
Ukraine's cybersecurity agency, CERT-UA, has warned that Russian-linked threat actors are using the encrypted messaging app Signal to distribute the DarkCrystal RAT (DCRAT) malware, targeting high-value individuals in the country's defense sector.
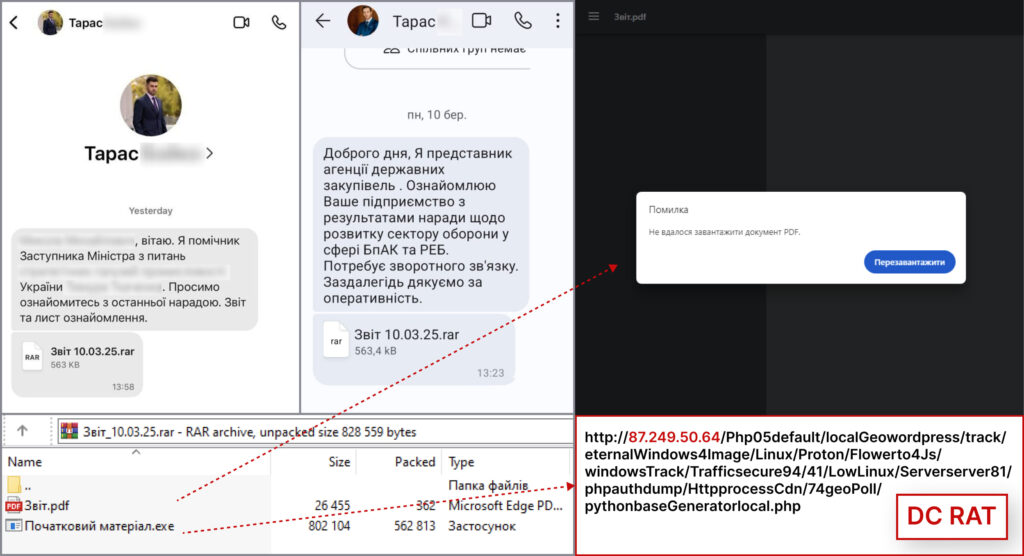
Attackers have been spreading malicious archives disguised as meeting reports, leveraging compromised accounts to enhance credibility.
Signal used to deliver DarkCrystal RAT
According to CERT-UA's latest bulletin, observed cyberattacks in March 2025 involved malicious messages sent via Signal containing ZIP or RAR archives. These archives include a decoy PDF file, typically appearing as an official report, and an executable file associated with DarkTortilla, a loader designed to deploy and inject DarkCrystal RAT (DCRAT) onto the victim's system.
DCRAT, a well-documented remote access trojan (RAT), enables attackers to execute arbitrary commands, steal sensitive data, and establish persistent control over infected systems. CERT-UA noted that the campaign has been active since at least mid-2024, with recent phishing lures referencing drones (UAVs) and electronic warfare (EW) systems — a shift reflecting Ukraine's military priorities.
The attackers exploit compromised Signal accounts to send messages from trusted contacts, increasing the likelihood that recipients will open the malicious files. This tactic, combined with Signal's strong encryption and privacy focus, makes detection and mitigation more challenging.
CERT-UA
Alleged inaction on Russian cyberthreats
News about this attack wave follows Signal's reported decision to stop cooperating with Ukrainian authorities on cyber threats linked to Russian intelligence. On March 14, 2025, Serhii Demediuk, Ukraine's Deputy Secretary of the National Security and Defense Council, accused Signal of ignoring warnings about Russian espionage operations on its platform.
Demediuk claimed that Ukraine had previously collaborated with Signal to counter phishing attacks, account takeovers, and abuse of the “linked devices” feature, which allows attackers to sync compromised accounts across multiple endpoints. However, he stated that Signal had ceased responding to Ukrainian requests, making it easier for Russian operatives to conduct cyber-espionage campaigns.
Signal, known for its strict stance on user privacy, did not officially respond to these claims. However, its CEO, Meredith Whittaker, denied the accusations via a post on Mastodon, stating:

Whittaker's comments suggest that Signal maintains a neutral, non-cooperative policy with all governments, reinforcing its commitment to privacy even in the face of geopolitical tensions.
The latest cyberattacks highlight a broader shift in Russian cyber tactics, as attackers increasingly use encrypted communication apps instead of traditional e-mail attacks to evade detection and security monitoring.
Given the increased cyber threat activity on Signal, CERT-UA recommends that high-value targets verify message sources and be very cautious when receiving files, even from known contacts. If suspicious, confirm through a secondary channel. It is also recommended to disable auto-downloads to prevent Signal from automatically saving media and documents and to regularly review linked devices and revoke unknown connections.







Leave a Reply