
A 15-year-old security researcher, Daniel (@hackermondev), has disclosed a zero-click deanonymization attack capable of revealing a user's approximate location within a 250-mile radius. The attack exploits content delivery network (CDN) caching mechanisms, particularly Cloudflare's caching infrastructure, and affects widely used platforms such as Signal and Discord. Despite responsible disclosure, responses from affected companies have been mixed, with some dismissing the findings as out of scope.
Geolocating users without interaction
Daniel discovered the vulnerability three months ago while investigating Cloudflare's caching behavior. Cloudflare, a leading CDN provider with a presence in over 330 cities worldwide, caches frequently accessed content in geographically distributed data centers. By analyzing cache response headers, an attacker can determine which Cloudflare data center served a request — revealing the general location of a user.
Initially, Cloudflare's network design appeared to prevent targeted queries to specific data centers, as all inbound connections are handled by the nearest available node. However, Daniel found a workaround using a known but unpatched bug in Cloudflare Workers. By leveraging an internal IP range used by Cloudflare WARP, he developed Cloudflare Teleport, a tool that could direct requests to specific data centers. This allowed him to track where cached resources were being stored, effectively mapping a user's location based on their proximity to the caching nodes.
Cloudflare later patched the Teleport bug after Daniel's disclosure, but he demonstrated that the attack remains feasible using VPNs, which provide access to multiple Cloudflare data centers globally.
Real-world exploits: Signal and Discord
Daniel tested the attack on major applications that rely on Cloudflare's CDN infrastructure, revealing privacy risks for millions of users.
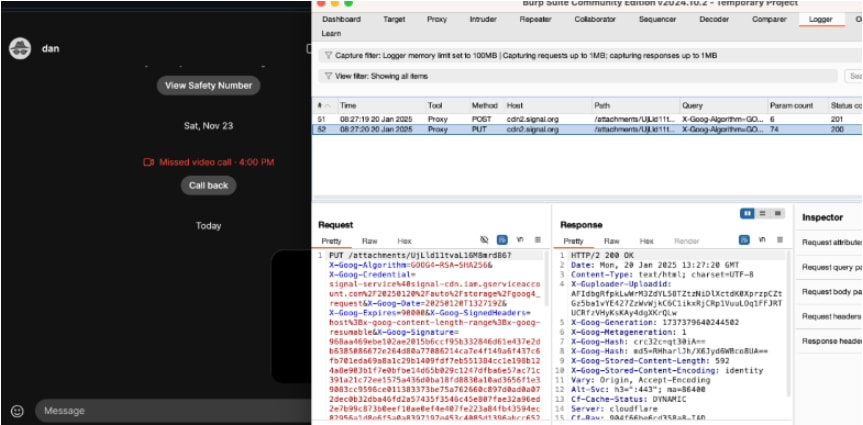
Signal, a widely used encrypted messaging service, hosts message attachments on Cloudflare-backed servers. When a user sends an attachment, the recipient's device automatically downloads it, triggering caching at a nearby data center. By monitoring cache responses, an attacker can infer the recipient's location.
Hackermondev | GitHub
Daniel further demonstrated a zero-click version of this attack using push notifications. Since Signal's mobile push notifications include attachments by default, a user's device downloads the image without requiring any interaction — silently exposing their location.
The same vulnerability was observed in Discord, a popular communication platform. Attackers can exploit Discord's CDN caching to track users who view custom emojis, profile pictures, or even friend requests.
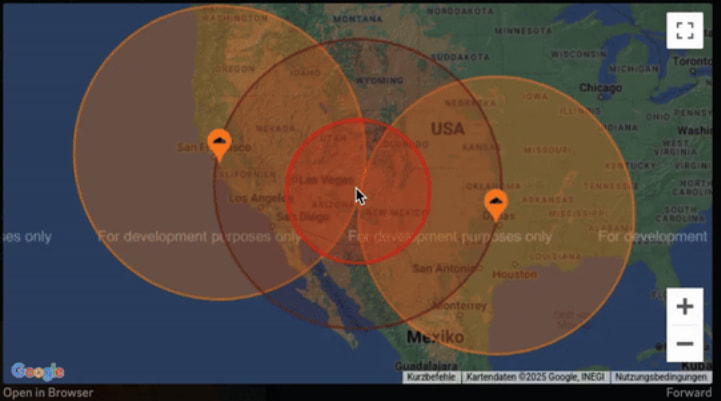
The researcher automated the attack with a custom Discord bot, GeoGuesser, which initiates friend requests and then analyzes CDN cache behavior to approximate the target's location. He successfully tested this on Discord's Chief Technology Officer, Stanislav Vishnevskiy, identifying his general location within minutes.
Hackermondev | GitHub
Responses and mitigation
Daniel reported the issue to Signal, Discord, and Cloudflare, receiving mixed responses:
- Signal dismissed the report, stating that network-layer anonymity was outside their security model.
- Discord initially acknowledged the issue but later attributed it to Cloudflare, declining to take direct action.
- Cloudflare patched the Teleport bug but stated that preventing deanonymization attacks is the responsibility of application developers. They awarded Daniel a $200 bug bounty for his report.
Despite Cloudflare's fix, Daniel demonstrated that attackers could still achieve similar results using VPNs, suggesting that the fundamental issue remains unresolved.
Users concerned about privacy, particularly journalists and activists who might be at greater tracking risk, should consider disabling push notifications and using VPNs to mask their actual IP address and location.







Leave a Reply