
Ivanti has disclosed a critical zero-day vulnerability (CVE-2025-0282) actively exploited in the wild, affecting Ivanti Connect Secure (ICS) VPN appliances. The flaw, a stack-based buffer overflow, allows unauthenticated remote code execution, potentially compromising entire network infrastructures. Ivanti has released a patch and strongly advises immediate updates to ICS version 22.7R2.5 or higher. The advisory also details a high-severity vulnerability (CVE-2025-0283), which enables privilege escalation but is not currently exploited.
Ivanti, in collaboration with cybersecurity firm Mandiant, disclosed the critical vulnerability yesterday following investigations that began in mid-December 2024. The attacks utilize repeated HTTP requests to specific appliance endpoints to determine software versions before deploying an exploit. Compromised systems were infected by various malware including PHASEJAM, SPAWNMOLE, and DRYHOOK. Exploitation involves disabling security features like SELinux, deploying web shells, and tampering with system logs to evade detection.
The two flaws are summarized as follows:
- CVE-2025-0282: A stack-based buffer overflow leading to remote code execution. (CVSS 9.0 – Critical)
- CVE-2025-0283: Privilege escalation via a stack-based buffer overflow. (CVSS 7.0 – High)
Mandiant has attributed some activity to UNC5337, a suspected Chinese-nexus cyber espionage group, but notes that other threat actors may also be involved.
Affected products and impact
The vulnerabilities affect the following Ivanti products:
- Ivanti Connect Secure: versions 22.7R2 through 22.7R2.4
- Ivanti Policy Secure: versions 22.7R1 through 22.7R1.2
- Ivanti Neurons for ZTA Gateways: versions 22.7R2 through 22.7R2.3
Ivanti is a Utah-based IT software provider specializing in endpoint and network security solutions used by government and enterprise organizations globally. The active exploitation of its VPN appliances highlights the significant threat to remote access solutions, often targeted due to their role as gateways to internal networks.
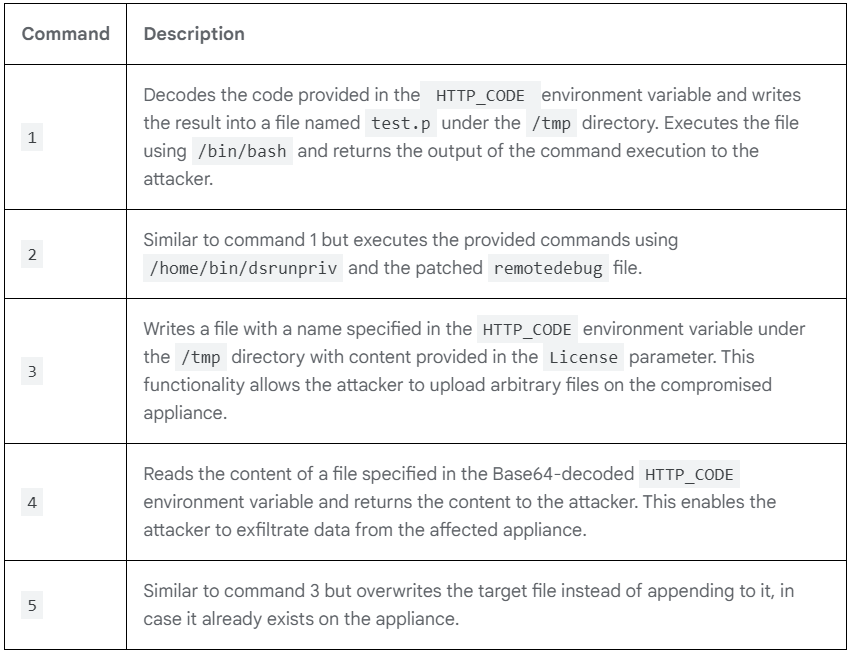
Mandiant identified several malicious tools deployed during exploitation, including:
- PHASEJAM: A dropper modifying ICS components to include web shells.
- SPAWNMOLE: A tunneler facilitating communication with command-and-control infrastructure.
- DRYHOOK: A credential-stealing script altering authentication processes.
Mandiant
Attackers used anti-forensic techniques, including clearing system logs and state dumps, modifying the integrity checker manifest to evade detection, and faking system upgrades to maintain persistence on compromised devices.
Defense recommendations
- Patch now: Upgrade Ivanti Connect Secure to version 22.7R2.5 or later. Patches for Ivanti Policy Secure and Neurons for ZTA Gateways are expected by January 21, 2025.
- Run Integrity Checker Tool (ICT): Use Ivanti's ICT to detect potential compromise. If signs of compromise are found, perform a factory reset and reinitialize devices with the latest software version.
- Audit Logs and network activity: Monitor for unusual activity, including repeated HTTP requests to specific appliance endpoints or blocked syslog forwarding. Look for IoCs, such as web shell deployments in /dana-na/auth/ directories.
- Enhance monitoring: Employ intrusion detection systems (IDS) and endpoint detection and response (EDR) solutions to identify post-exploitation behavior. Monitor for unusual LDAP queries and lateral movement.
The Cybersecurity and Infrastructure Security Agency (CISA) has added CVE-2025-0282 to its Known Exploited Vulnerabilities (KEV) catalog, setting a deadline for applying mitigations to January 15, 2025.






Leave a Reply