McAfee Labs has uncovered a network of malicious GitHub repositories masquerading as game hacks, cracked software, and cryptocurrency tools to distribute the Lumma Stealer malware. The cybercriminals behind these repositories frequently update them with new names and descriptions while maintaining the same malicious payload, ensuring continued infections despite GitHub’s takedown efforts.
Pirate software to malware
Attackers create repositories claiming to offer cheats for popular video games like Apex Legends, Minecraft, Counter-Strike 2, Valorant, Fortnite, Call of Duty, and GTA V. Others disguise themselves as cracked versions of premium software, including Spotify Premium, FL Studio, Adobe Express, SketchUp Pro, and Xbox Game Pass.
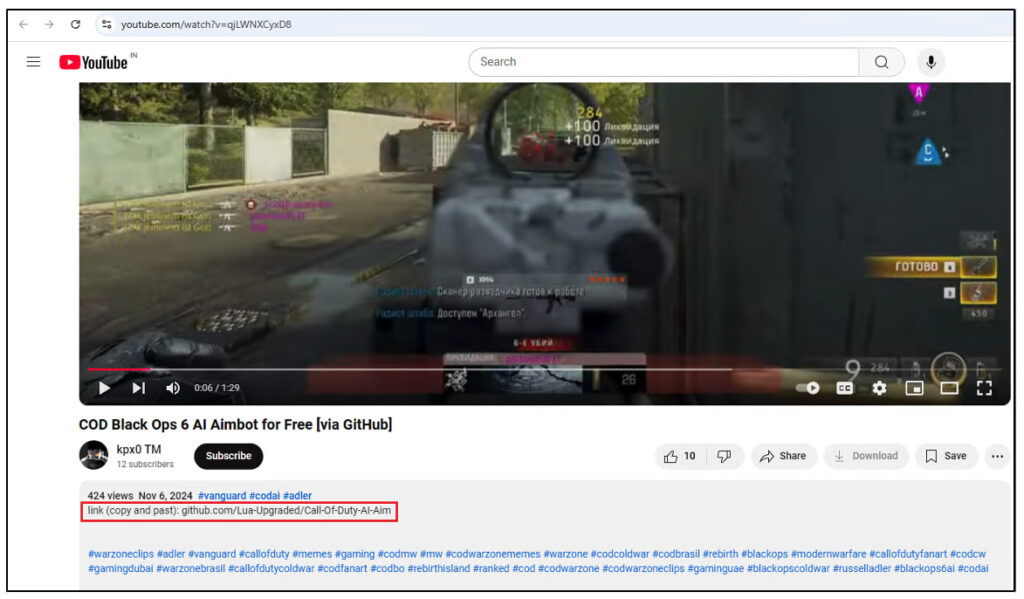
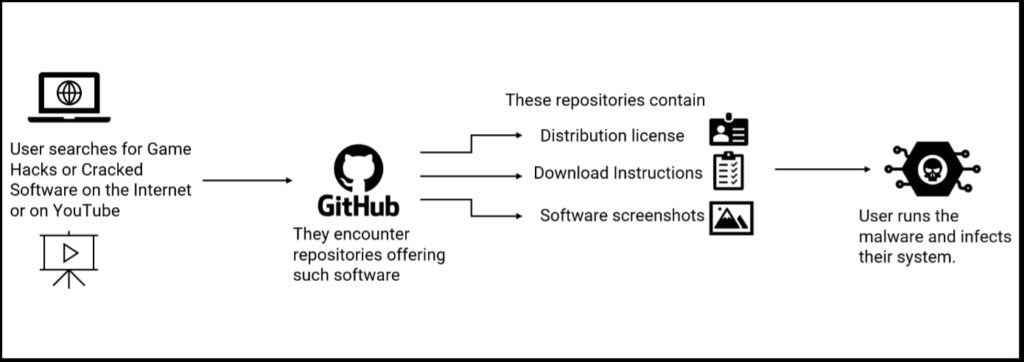
Victims typically encounter these repositories through internet searches or YouTube videos linking directly to them. The repositories appear legitimate, often containing software descriptions, distribution licenses, and installation instructions. However, the setup guides instruct users to disable Windows Defender and other antivirus software before downloading the malware, claiming it is necessary due to the software’s nature as a hack or bypass tool.
McAfee
Once downloaded, the malware — primarily variants of Lumma Stealer — exfiltrates sensitive information, including login credentials, cryptocurrency wallets, and stored passwords. The attackers regularly create new repositories to replace those that are taken down, ensuring a continuous infection cycle.
Upon execution, the downloaded files typically include a loader executable (Loader.exe). This file scans the system for credentials stored in browsers such as Google Chrome, Firefox, and Edge. It also searches for cryptocurrency wallets, extracting private keys and authentication data. After collecting the data, the malware establishes a connection with C2 (command-and-control) servers to transfer the stolen information.
McAfee researchers noted that while Lumma Stealer was the most common malware variant found, newer repositories have started delivering other malicious payloads as well.
McAfee
GitHub widely abused
GitHub, a widely trusted platform for developers, has been repeatedly exploited for malware distribution due to its open and accessible nature. Cybercriminals easily create new repositories, upload infected files, and leverage GitHub’s reputation to deceive unsuspecting users. Despite GitHub’s security measures, the attackers adapt quickly, replacing removed repositories with new ones under different names.
This abuse of GitHub is part of a broader trend where cybercriminals use legitimate platforms — such as cloud storage services and code repositories — to host and distribute malware while evading traditional detection mechanisms.
McAfee has taken steps to disrupt this malware campaign, including blocking URLs linked to malicious repositories and reporting them to GitHub for removal. However, many are still online at the time of writing this, so users must remain vigilant to avoid falling victim.
In general, it is recommended to avoid downloading cracked software or game cheats, as these are common vectors for malware. Verify the legitimacy of GitHub repositories before downloading any files. Legitimate projects often have detailed documentation, active discussions, and contributions from multiple developers.







Leave a Reply