
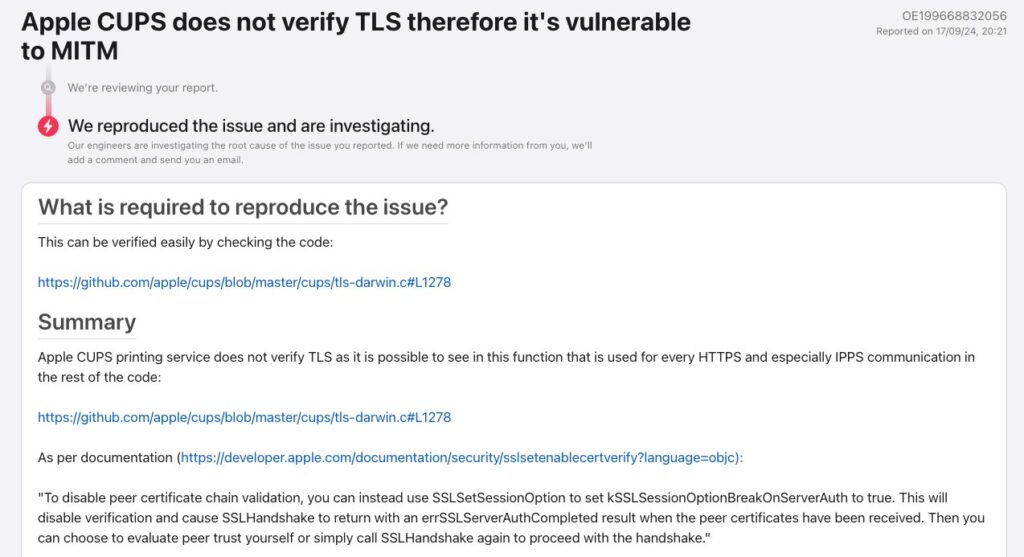
Security researcher Simone Margaritelli has publicly disclosed a critical vulnerability in Apple’s Common UNIX Printing System (CUPS), revealing that the service fails to verify TLS certificates. This flaw allows attackers on the same network to impersonate IPP-over-HTTPS (IPPS) printers and intercept, modify, or redirect print jobs — potentially exposing sensitive data and enabling broader system compromise.
Margaritelli, known for his previous high-impact CUPS discoveries, first reported the issue to Apple 121 days ago but received no response or patch. Frustrated by the lack of action, he published a full disclosure on X.
@evilsocket
The vulnerability stems from how CUPS, when paired with Apple’s Bonjour discovery service, automatically and silently trusts network printers without proper authentication. By broadcasting spoofed Bonjour advertisements, an attacker can force macOS to connect to a malicious host—whether on the local network or an external server — bypassing security measures.
CUPS is an open-source printing system used widely across macOS and Linux distributions. Originally developed by Michael Sweet in 1997 and later acquired by Apple in 2007, it remains the default printing backend for UNIX-based systems. Despite its ubiquity, CUPS has faced ongoing security challenges. Margaritelli previously uncovered a set of critical CUPS vulnerabilities enabling remote code execution (RCE) on Linux systems.
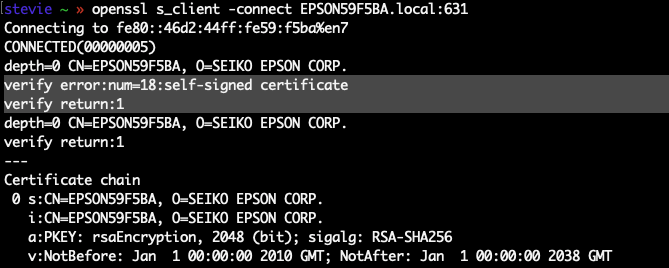
A key issue in the newly disclosed flaw is the widespread use of self-signed certificates by network printers. Without TLS verification, macOS devices accept these certificates without validation, making it trivial for attackers to exploit the flaw. Margaritelli noted that while Apple plans to transition to a “Trust On First Use” (TOFU) model, this approach remains susceptible to manipulation due to existing vulnerabilities in how trust is established.
@evilsocket
To demonstrate the severity of the attack, Margaritelli pointed to the ZeroGod module in Bettercap, a powerful network attack framework that he had previously developed. The module can automate the spoofing process, making exploitation relatively easy for attackers with access to a target’s network. While Apple has yet to respond with an official fix, the researcher has suggested that addressing this vulnerability without breaking backward compatibility will be a significant challenge.
While no official patch exists, users can take the following steps to mitigate the risk:
- Disable Bonjour Printer discovery to reduce network exposure.
- Manually configure printers with trusted certificates and disable IPPS where possible.
- Isolate printers on a separate VLAN to limit the attack surface.
- Employ intrusion detection systems (IDS) to flag unusual connections to unexpected hosts.







Leave a Reply