
A cybercriminal operating under the alias “emirking” recently claimed to have access to 20 million OpenAI accounts, offering login credentials for sale on BreachForums.
However, a deeper investigation by cybersecurity firm KELA reveals that these credentials were not obtained from a breach of OpenAI’s systems but rather sourced from infostealer malware campaigns.
Alleged OpenAI breach
On February 9, 2025, emirking posted on BreachForums, stating that they had amassed over 20 million login credentials for OpenAI accounts. Their message, written in Russian (but seemingly auto-translated), implied that they had discovered a method to bypass OpenAI’s authentication process. They shared sample credentials allegedly linked to the subdomain auth0.openai.com, raising concerns that OpenAI’s authentication infrastructure might have been compromised.
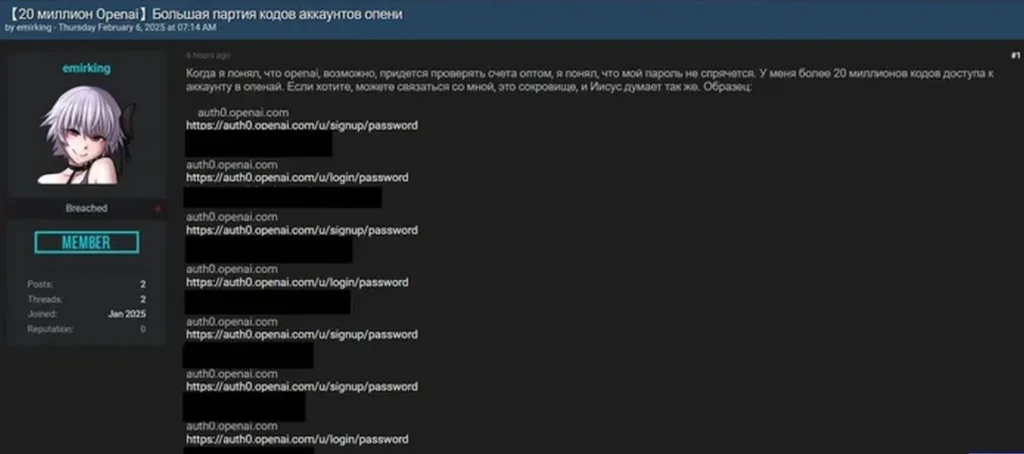
Malwarebytes
Cybersecurity analysts initially speculated that such a large dataset could have been obtained through either a direct breach or administrator credential theft. Given OpenAI’s widespread usage across enterprises and individual users, the potential impact of such a breach was alarming. The stolen credentials could allow attackers to access private user conversations or abuse OpenAI’s API services at the victims’ expense.
However, further scrutiny revealed discrepancies in the threat actor’s claims. KELA’s research team analyzed the samples emirking provided and cross-referenced them with a vast database of previously stolen credentials. Their findings indicated that all of the credentials emirking advertised were already present in records obtained from infostealer malware rather than a direct OpenAI breach.
Despite the alarming numbers cited by emirking, KELA’s findings confirm that OpenAI’s infrastructure has not been breached. Instead, the login credentials are a result of individual users falling victim to infostealer malware. Affected accounts were likely compromised due to weak personal security measures — such as reusing passwords across multiple services or failing to secure their devices against malware infections.
Moreover, other dark web users were skeptical of emirking’s claims. Some users who tested the credentials found that they did not grant access to ChatGPT conversations or any sensitive OpenAI data, suggesting that the leaked information was either outdated or incomplete. Shortly after these doubts surfaced, emirking’s post was deleted from BreachForums, further casting doubt on the credibility of the alleged breach.
Infostealer malware (again)
Infostealers are a prevalent form of malware that covertly extract login credentials, financial details, and other sensitive data from infected devices. Once compromised, the stolen data is either sold on cybercrime forums or incorporated into larger credential dumps. The OpenAI credentials emirking attempted to sell appear to be part of this broader ecosystem of stolen data.
KELA’s analysis identified multiple malware families responsible for the compromised credentials, including:
- RedLine – One of the most widely used infostealers, stealing browser-saved passwords and autofill data.
- Lumma – An emerging infostealer marketed as a Malware-as-a-Service (MaaS).
- StealC – A sophisticated credential harvester distributed through phishing campaigns.
- Vidar – A well-known infostealer that extracts passwords, cookies, and cryptocurrency wallet information.
The stolen credentials originated from 14 different sources, spanning private data leaks, underground marketplaces, and widely shared stolen credential repositories. Additionally, infection timestamps revealed that many credentials were stolen between October 2023 and July 2024, long before emirking’s post — further discrediting the claim of a recent OpenAI-specific breach.
Recommendations
While OpenAI’s systems remain secure, users must take precautions to protect their accounts from infostealer malware threats.
If you suspect your credentials may be compromised, update your OpenAI password immediately, avoid using the same password across multiple services, and enable multi-factor authentication (MFA) for an extra layer of security.
Cybercriminals often use stolen credentials to launch phishing campaigns, so you should remain cautious of emails or messages requesting your OpenAI login details.







Leave a Reply