
A newly discovered Android malware named ‘SpyAgent' is stealing sensitive cryptocurrency credentials using advanced image recognition technology. The malware, discovered by McAfee's Mobile Research Team, targets mnemonic keys used to recover crypto wallets by scanning images on infected devices. These 12-word phrases serve as a more user-friendly alternative to traditional, complex private keys, making their theft a serious security risk.
The SpyAgent malware disguises itself as legitimate apps, including banking, government services, and utilities. Once installed, these fake apps access and steal users' text messages, contacts, and images, uploading them to remote servers controlled by cybercriminals.
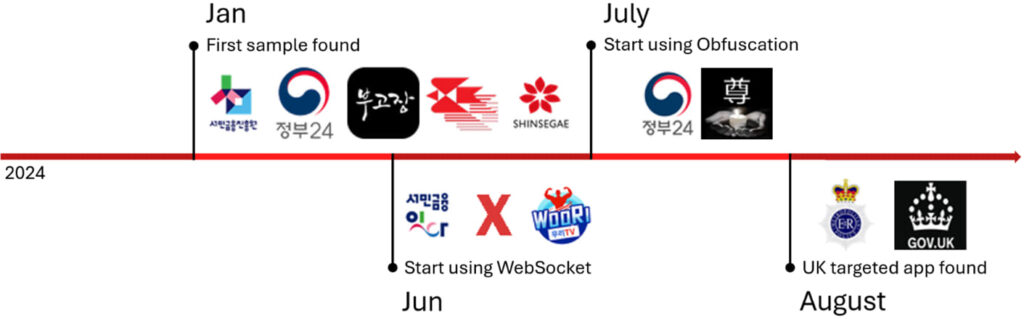
To avoid detection, these apps present deceptive loading screens and redirects, hiding their malicious activities. Since January 2024, McAfee has detected over 280 fake apps associated with this campaign, primarily targeting users in South Korea.
McAfee
A key aspect of this campaign involves the use of optical character recognition (OCR) technology to analyze stolen images for mnemonic keys. This method indicates the attackers' primary goal: to gain access to cryptocurrency wallets by extracting recovery phrases from the victims' images.
SpyAgent distribution
The malware propagates through phishing campaigns, typically via SMS or social media messages, which trick users into downloading malicious APK files. These messages often imitate trusted organizations, urging users to download fake apps that request sensitive permissions, such as access to contacts, SMS, and device storage. Once these permissions are granted, SpyAgent gains the ability to steal and transmit sensitive data to its command and control (C2) server.
McAfee's investigation revealed that the malware's primary focus is obtaining mnemonic recovery phrases for cryptocurrency wallets, allowing attackers to seize control of victims' crypto assets. The malware's activities are organized into several steps:
- Collects and sends the user's entire contact list to attackers, facilitating further phishing attacks.
- Incoming messages (SMS), which may contain two-factor authentication codes or other private data, are captured and transmitted.
- Photos, particularly those containing mnemonic keys or other sensitive information, are uploaded to the attackers' server.
- Collects information about the victim's device, such as the operating system version, which helps attackers refine their tactics.
Peeking into stolen data
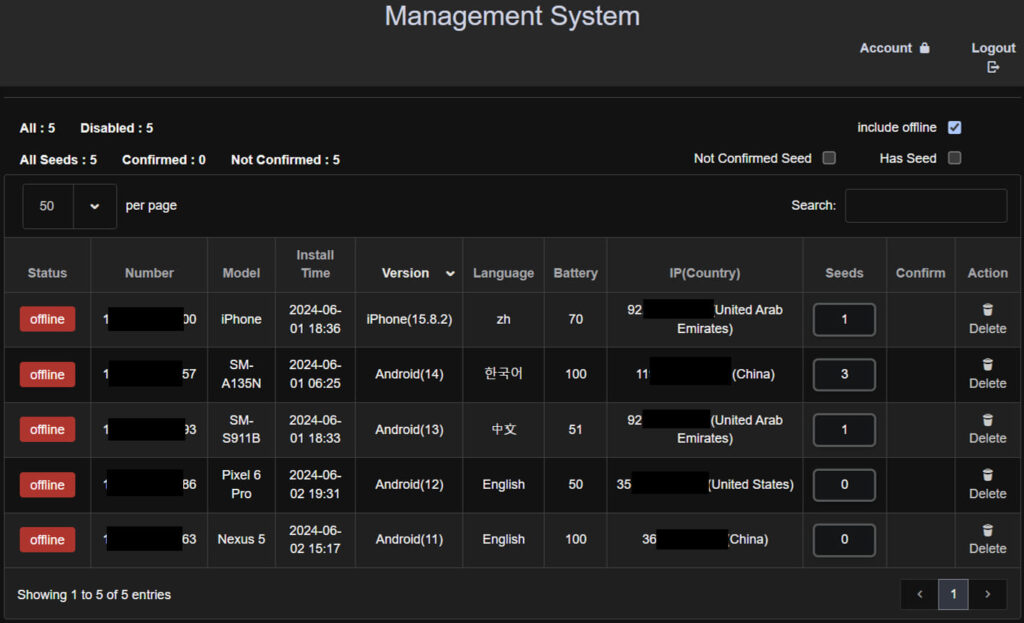
During their investigation, McAfee researchers uncovered serious security lapses in the C2 servers, which were improperly configured and left sensitive data exposed. These servers stored personal data gathered from victims, including photos in the “uploads” directory, organized by different malware campaigns. The servers also featured administrative panels displaying lists of compromised devices and their corresponding actions, including commands to change device settings or send SMS messages.
McAfee
Initially, SpyAgent relied on HTTP for communication with its C2 server, but it has since evolved to use WebSocket connections, making it harder for security tools to detect and intercept. The malware has also implemented complex obfuscation techniques, such as code encryption and the renaming of functions, which further complicates detection efforts.
The campaign, which began in South Korea, has expanded its reach, now targeting users in the UK. This geographic expansion, along with increasingly sophisticated phishing strategies, points to a growing and persistent threat.
Defense tips
To protect against SpyAgent and similar malware, users should take the following precautions:
- Be cautious of unsolicited messages urging you to download apps, especially those promising banking or government services.
- Only download apps from official platforms like the Google Play Store.
- Pay close attention to the permissions requested by apps. Be wary of apps asking for extensive access to personal data or device settings.
- Install reputable mobile security software, or use Google Play Protect to perform regular device scans.







Leave a Reply