
Cybercriminals are running a large-scale phishing operation that exploits Google Ads itself to steal advertiser credentials. According to a new Malwarebytes report, the attackers create fraudulent ads that impersonate Google Ads, tricking businesses and individuals into entering their login details on fake Google pages. Stolen accounts are then resold on blackhat forums or used for various malicious activities.
Google Ads phishing scheme
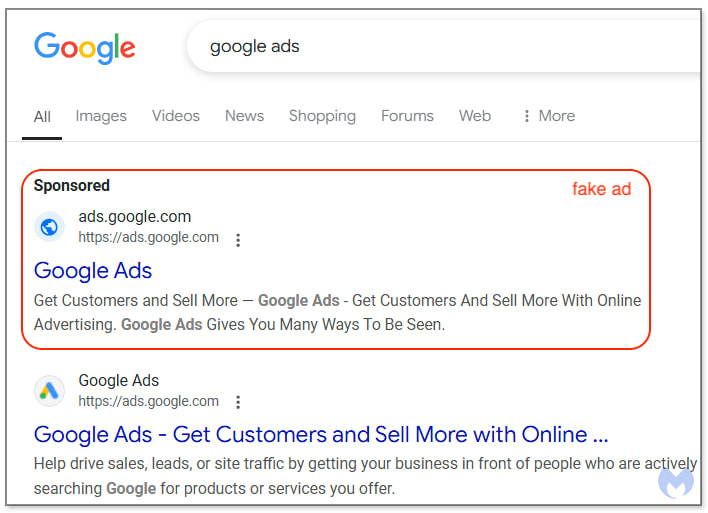
The campaign, which Malwarebytes describes as “the most egregious malvertising operation we have ever tracked,” works by placing deceptive ads for Google Ads on Google Search. These ads, which appear as “Sponsored” results, lead victims to counterfeit Google Ads login pages hosted on Google Sites. Once victims enter their credentials, attackers collect usernames, passwords, and other identifying information before taking control of the accounts.
Malwarebytes
Investigators first discovered the fraudulent ads while researching suspicious Google account activity. A deeper analysis revealed a global-scale phishing campaign, with fake ads appearing in multiple countries, including the U.S., Paraguay, Hong Kong, and Brazil. The compromised accounts — some belonging to legitimate businesses with active advertising campaigns — are then exploited to run additional fake ads, perpetuating the scam.
Malwarebytes
Here's how the attack works in simple steps:
- The attackers purchase Google Ads that mimic legitimate Google Ads sign-up and login pages.
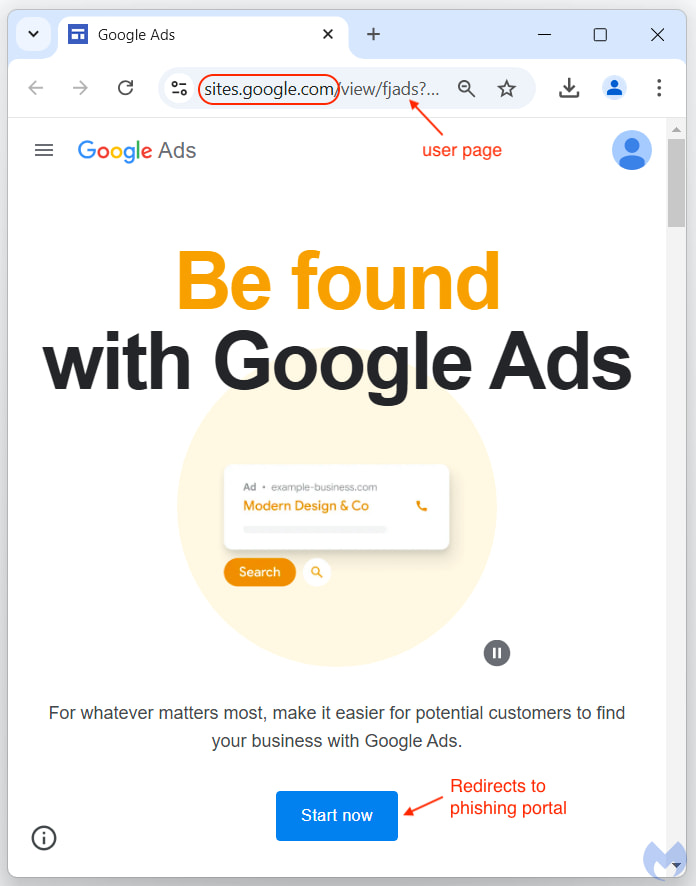
- Victims are directed to pages hosted on Google Sites, which appear authentic due to rules regarding the display of URLs on Google Ads.
