
A newly discovered vulnerability in China's Great Firewall (GFW), dubbed Wallbleed, exposed sensitive memory data from its censorship infrastructure for over two years.
The flaw leaked up to 125 bytes of internal memory whenever a specially crafted DNS query was injected into the system, offering an unprecedented view into China's nationwide censorship mechanisms.
The vulnerability was uncovered by a team of researchers from the University of Colorado Boulder, University of Massachusetts Amherst, Shinonome Lab, and independent researchers from GFW Report. The team conducted an extensive study spanning two and a half years, beginning in October 2021. Their findings were presented at the Network and Distributed System Security Symposium (NDSS) 2025.
The researchers reverse-engineered the GFW's DNS injection system, analyzed the extent of the memory leaks, and monitored China's censorship apparatus to track the firewall's patching behaviors. The research involved large-scale Internet-wide measurements and probing across various networks to understand the potential implications of the vulnerability.
Understanding Wallbleed
Wallbleed affected the DNS injection subsystem of the GFW, which manipulates DNS responses to block access to restricted domains. The flaw stemmed from a buffer over-read bug, where a vulnerable middlebox would mistakenly include parts of its memory when generating a fake DNS response. This flaw was similar in nature to other notorious memory disclosure bugs like Heartbleed and Cloudbleed.
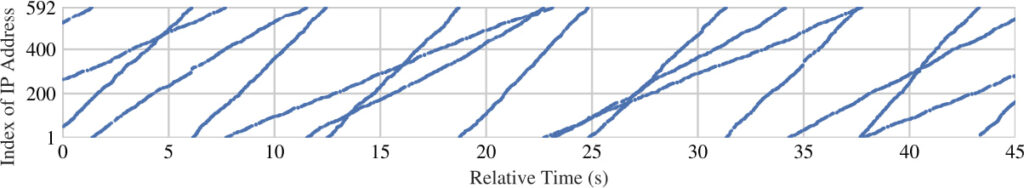
gfw.report
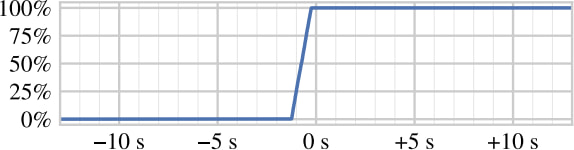
gfw.report
The researchers' longitudinal study revealed that:
- The vulnerability existed for at least two years, with possible traces of similar issues dating back to 2010.
- Wallbleed leaked portions of memory that included fragments of plaintext Internet traffic, HTTP requests, TCP segments, and other data seen by the firewall.
- The GFW attempted an incorrect patch in November 2023, which only partially fixed the issue. A complete fix was deployed in March 2024.
Implications and ethical considerations
The researchers found that the leaked data included network protocol headers, payloads, x86_64 stack frames, and even executable code fragments. While it remains unclear if this data belonged to the GFW itself, it suggests that the system inadvertently disclosed sensitive traffic information.
Their study also provided critical insights into how China's censorship infrastructure operates, including the load-balancing mechanisms of the censorship devices, the process-level architecture of the injector nodes, and the internal IP address cycling behavior used by the firewall.
This vulnerability demonstrates that censorship infrastructure when poorly implemented, not only infringes on freedom of expression but also poses severe security and privacy risks for Internet users.
The study sparked ethical debates within the security research community. The NDSS 2025 Program Committee acknowledged the research's technical contributions but expressed concerns over the ethical implications of the experiments. While the authors followed ethical guidelines, questions arose over the risks posed by actively probing a government-run censorship system.
The NDSS Ethics Review Board scrutinized the research, and while the paper was accepted, the committee did not endorse the methodology. Researchers were advised to seek legal guidance when conducting similar security studies, particularly when targeting critical government infrastructure.
While the vulnerability has been patched, Wallbleed highlights broader concerns about Internet censorship and security. Users affected by China's GFW should use encrypted DNS services such as DoH or DoT to prevent DNS injection attacks, deploy VPNs or circumvention tools to bypass the GFW's censorship mechanisms and monitor network traffic for anomalies that may indicate interference from censorship middleboxes.






Leave a Reply