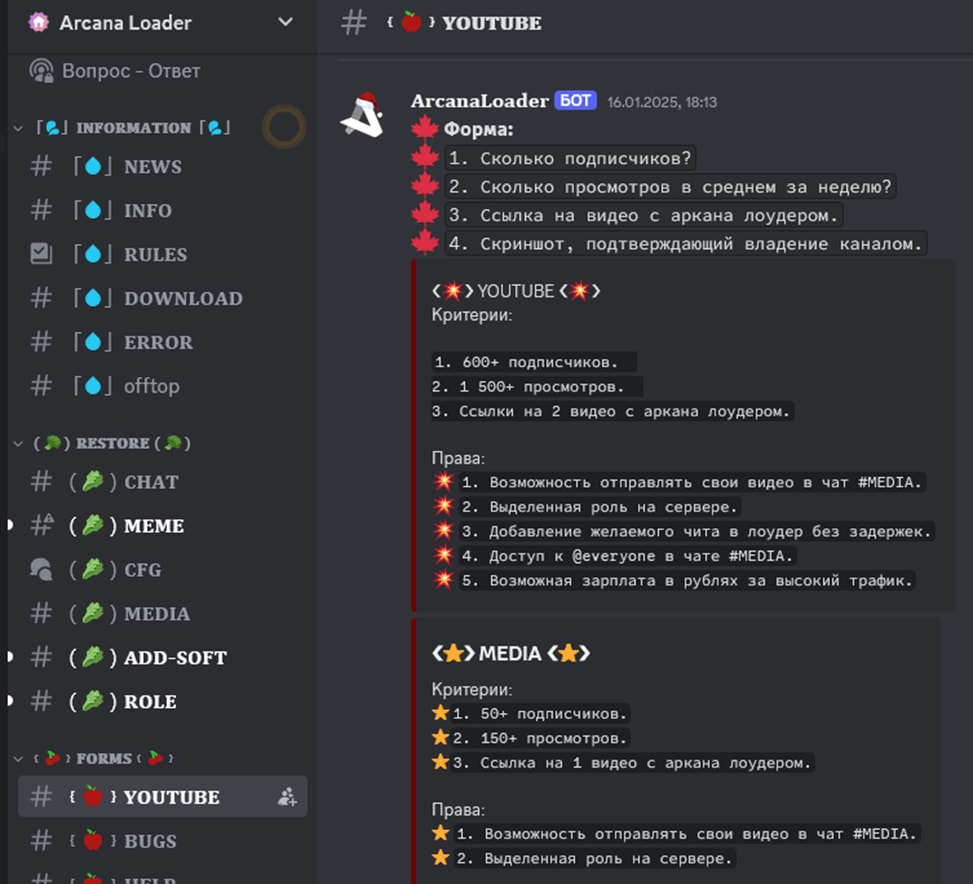
By early 2025, attackers shifted to a new distribution model using ArcanaLoader, a malware loader disguised as a cheat manager. Unlike earlier campaigns, where users downloaded malware disguised as cheats, ArcanaLoader presents itself as a legitimate tool for managing cracks and mods.
Users were lured into downloading ArcanaLoader via YouTube videos, which redirected them to an executable file that fetched an infected archive. Once executed, ArcanaLoader would deploy Arcane stealer in the background.
Attackers also promoted ArcanaLoader through a Discord server, which included channels for updates, support, and recruitment. One of the channels even advertised paid opportunities for bloggers to promote the malware.
Kaspersky
Targeting scope
Analysis of the Discord server and YouTube content revealed that the campaign primarily targets Russian-speaking users. Conversations, announcements, and promotional content were all in Russian. Kaspersky's telemetry data confirmed most infections were in Russia, Belarus, and Kazakhstan, though the company's visibility in the Western world has been limited due to recent bans on its products.
While this campaign appears localized, the stealer's capabilities make it a potential global threat if its distribution methods expand.
To protect against Arcane Stealer and similar threats, avoid downloading cheats and cracks from untrusted sources, especially YouTube links. Also, enable Microsoft SmartScreen and ensure it remains active in system settings, and use a reputable antivirus solution with real-time protection enabled. To protect your accounts from information-stealing malware, regularly change passwords and use two-factor authentication (2FA).







i really wonder how investors will act, if discord will make it to stockx. it’s full of p3dos, hackers and hacks, rasicts… you name it. i really whish discord will get sucked up by a low valuation (i know, probably wont happen) or getting hacked by the users kekw