
Microsoft Threat Intelligence has identified a security risk involving publicly available ASP.NET machine keys, which have been exploited in code injection attacks.
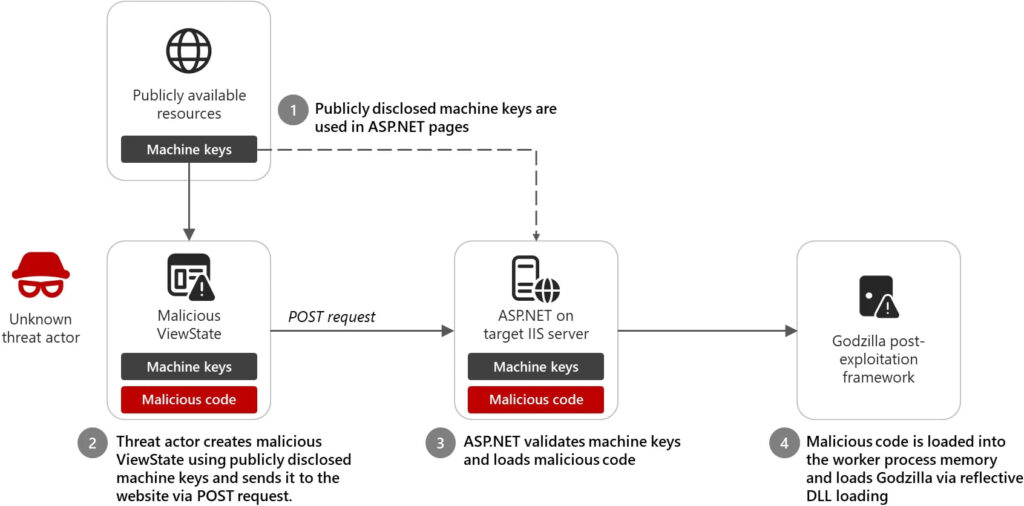
Microsoft’s security researchers observed limited malicious activity in December 2024, when a threat actor leveraged a publicly disclosed ASP.NET machine key to perform a ViewState code injection attack. During the investigation, Microsoft found that developers had embedded machine keys from publicly accessible sources — such as code documentation and online repositories — into their applications, inadvertently exposing their systems to attackers.
ViewState is a mechanism in ASP.NET Web Forms that maintains the state of web pages between user interactions. To protect this data, ValidationKey and DecryptionKey are used to sign and encrypt ViewState data. If these keys are compromised, attackers can craft a malicious ViewState payload, which, when processed by the ASP.NET runtime, executes arbitrary code on the target IIS web server.
Microsoft has since identified over 3,000 publicly exposed machine keys, warning that they pose a higher risk than stolen keys traded on dark web forums because they are widely accessible in public repositories and could have been unknowingly integrated into development environments.
Deployment of Godzilla Framework
The December attack used a known machine key to inject a malicious ViewState payload that reflectively loaded “assembly.dll.” This payload deployed Godzilla, a post-exploitation framework that allows attackers to execute arbitrary commands on the compromised system, inject shellcode into running processes, and maintain persistence on the target IIS web server.
Godzilla is a known webshell toolkit often used in targeted cyber intrusions, giving attackers full control over compromised servers.
Microsoft
Microsoft’s response and mitigation tips
Microsoft has taken several steps to mitigate the risks associated with publicly disclosed machine keys. First, Microsoft Defender for Endpoint now detects and alerts administrators about publicly disclosed machine keys in use. Secondly, Microsoft has removed key samples from its own documentation to discourage insecure practices. Finally, a GitHub repository has been provided with a list of hash values for exposed keys, along with a script to help organizations identify compromised machine keys in their environment.
Organizations running ASP.NET applications should take the following immediate actions:
- Check for publicly disclosed machine keys using Microsoft’s provided script.
- Rotate machine keys regularly to prevent unauthorized use.
- Avoid copying keys from public sources or documentation.
- Remove static machine keys from web.config files and allow ASP.NET to auto-generate secure keys.
- Encrypt sensitive data in web.config to prevent attackers from accessing plaintext secrets.
- Upgrade to ASP.NET 4.8 to enable Antimalware Scan Interface (AMSI) for enhanced protection.
- Monitor IIS logs for suspicious activity, including unusual access to web.config files.
While Microsoft observed only limited activity in December, the presence of thousands of exposed machine keys suggests that this technique could be widely adopted by threat actors in the future. Microsoft Threat Intelligence continues to monitor ViewState code injection attacks and urges organizations to adopt secure DevOps practices to prevent the misuse of machine keys.
Given the potential for remote code execution and server takeovers, affected organizations should immediately rotate compromised keys and conduct a thorough security audit of their web-facing infrastructure. If an attacker has exploited a disclosed key, simple key rotation may not be enough — organizations should consider reinstalling affected servers to eliminate persistent threats.







Leave a Reply