
The notorious Quad7 botnet, also known as the 7777 botnet, continues to evolve its operations, with recent discoveries pointing to significant changes in both its targeting and attack methods.
According to a new report by Sekoia.io, the operators of Quad7 are developing new backdoors and infrastructure to enhance the botnet’s resilience while maintaining its ability to carry out brute-force attacks. This development marks a notable shift from earlier tactics that focused heavily on compromised TP-Link and ASUS routers using Socks5 proxies.
New *login variants
Since its first report in October 2023, Quad7 has undergone a steady transformation. Originally known for its reliance on TP-Link routers, it now incorporates a range of devices, including ASUS routers, through a secondary network using TCP port 63256. Quad7's operations originally used Socks5 proxies to relay attacks against Microsoft 365 accounts, employing compromised routers as conduits for password-spraying attacks. However, the latest report indicates that the botnet operators are diversifying their approach, using new malware and reverse shells instead of Socks5 proxies.
Sekoia.io's research team recently uncovered additional clusters linked to the Quad7 operators, including variants such as the *login botnets (alogin, xlogin, rlogin, and others). Each variant targets different types of devices:
- Alogin botnet: ASUS routers using TCP ports 63256 and 63260 for brute-force attacks on exposed services like VPN, SSH, and Telnet.
- Rlogin botnet: Targets Ruckus wireless devices, a relatively smaller botnet with 213 devices compromised as of August 2024.
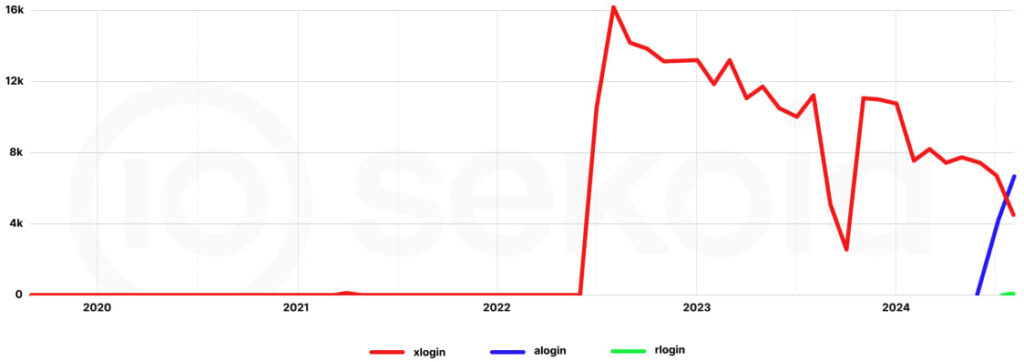
Sekoia
This diversification reflects the botnet operators' adaptability and their pursuit of new attack vectors. Moreover, the operators seem to be actively testing reverse shells for future deployments, possibly to avoid detection and reduce the likelihood of other threat actors hijacking their infrastructure.
New “UPDTAE Backdoor” and “FsyNet” implants
A critical discovery involves the “UPDTAE backdoor,” a new reverse shell implant currently in testing by the Quad7 operators. These backdoors, hosted on staging servers, are poorly designed yet effective, sending beaconing requests via HTTP every 30 seconds. The UPDTAE implants were found on both ASUS routers and Axentra NAS devices, with different versions for MIPS and ARM architectures. These backdoors allow the botnet operators to execute commands and potentially update command-and-control (C2) URLs, providing them with greater control over compromised devices.

Sekoia
Alongside these implants, Sekoia.io also uncovered a more sophisticated project named “FsyNet.” FsyNet uses the KCP protocol, typically employed for creating reliable connections over unreliable networks, and is designed to establish a chain of compromised operational relay boxes (ORBs). This approach suggests that Quad7 may be transitioning away from Socks5 proxies toward a more secure and less detectable method of communication.
Broader impact and recommendations
Quad7's continued expansion, particularly its shift toward devices such as ASUS and Ruckus routers, poses a growing threat to internet-exposed services worldwide. ASUS, a leading manufacturer in the consumer and enterprise router markets, provides a significant footprint for the botnet to exploit. The Quad7 operators' ability to compromise such widely used devices indicates the botnet’s increasing capacity to scale its operations while avoiding detection.
The botnet's new tactics not only highlight its adaptability but also its operators' intent to remain under the radar. By moving away from open Socks5 proxies and experimenting with reverse shells, Quad7 is making it more challenging for cybersecurity teams to track its activities through conventional scanning tools. The introduction of FsyNet could further complicate detection efforts by creating an encrypted, decentralized network for botnet management.
Given Quad7’s evolving nature, it is essential for network administrators to implement stringent defense measures. These include:
- Regular firmware updates for all devices, particularly routers from brands like ASUS and TP-Link.
- Use of strong, unique passwords for administrative interfaces, and disabling unused services.
- Limiting remote access to trusted IP addresses or disabling remote administration entirely.
- Monitoring network activity for unusual behavior, particularly on ports commonly used by Quad7 (e.g., 7777, 63256, 63260).
- Deploying advanced detection tools such as Suricata and YARA rules to identify Quad7’s unique signatures, including the new UPDTAE backdoor.







Leave a Reply