
A report by Intrinsec sheds light on the growing cybercrime market for Extended Validation (EV) code signing certificates, revealing how threat actors are leveraging these certificates to deploy malware and bypass security measures.
The detailed analysis uncovers the methods by which these criminals obtain, sell, and exploit EV certificates, often with devastating consequences for cybersecurity.
Code signing and the cybercrime market
Code signing technology is integral to software security, allowing developers to attach digital signatures to their code, thereby ensuring its authenticity and integrity. However, this technology has become a double-edged sword.
Cybercriminals have found ways to exploit code signing to distribute malware while evading detection. By using legitimate-looking certificates, attackers can bypass security systems like Microsoft SmartScreen, gain administrative privileges, and lower the risk of antivirus detection.
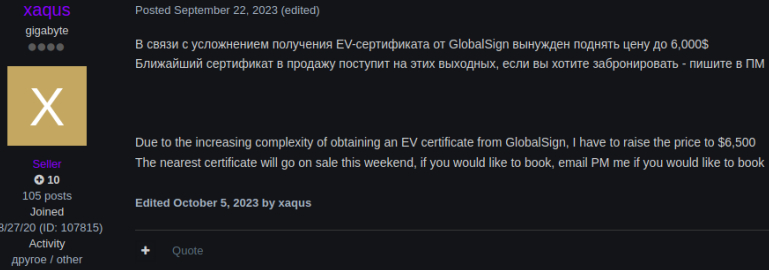
The market for EV certificates in the cybercrime underworld is particularly lucrative. These certificates, which require thorough validation of a company's legal and operational status, are sold for prices ranging from $2,000 to $6,500 on underground forums.
Intrinsec
The demand for such certificates is driven by their ability to enhance the perceived legitimacy of malicious software, making them a valuable tool for cybercriminals, explains Intrinsec in its report.
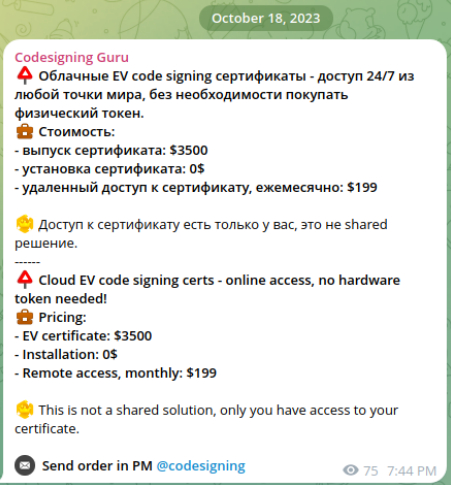
For those looking to obtain a certificate quickly, some sellers can expedite the process, delivering certificates in as little as 2-5 days. Others might take up to two weeks, depending on the complexity of the registration process and the rigor of the certificate authority’s checks. The choice of certificate authority is also a key consideration, with options including well-known CAs such as GlobalSign, Sectigo, SSL.com, Entrust, and Comodo.
Intrinsec
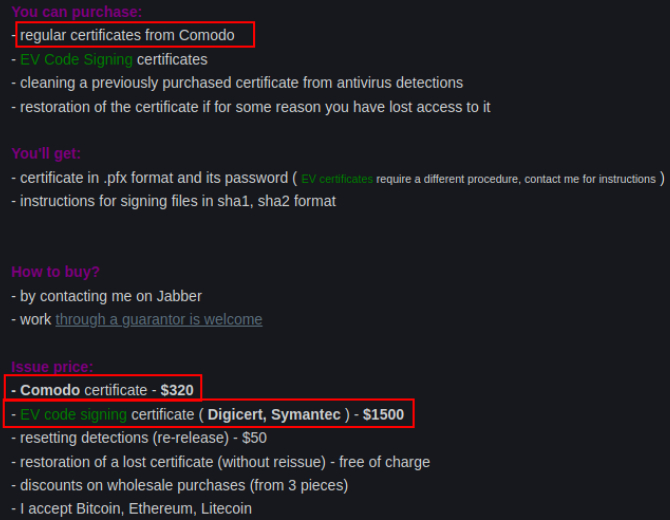
The method by which the customer accesses the certificate’s key pair is another significant factor in the transaction. Some sellers offer cloud signing services, where the malicious code is uploaded to the CA’s website for signing. However, this method is less popular among criminals because the files are often scanned by antivirus software during the upload process, increasing the risk of detection.
