A data breach in the spyware applications Cocospy and Spyic has exposed the personal data of millions of people, including sensitive information such as messages, photos, and call logs.
The breach, discovered by a security researcher, affects both the operators of the spyware and the victims whose devices were unknowingly compromised.
Cocospy and Spyic data leaked
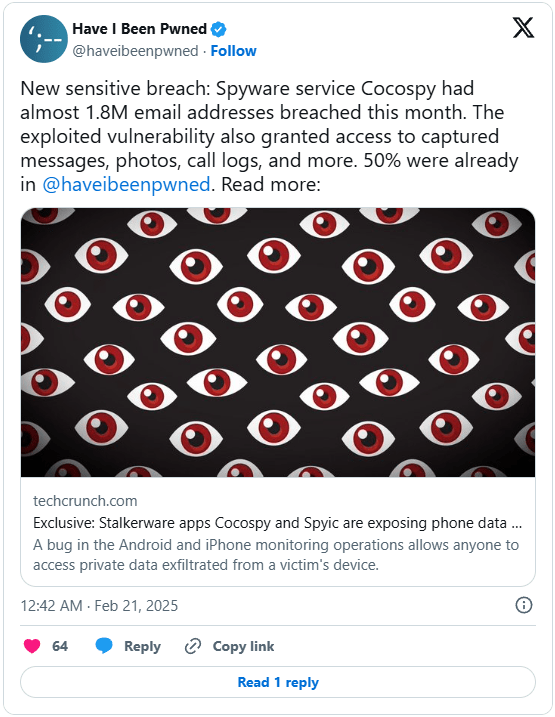
The breach, which occurred on February 14, 2025, exposed a total of 2.65 million unique email addresses of Cocospy and Spyic customers. This data was collected by a researcher and provided to Troy Hunt, the operator of the data breach notification service Have I Been Pwned (HIBP). The emails were scraped from the spyware's servers due to an unpatched flaw that allowed unauthorized access to stored user information. The source of the leak, who identified themselves as “zathienaephi” shared the dataset with HIBP, which added it to its database yesterday. (1, 2)
The alerting platform noted on X that roughly half of the exposed data is “fresh,” not having been exposed in any past security incidents.
Cocospy and Spyic are widely used stalkerware applications, often marketed as parental control or employee monitoring tools but frequently exploited for illegal surveillance of spouses and partners. These apps operate covertly, remaining hidden on a victim's device while continuously transmitting personal data to a remote dashboard accessible by the person who installed them. The stealthy nature of spyware makes it difficult for victims to detect and remove, putting their privacy at serious risk.
The leaked data includes:
- 1.8 million email addresses from Cocospy customers
- 876,000 email addresses from Spyic customers
- Stored messages, call logs, photos, and other personal data
Cocospy and Spyic are not standalone services but are built on a common spyware codebase, suggesting a shared infrastructure. According to security researchers Vangelis Stykas and Felipe Solferini, both apps have links to 711.icu, a now-defunct China-based mobile app developer known for spyware operations. The researchers' previous investigations have uncovered similar flaws in multiple stalkerware applications, indicating a pattern of poor security practices in the industry.
TechCrunch, which analyzed the applications on a virtual device, found that Cocospy and Spyic disguise themselves as innocuous “System Service” apps on Android devices, allowing them to avoid detection. Data exfiltrated by the apps is routed through Cloudflare, concealing the true location of their servers. Additionally, some stored data was found on Amazon Web Services (AWS), raising concerns about how mainstream cloud providers are being misused to facilitate spyware operations.
No response from vendors
Despite the severity of the breach, the operators of Cocospy and Spyic have not responded to inquiries, nor have they taken steps to fix the vulnerability at the time of reporting. This means that the exposed data remains accessible to anyone with knowledge of the flaw, further endangering the privacy of victims.
With spyware applications already violating ethical and legal boundaries, security flaws like this only compound the risk, potentially allowing malicious actors to exploit stolen data for blackmail, harassment, or identity theft. In previous spyware-related breaches, leaked customer information has been linked to cases of domestic abuse and stalking, underscoring the dangers posed by such applications.
Recommended actions
Given the clandestine nature of Cocospy and Spyic, victims may be unaware that their device is compromised. However, there are steps to identify and remove these apps:
- Go to the Android Settings > Apps menu and check if “System Service” or any suspicious applications are installed.
- On an Android device, dialing ✱✱001✱✱ and pressing the call button may reveal the spyware app's interface.
- Enable Google Play Protect, Android's built-in security feature that can detect and block many spyware applications.
- iPhone users should ensure their Apple ID has two-factor authentication enabled and remove unrecognized devices from their account.
- Use unique, strong passwords and enable multi-factor authentication on all online accounts to reduce the risk of unauthorized access.







Leave a Reply