
Security researchers from George Mason University have uncovered a new attack, called nRootTag, that allows attackers to turn Bluetooth-enabled devices into covert Apple AirTag-like trackers — without needing root privileges.
The new method exploits Apple's Find My network, which consists of over a billion Apple devices, to silently track computers, smartphones, and IoT devices with alarming efficiency.
cs.gmu.edu
How nRootTag works
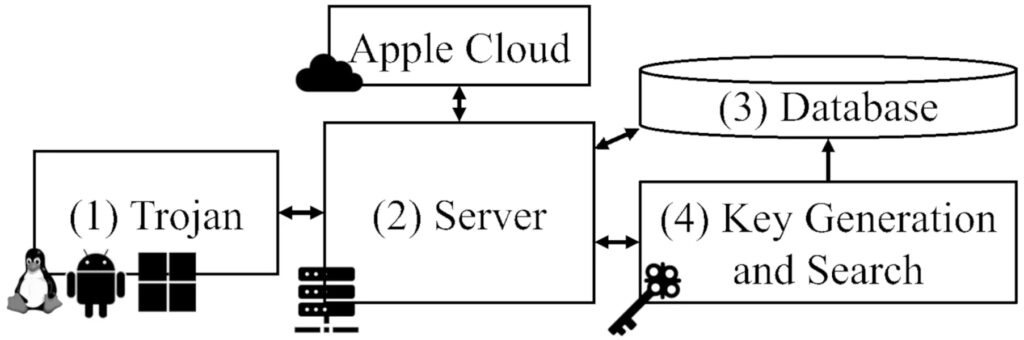
Unlike previous methods such as OpenHayStack, which required root privileges to modify BLE (Bluetooth Low Energy) advertising addresses, nRootTag avoids this restriction by leveraging precomputed key searches. The attack consists of the following steps:
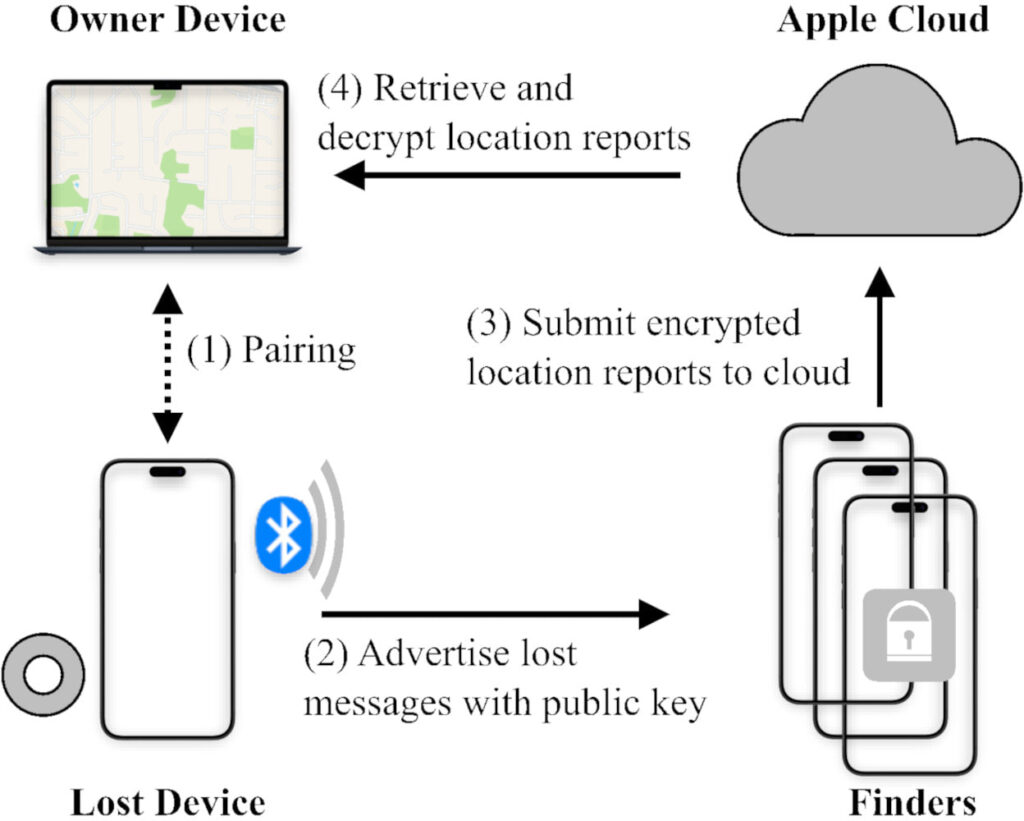
- Acquiring a Device's BLE Address – The attacker retrieves a device's Bluetooth advertising address, either from a local query or by sniffing nearby advertisements.
- Generating a Matching Public/Private Key Pair – Instead of modifying the advertising address (which requires root privileges), nRootTag searches for a cryptographic key pair that naturally matches the address.
- Broadcasting “Lost” Messages – The infected device starts advertising a public key as if it were a lost AirTag, prompting Apple devices nearby to report its location to Apple's servers.
- Extracting the Location from Apple Cloud – The attacker uses a hashed public key to request encrypted location reports from Apple Cloud and then decrypts them using the private key.
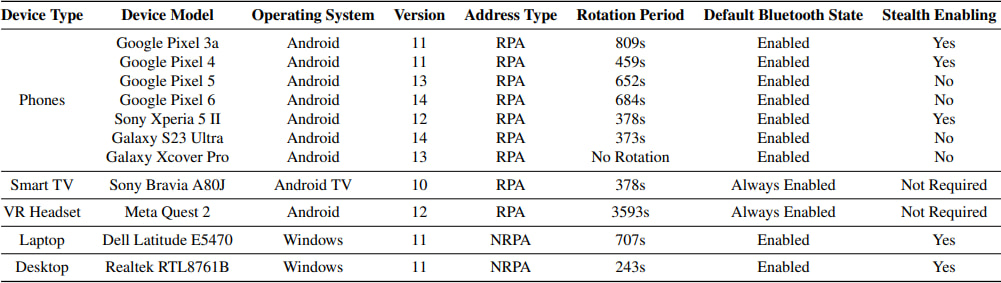
The attack is remarkably efficient and stealthy, working across Linux, Windows, and Android operating systems. Evaluation results showed a success rate exceeding 90% in under three minutes. Attackers can track desktops, laptops, smartphones, and IoT devices, while the attack can be executed for just a few dollars, and tracking costs do not increase with the number of devices being monitored.
cs.gmu.edu
Unlike previous tracking attempts that relied on IP geolocation (which is unreliable due to NAT and VPNs), or Wi-Fi MAC address tracking (which is mitigated by address randomization), nRootTag exploits Apple's Find My network's global coverage — making it nearly impossible for victims to detect.
cs.gmu.edu
Abuse scenarios and protection
Several malicious entities could exploit this attack, including spyware and adware developers tracking users for behavioral profiling, nation-state actors conducting surveillance operations, cybercriminals running large-scale botnets for extortion and phishing, and even legitimate shopping, streaming, or social media apps with Bluetooth permissions could implement nRootTag without raising suspicions.
Apple's Find My network includes unwanted tracking alerts, but nRootTag can evade these by modifying the “Status” field in lost messages. This makes tracking alerts unlikely to trigger, particularly for stationary devices like desktops, TVs, and gaming consoles.
A possible mitigation would be Apple to restrict Find My network participation to devices using only random static addresses — as originally specified in its protocol. On the users' side, it's important to be cautious about Bluetooth permissions granted to apps, especially those that do not explicitly need Bluetooth functionality.






Leave a Reply