
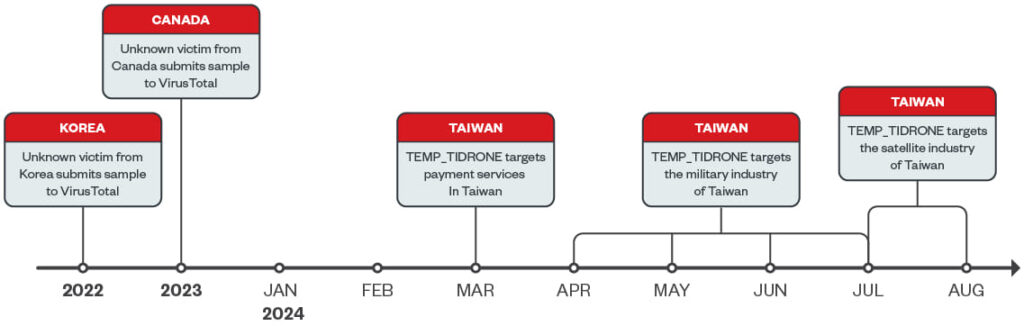
Trend Micro has uncovered a new threat group, dubbed TIDRONE, targeting Taiwan's military and satellite industries, with a specific focus on drone manufacturers. This campaign employs advanced malware and espionage tactics, likely linked to a Chinese-speaking cyber espionage group.
The TIDRONE campaign, active since early 2024, is suspected to be a supply chain attack, leveraging vulnerabilities in ERP systems to infiltrate multiple organizations. The campaign's operational timeline suggests a long-term espionage mission focused on Taiwan's military sector, with telemetry logs revealing traces of lateral movement across compromised environments.
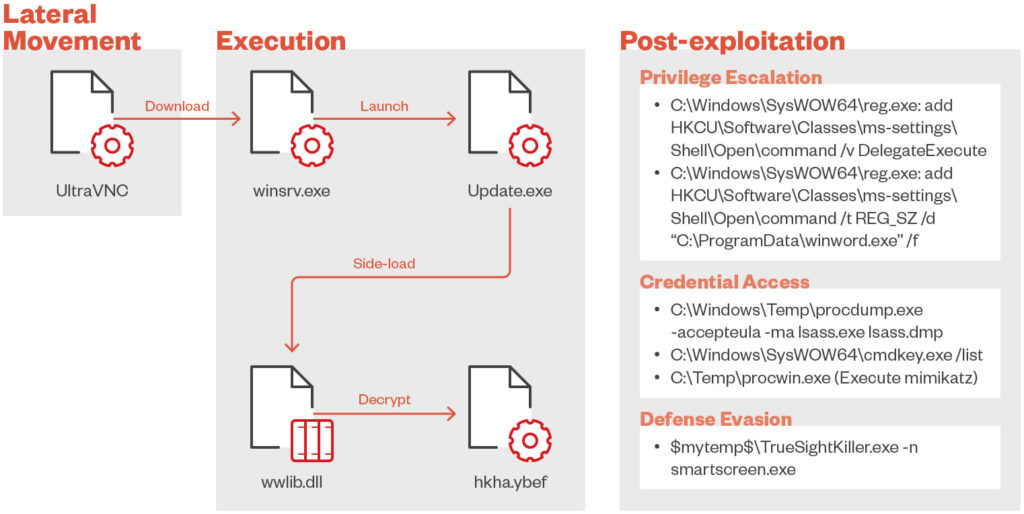
Attackers also utilize tools like UltraVNC to gain unauthorized remote access, manipulating legitimate executables to escalate privileges and evade detection.
Trend Micro
TIDRONE's custom malware
TIDRONE infiltrates systems by exploiting vulnerabilities in remote desktop connections and enterprise resource planning (ERP) software, two commonly used tools in business environments, to gain unauthorized access. Once inside, the group deploys custom malware such as CXCLNT and CLNTEND, each designed for specific stages of the attack.
Trend Micro
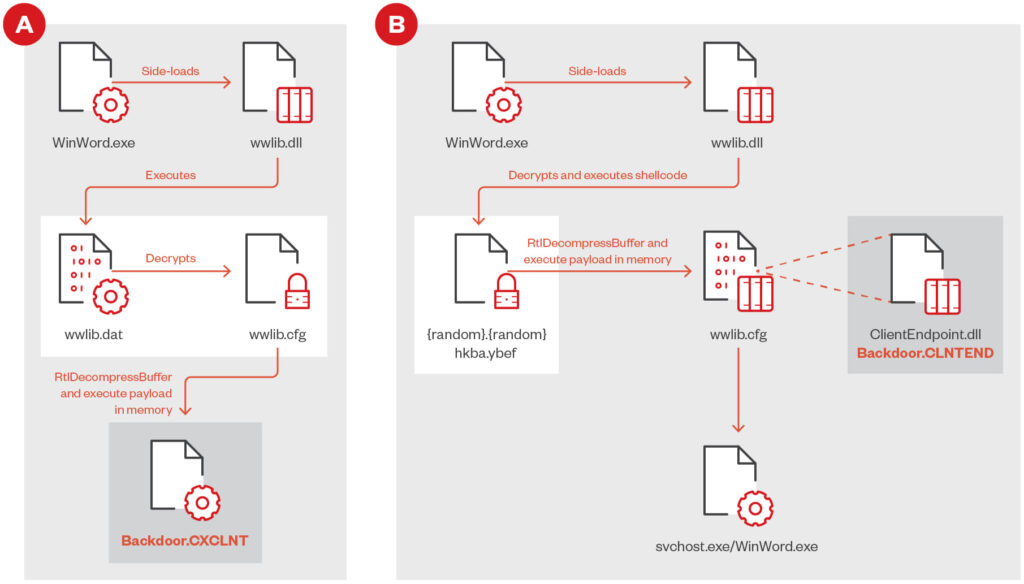
CXCLNT, an earlier variant in the group's arsenal, is capable of basic functions such as uploading, downloading, and executing additional portable executable (PE) files. It also collects crucial system information, including file listings and computer names, which aids in expanding the attack and maintaining persistence within the targeted network.
CLNTEND, a newer remote access tool (RAT) discovered in April 2024, enhances the attackers' ability to communicate with their command and control (C&C) servers by supporting a broader range of network protocols, such as HTTP, HTTPS, and SMB. This versatility allows attackers to adapt to different environments and ensures continuous data exfiltration, even in highly secured networks. Both malware variants play a pivotal role in stealing sensitive data, including intellectual property, and enable extensive system exploitation through lateral movement across compromised networks.
Trend Micro
What makes these tools stand out is their advanced anti-analysis features. For instance, they can hook widely used system APIs such as GetProcAddress to alter the execution flow, making them harder for security researchers to detect and analyze. Additionally, they utilize persistence techniques such as bypassing User Account Control (UAC), a security feature designed to prevent unauthorized changes to a system.
These custom malware families also perform credential dumping—extracting stored passwords and authentication tokens—and disable antivirus software, clearing the path for further malicious activities. This combination of stealth, persistence, and adaptability underlines the group's espionage-oriented objectives.
Conclusion
Taiwan's defense and satellite sectors are integral to the nation's strategic positioning, especially given ongoing geopolitical tensions with China. Companies manufacturing drones and other sensitive military technologies are naturally prime targets for cyber espionage groups seeking to gain access to intellectual property and classified information.TIDRONE's







Leave a Reply