Intrinsec
For more secure access, many sellers provide physical tokens, such as USB keys, that store the certificate’s private key. These tokens are often delivered via private courier, and some services even offer remote access to the physical token through “USB over network” technologies. This allows the certificate to be used without direct physical access to the token, adding another layer of operational security for the criminals.
Malware campaigns fueling the crime
Several malware campaigns have been linked to the misuse of EV certificates. For example, the notorious QakBot malware, which resurfaced in December 2023, was distributed using an EV certificate issued by SSL.com. The certificate was associated with a company named “SOFTWARE AGILITY LIMITED,” registered in the UK in 2013. Although the certificate has since been revoked, the incident highlights the potential for attackers to either spoof legitimate companies or create shell companies to obtain these valuable certificates.
Another notable case involves the Grandoreiro banking trojan, which has been active in South America since 2019. In May 2024, Grandoreiro was found using an EV certificate belonging to “MR Software GmbH,” a company that had been closed since June 2023. This suggests that the attackers took advantage of the company's closure to impersonate it and obtain a valid certificate.
A timely Sophos report about the Poortry malware, which emerged in mid-2024, provides another striking example. Poortry was found using a legitimate EV code signing certificate issued by Sectigo. The certificate was registered under the name of a real company but had been misappropriated by the attackers, allowing them to distribute Poortry as a seemingly legitimate application. This incident underscores the lengths to which cybercriminals will go to obtain and misuse these certificates, further complicating efforts to detect and prevent malware distribution.
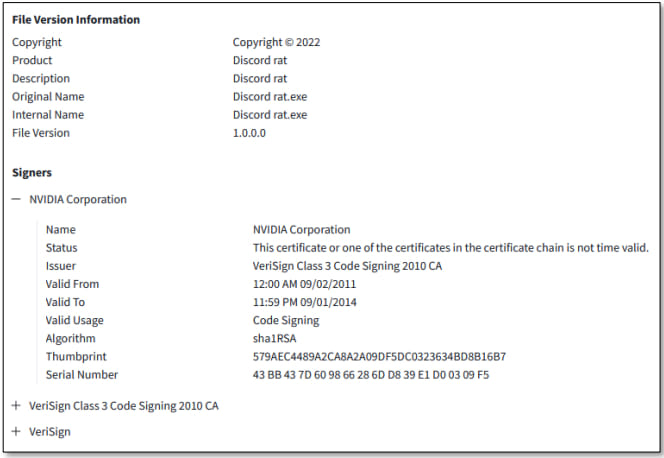
Stolen certificates also pose a significant threat. The Lapsus$ group, which targeted NVIDIA in early 2022, managed to steal two code-signing certificates. These certificates were later used to sign malware, such as the Discord RAT, allowing the attackers to distribute their malicious software with apparent legitimacy.
Intrinsec
Defense recommendations
To mitigate the risks associated with malicious code signing, Intrinsec provides several recommendations:
- Implement stringent allowlisting and blocklisting of application vendors to ensure only trusted sources are allowed.
- Conduct comprehensive validation of certificates, including checks for revocation status and chain of trust.
- Train staff to recognize unsigned or suspiciously signed code is crucial in preventing malware infections.
- Regularly check for revoked certificates to prevent the use of compromised keys.
- Employ reputation-based threat intelligence to identify and block malicious certificates.
- Isolate unknown executables in secure environments to observe their behavior before allowing full access.






Leave a Reply