
A newly identified Adversary-in-the-Middle (AiTM) phishing kit, dubbed Sneaky 2FA, is being distributed as a Phishing-as-a-Service (PhaaS) operation on Telegram, enabling cybercriminals to bypass multi-factor authentication (MFA) protections for Microsoft 365 accounts. Sekoia’s Threat Detection & Research (TDR) team discovered the phishing kit in December 2024 during routine threat-hunting activities and has since linked it to a service called Sneaky Log.
Sekoia researchers identified Sneaky 2FA in active phishing campaigns running since at least October 2024. The kit operates as an AiTM attack, intercepting authentication tokens instead of simply capturing login credentials, allowing attackers to hijack active sessions without needing the victim’s password or second-factor authentication code.
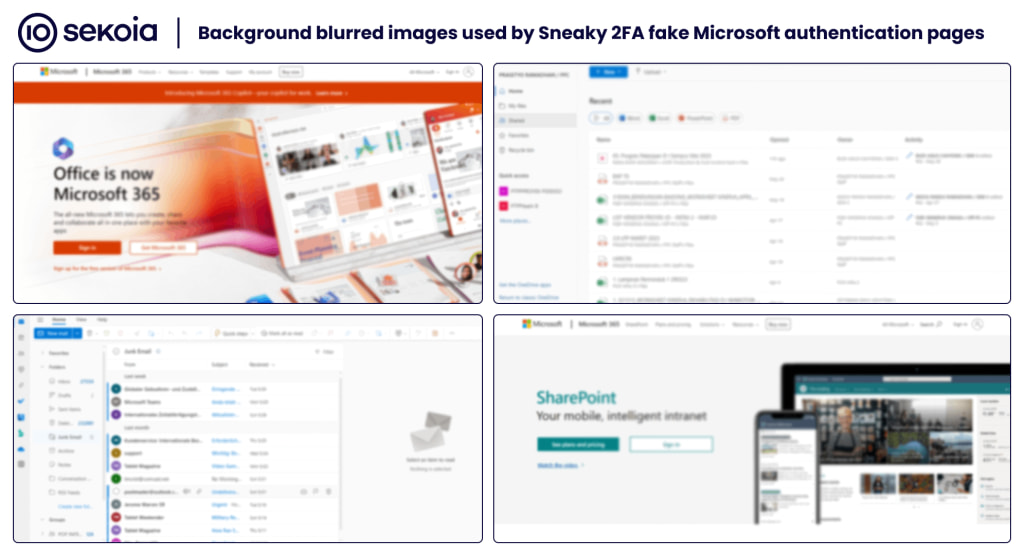
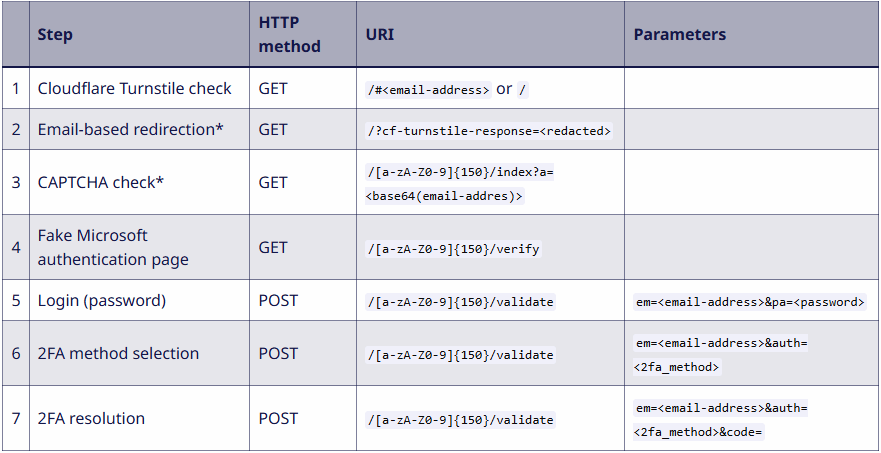
The phishing kit is distributed as a licensed product, with customers purchasing an obfuscated version of the source code for independent deployment. Hosted primarily on compromised WordPress websites and attacker-controlled domains, Sneaky 2FA presents fake Microsoft 365 authentication pages to victims. The phishing URLs follow distinct patterns, often including 150-character alphanumeric strings appended with paths like /index, /verify, or /validate, making them trackable for defenders.
Sekoia
Notably, the leaked source code obtained by Sekoia revealed similarities to W3LL Panel OV6, another AiTM phishing kit linked to business email compromise (BEC) operations, previously reported by Group-IB in 2023. This suggests that Sneaky 2FA may be an evolution or derivative of W3LL OV6.
Sneaky and evasive
Sneaky 2FA incorporates several techniques to evade detection:
- Anti-bot measures: Uses Cloudflare Turnstile CAPTCHA to filter out automated security scans.
- Traffic filtering: Redirects visitors from suspicious IPs (such as VPNs, proxies, or data centers) to Microsoft-related Wikipedia pages.
- HTML and JavaScript obfuscation: Scrambles code to avoid detection by security tools.
- Anti-debugging features: Blocks browser developer tools to prevent manual analysis.
Additionally, the phishing kit manipulates User-Agent strings inconsistently during authentication, allowing defenders to detect anomalous login behaviors—a method dubbed impossible device shift detection.
Sekoia
The Sneaky Log PhaaS operates a dedicated bot on Telegram, facilitating sales and customer support. The bot offers phishing tools, including ‘365 Cookie Page' for grabbing session cookies, ‘B2B Sender' for spamming phishing emails, and ‘Redirect & Attachment' for phishing link delivery.
Subscriptions for Sneaky 2FA start at $200 per month, with discounts for longer commitments, making it competitively priced against similar kits like Tycoon 2FA and Mamba 2FA.
The service supports cryptocurrency transactions in Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), and Tether (USDT), employing transaction obfuscation techniques to conceal payment flows. Blockchain analysis suggests the possible use of a laundering service, as payments require a 10% overcharge, with further deductions applied in follow-up transfers.
The best way to defend against AiTM attacks from the various phishing kits cybercriminals use is to adopt phishing-resistant MFA methods such as FIDO2-based authentication.







Leave a Reply