
A newly emerged threat actor named “Belsen Group” has publicly released sensitive configuration data and VPN credentials from over 15,000 FortiGate firewalls, affecting both governmental and private sector organizations worldwide. The data, which includes usernames, passwords, firewall rules, and digital certificates, was allegedly obtained through a 2022 Fortinet zero-day vulnerability (CVE-2022-40684) and has now been leaked for free on clearnet hacker forums and on the dark web.
15,000 VPN credentials exposed
The breach was initially reported by Kevin Beaumont, a cybersecurity researcher, who verified the authenticity of the leaked data. According to his findings, the leaked files are organized by country, with each entry containing:
- Full firewall configurations (config.conf)
- VPN user credentials (vpn-users.txt), some in plaintext
- Device management certificates
- Complete firewall rule sets
Beaumont confirmed that the leak includes real-world, identifiable devices, as cross-referenced with Shodan, an internet-scanning service. Many affected firewalls share unique serial numbers with those listed in the dump, validating the breach’s legitimacy.
The stolen data appears to have been originally exfiltrated in October 2022, coinciding with the active exploitation of CVE-2022-40684, a critical authentication bypass flaw in Fortinet’s FortiOS, FortiProxy, and FortiSwitchManager. At the time, Fortinet warned that attackers were actively abusing the zero-day to breach firewalls, but the full extent of the compromise remained unclear until now.
Even organizations that patched the vulnerability in late 2022 could still be at risk if their firewall configurations and credentials were stolen before mitigation. With the full device configurations now exposed, attackers can potentially reverse-engineer network security policies, exploit misconfigurations, and conduct targeted attacks.
Belsen Group profile
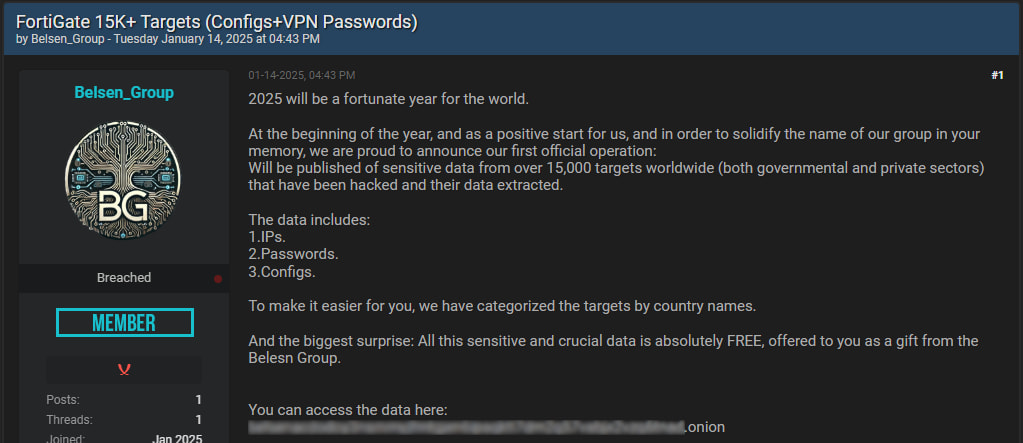
The Belsen Group, an unknown threat actor, announced the leak on BreachForums, a popular cybercrime marketplace. In their post, they describe the release as their “first official operation” and offer the stolen data for free.
This act raises concerns about potential follow-up attacks, as cybercriminals worldwide can now access highly sensitive firewall configurations without any financial barrier.
Security measures
Organizations using FortiGate firewalls should immediately assess their exposure and take the following steps:
- Check if your firewall's IP address is in the leaked data (once security researchers publish a verified list).
- Change all administrative passwords and VPN credentials on affected devices.
- Reissue digital certificates if any were exposed in the dump.
- Review and update firewall rules to mitigate risks from leaked configurations.
- Monitor for suspicious activity related to FortiGate devices and VPN access.
- Apply Fortinet’s latest patches and security advisories to ensure all vulnerabilities are mitigated.







Leave a Reply