
Security researchers at Bitdefender have uncovered a massive ad fraud campaign involving at least 331 malicious apps that managed to bypass Android 13's security measures, racking up over 60 million downloads on Google Play.
The apps, which masquerade as harmless utilities, not only bombard users with intrusive ads but also attempt to steal credentials and credit card data through phishing attacks.
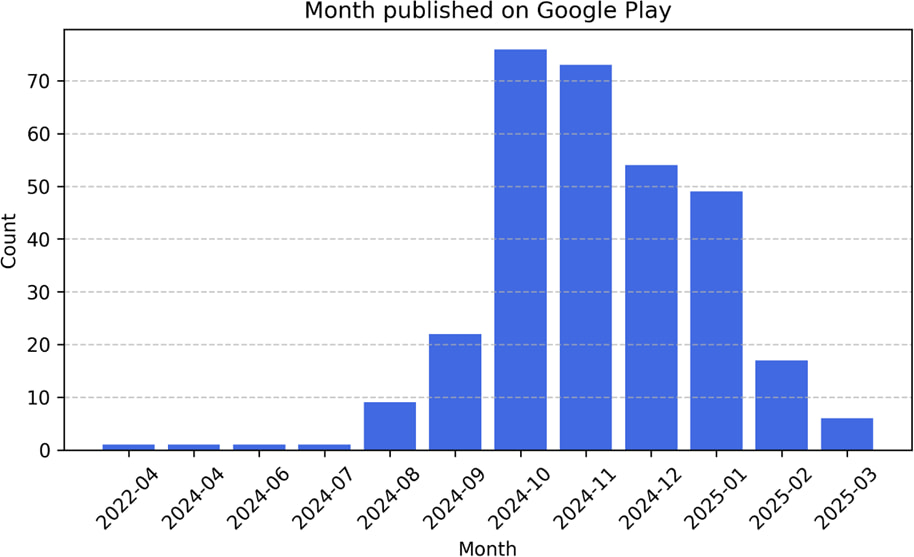
The campaign, first identified by IAS Threat Lab as part of an operation codenamed “Vapor,” has been active since early 2024. Researchers initially found 180 malicious apps, but Bitdefender's subsequent investigation revealed a much larger operation. The apps exploited a loophole in Android 13's security to hide their icons, making it difficult for users to detect and remove them. Furthermore, they could launch themselves without user interaction, a behavior that should be restricted in newer Android versions.
Advanced fraud scheme
The Vapor operation, as detailed in a report by IAS Threat Lab, was designed to generate revenue through fraudulent ad impressions. The scheme involved multiple developer accounts, each hosting only a few apps to avoid detection. By embedding various ad SDKs and controlling their own seller accounts, the attackers could profit from ad networks while ensuring their apps remained active despite occasional Google Play takedowns.
Bitdefender
The apps initially appeared benign, but updates later introduced malicious features such as ad injection and phishing interfaces. To avoid user detection, they removed their launch icons and even disguised themselves in device settings under names like “Google Voice.”
From a technical perspective, the apps leveraged the DisplayManager.createVirtualDisplay API to display fullscreen ads without explicit permissions. Additionally, they used encrypted communications and obfuscation techniques such as XOR-based string encoding to hide their true nature.
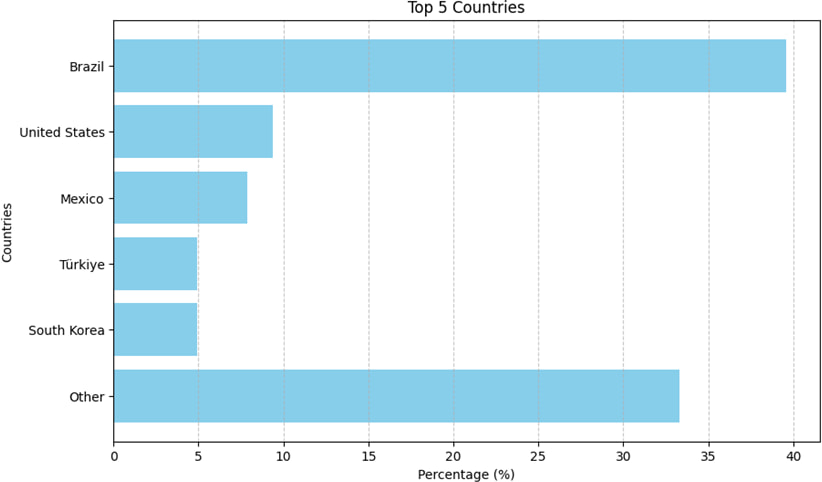
The campaign affected millions of devices globally, with over 200 million fraudulent ad impressions generated daily.
Bitdefender
Apps gone but threat still looms
Following IAS Threat Lab's research, Google took action in early 2025 by removing identified malicious apps from the Play Store and enhancing Play Protect to warn users about these threats. However, the rapid adaptability of attackers means new variants may emerge soon.
To safeguard against such threats, users should avoid installing apps with vague functionality like QR scanners, wallpaper apps, or basic utilities from unknown developers, check app permissions and be wary of those requesting unnecessary access. It's also good practice to manually verify installed apps by checking for hidden or renamed entries in settings. Finally, make sure to enable Google Play Protect to receive warnings about potentially harmful apps.







Leave a Reply