
Hackers claim to have breached Gravy Analytics, a major player in the collection and sale of smartphone location data. The attackers allege they have stolen sensitive data, including customer lists, industry insights, and precise location data tied to individuals’ smartphone movements. The breach is poised to have far-reaching consequences as the hackers threaten to publicly release the stolen data.
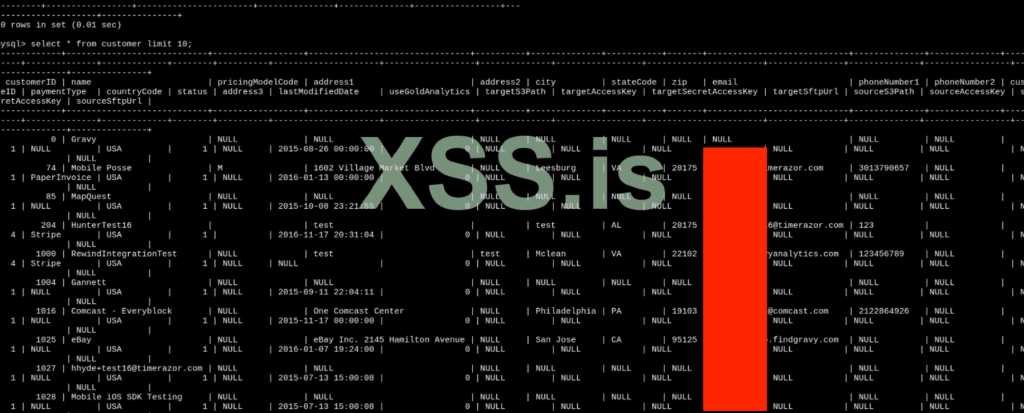
Gravy Analytics, based in Virginia, is well-known for its subsidiary Venntel, which has sold location data to U.S. government entities, including the Department of Homeland Security (DHS) and the FBI. The stolen data reportedly includes smartphone geolocation information, classified files like “LIKELY_DRIVING” behavior tags, and client lists of prominent companies such as Uber, Apple, and LexisNexis. Affected regions include diverse locations such as North Korea, Mexico, and the U.S., highlighting the global reach of Gravy’s data operations.
The hackers shared screenshots on the Russian cybercrime forum XSS, first spotted by 404media, suggesting access to Gravy’s critical infrastructure, including:
- Root access to an Ubuntu server.
- Control over Gravy’s domains.
- Amazon S3 buckets, commonly used for storing large volumes of data.
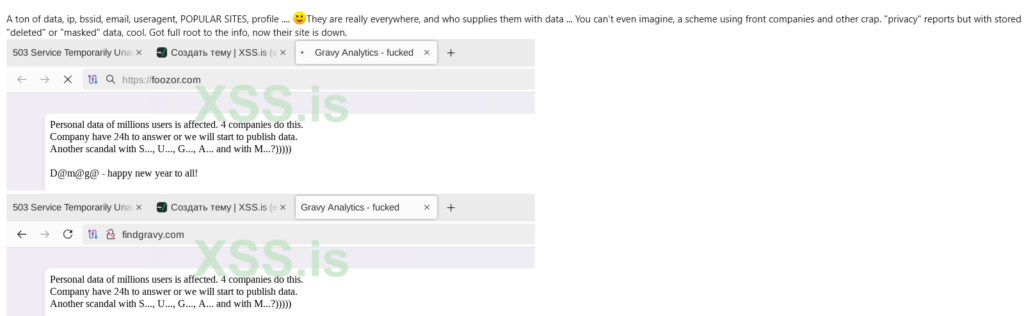
The leaked samples revealed precise historical location data, with latitude, longitude, and timestamps that could deanonymize users’ movements. A message from the hackers on Gravy’s websites warned, “Personal data of millions of users is affected,” and threatened to begin publishing data unless the company responded within 24 hours. The hackers also claimed to have had access to Gravy’s systems since 2018.
Previous FTC action
This breach comes just weeks after the Federal Trade Commission (FTC) announced a proposed settlement against Gravy Analytics and Venntel, banning them from selling sensitive location data and demanding the deletion of all historical data collected without user consent. The FTC alleged that the companies violated privacy laws by harvesting data via third-party suppliers and selling it without verifying user consent.
Gravy’s data practices have long drawn scrutiny due to their potential for misuse. Past reporting revealed the company’s tools were used to track visitors to abortion clinics and other sensitive locations, raising privacy and security concerns. Zach Edwards, a senior threat analyst at Silent Push, described this breach as “a nightmare scenario,” emphasizing the risks to high-risk individuals, government workers, and organizations.
The latest breach raises critical concerns about the location data industry’s security practices. If the data is published or sold on underground markets, it could expose individuals to deanonymization, tracking, and targeting. Sensitive information, such as a user’s visits to medical clinics or places of worship, could be exploited, threatening privacy and safety.







Leave a Reply