
The popular gaming platform Steam experienced a severe DDoS (Distributed Denial of Service) attack on August 24, 2024, coinciding with the launch of the highly anticipated game “Black Myth: Wukong.”
The attack, which targeted Steam servers across multiple regions, caused widespread disruption, leaving millions of gamers unable to access the platform. While initially speculated to be due to an overwhelming number of players, further analysis by XLab revealed that the outage was the result of a coordinated cyber assault.
Incident overview and initial reactions
On the evening of August 24, reports began flooding in from players around the world who were unable to log into Steam. The timing of the outage, closely aligned with the release of “Black Myth: Wukong,” led many to believe that the servers had simply been overwhelmed by the influx of players. However, an announcement by the Perfect World esports platform, which manages Steam's operations in China, clarified that the real cause was a massive DDoS attack.
XLab's analysis
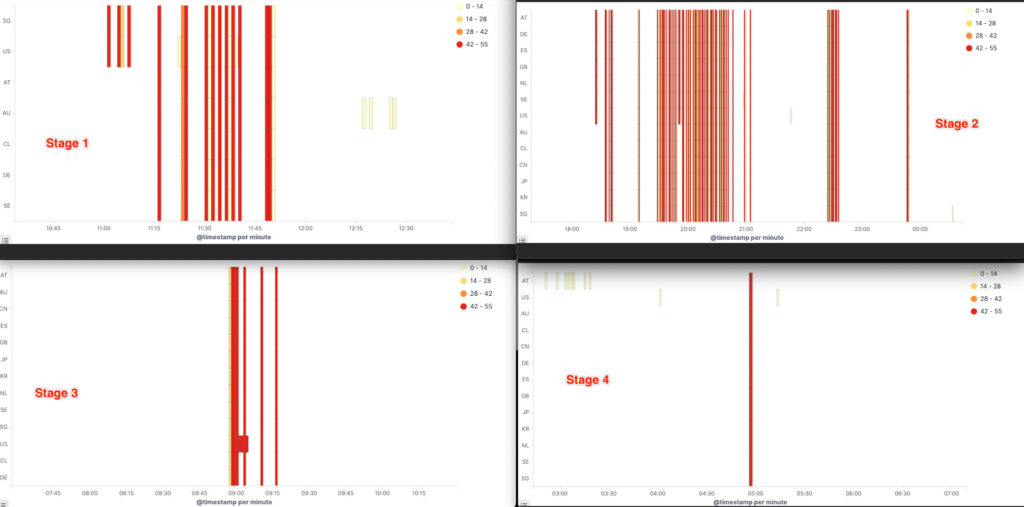
XLab, a cybersecurity research group, conducted an in-depth investigation into the attack, revealing that it was far more extensive than typical DDoS incidents. The assault was orchestrated using approximately 60 botnet control nodes, significantly more than what is commonly observed in such attacks. These nodes managed a large number of infected devices, directing them to flood Steam's servers with traffic in coordinated waves.
XLab
The attack targeted Steam servers in 13 regions worldwide, including China, the United States, the United Kingdom, and Japan. A total of 107 server IPs were affected, including those managed by Perfect World in China. The attackers strategically timed their waves to coincide with peak gaming hours in different time zones, maximizing the impact by disrupting services when the platform was most heavily used.
Potential motives
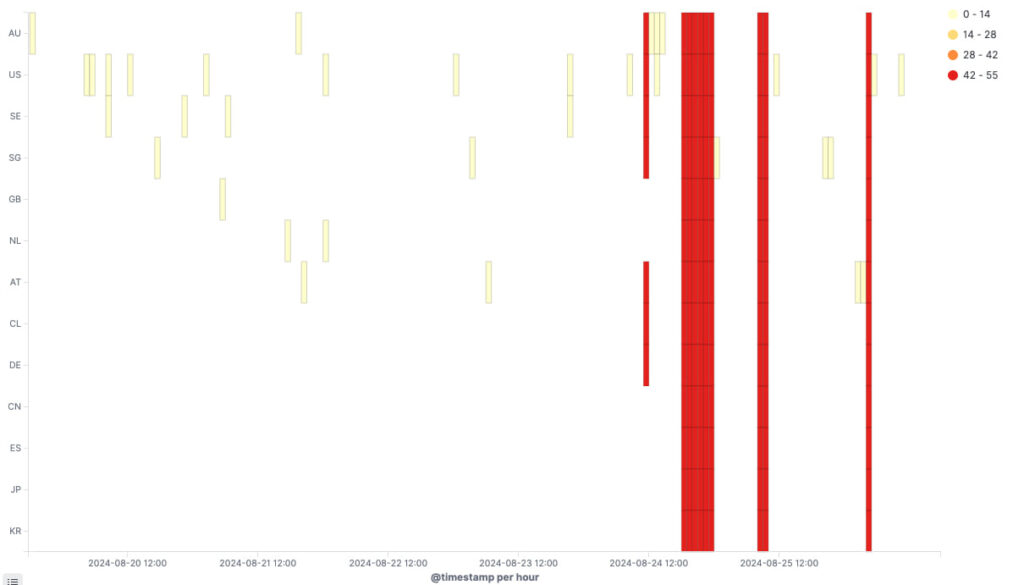
The sheer scale and timing of the attack have led to speculation about its motives. XLab observed a significant increase in attack commands directed at Steam—spiking to over 250,000, a number that dwarfs the typical few hundred commands usually seen in DDoS attempts.
XLab
The deliberate timing, targeting multiple global regions during their peak usage periods, suggests a calculated effort to disrupt the platform's operations, particularly in China. This has led to speculation that the attack may have been linked to the launch of “Black Myth: Wukong,” a game that has garnered significant attention both domestically and internationally.
AISURU botnet
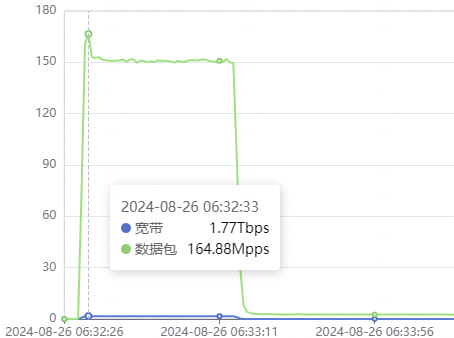
One of the main botnets identified in the attack was the AISURU botnet, which claimed responsibility via a Telegram channel. AISURU reportedly has over 30,000 bot nodes with a combined attack capacity of 1.3 to 2 terabits per second, making it a formidable force in the cyber landscape. The botnet's operators have a history of taunting security companies, often leaving messages within their malware samples to provoke a response and gain notoriety.
XLab
AISURU's tactics and infrastructure appear to be heavily influenced by the infamous Fodcha botnet, known for its role in high-profile DDoS attacks. AISURU employs similar techniques, such as using switch-case structures in its code and mapping its command-and-control (C2) servers across multiple countries to complicate takedown efforts.
Impact on Steam and players
Steam, operated by Valve Corporation, is one of the world's largest digital distribution platforms for video games, serving millions of users globally. The disruption caused by this DDoS attack not only affected gamers' ability to access their purchased games and content but also damaged the platform's reputation during a critical period of high traffic driven by the release of “Black Myth: Wukong.”







Someone said they were first sooo……..
First!