
The first day of Pwn2Own Automotive 2025 saw security researchers successfully exploit multiple in-vehicle infotainment (IVI) systems and electric vehicle (EV) chargers, uncovering 16 previously unknown (zero-day) vulnerabilities. A total of $382,750 was awarded to participants, with researchers demonstrating exploits ranging from buffer overflows to OS command injection flaws.
Pwn2Own Automotive, hosted by Trend Micro’s Zero Day Initiative (ZDI), is a high-profile cybersecurity competition where researchers attempt to find and exploit vulnerabilities in automotive systems. This year’s event, held in Tokyo, features targets such as IVI systems from Alpine, Kenwood, and Sony, as well as EV chargers from Autel, ChargePoint, and Phoenix Contact.
Among the standout performances on Day One:
- PCAutomotive leveraged a stack-based buffer overflow to execute code on the Alpine IVI, earning $20,000 and two Master of Pwn points.
- Viettel Cyber Security exploited an OS command injection bug in the Kenwood IVI, securing $20,000 and two points.
- Cong Thanh (@ExLuck99) and Nam Dung (@greengrass19000) of ANHTUD used an integer overflow to attack the Sony XAV-AX8500 IVI, netting $20,000.
- Synacktiv combined a stack-based buffer overflow and an OCPP vulnerability to manipulate signals on a ChargePoint EV charger, earning $47,500 and 4.75 points.
- PHP Hooligans exploited a heap-based buffer overflow to attack an Autel charger, taking home $50,000 and five points.
- Sina Kheirkhah (@SinSinology) of Summoning Team used a hard-coded cryptographic key flaw to compromise a Ubiquiti charger, receiving $50,000 and five points.

ZDI
Not every attempt in Pwn2Own Day One was successful though, and some exploits faced collisions—instances where a vulnerability was already known. Sina Kheirkhah found a three-bug exploit for the Phoenix Contact CHARX SEC-3150 EV charger, but one bug was already public. He still earned $41,750 and 4.25 points. Similarly, SK Shieldus (@EQSTLab) attempted to exploit an OS command injection flaw in the Alpine IVI, only to discover it was the same vulnerability demonstrated last year—one that Alpine did not patch, citing ISO21434 compliance. This resulted in a reduced reward of $5,000 and one point.
At the end of Day One, Tobias Scharnowski (@ScepticCtf), Felix Buchmann (@diff_fusion), and Kristian Covic (@SeTcbPrivilege) of fuzzware.io lead the Master of Pwn rankings, closely followed by Sina Kheirkhah (@SinSinology).
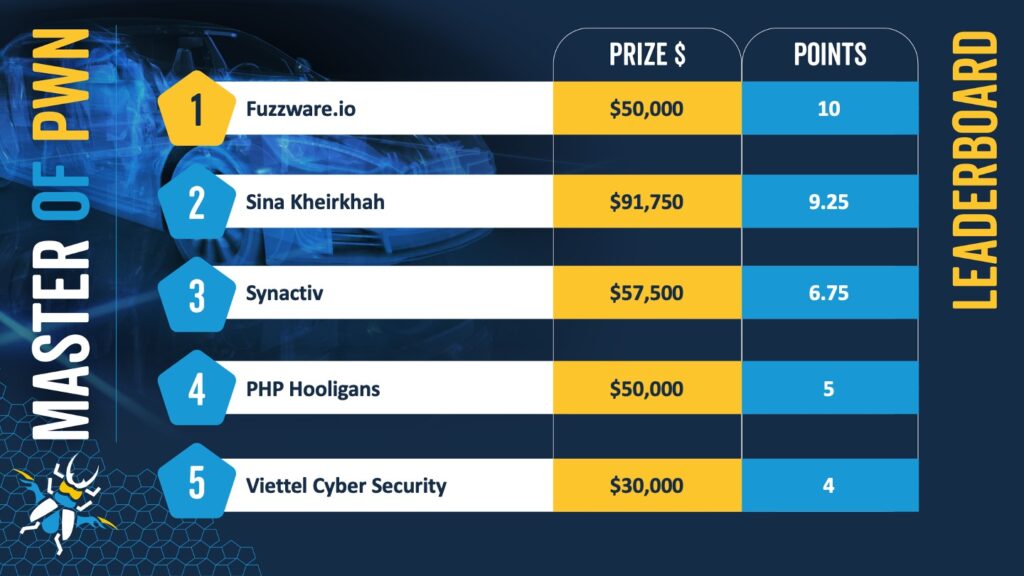
ZDI
Pwn2Own Automotive 2025 continues with more rounds in the following days, offering researchers additional opportunities to exploit vulnerabilities in automotive systems and EV chargers. The competition not only rewards ethical hackers but also plays a crucial role in identifying and fixing security flaws before malicious actors can exploit them.







Leave a Reply