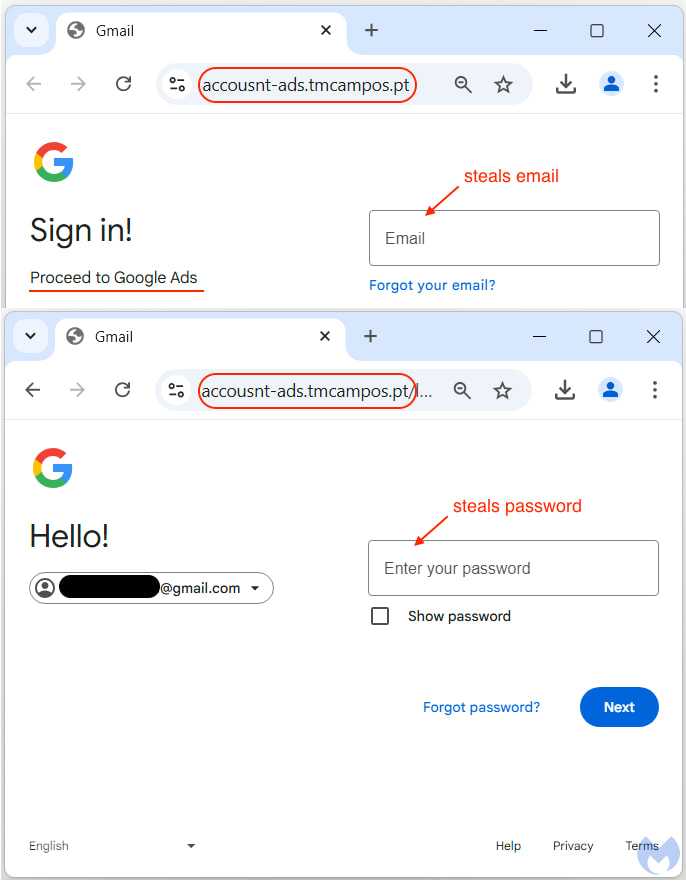
- Clicking “Start Now” on these pages redirects users to a phishing site that captures login details.
- If login attempts aren't blocked, attackers add their own administrator accounts and take control.
- Stolen accounts are used to push more fraudulent ads, distribute malware, or resell access on underground forums.
According to Malwarebytes, compromised advertisers may receive an email alerting them to an unusual login attempt, often from Brazil. However, these notifications frequently come too late, allowing attackers to hijack accounts and lock out the original owners.
Malwarebytes
Who's behind the campaign?
Malwarebytes identified at least two major threat actor groups involved, namely a Brazilian and an Asia-based group.
The former is the most prolific group, responsible for over 50 fraudulent ad campaigns. Their phishing kits include Portuguese-language code, and stolen accounts frequently show logins from Brazil.
The latter, likely operating from China or Hong Kong, uses a different phishing kit but employs similar tactics with fake Google Sites pages.
A third campaign, possibly linked to Eastern Europe, appears to have different objectives. Instead of stealing Google Ads accounts, it uses fake Google Authenticator ads to deliver malware through heavily obfuscated phishing pages.
Google's lackluster response
Despite reporting numerous fraudulent ads, Malwarebytes researchers found that at least one malicious ad remained active at all times. Google's policy states that compromised advertiser accounts should be frozen until their security is restored, but enforcement appears inconsistent. In one case, an account reported 30 times was still running fraudulent ads.
The misuse of stolen accounts fuels other malware and scam campaigns. Malicious advertisers use hijacked budgets to distribute harmful software, promote scams, or direct users to credential-stealing sites. This creates a cycle where criminals profit while legitimate advertisers suffer financial losses.
To avoid falling victim to these attacks, advertisers and businesses should always check that the URL for Google Ads starts with ads.google.com before entering login details, and use Google's Advanced Protection Program or 2FA to prevent unauthorized access even in the case of credential loss.
Additionally, it is recommended that Google account login locations are regularly reviewed and suspicious access is immediately revoked. While counterintuitive for advertisers, temporarily enabling an ad blocker can also help spot unusual sponsored results.







Leave a Reply