Morphisec highlights the evolution of fake update campaigns and the emergence of CoinLurker—a powerful information stealer written in Go. CoinLurker uses advanced evasion techniques, including in-memory execution, multi-stage obfuscation, and reliance on trusted platforms, making it a formidable threat to individuals and organizations.
Fake Update campaigns and delivery tactics
CoinLurker builds on the deceptive strategies pioneered by campaigns like SocGolish, ClearFake, and FakeCAPTCHA. These fake update schemes manipulate user trust, presenting prompts for seemingly routine updates. The infection typically begins through multiple entry points, such as fake software update notifications on compromised WordPress sites, phishing emails linking to spoofed update pages, and malicious ads that redirect users to fake updates or CAPTCHA windows. Additionally, attackers leverage social media and messaging links, which often lead to disguised verification pages hosting malware.
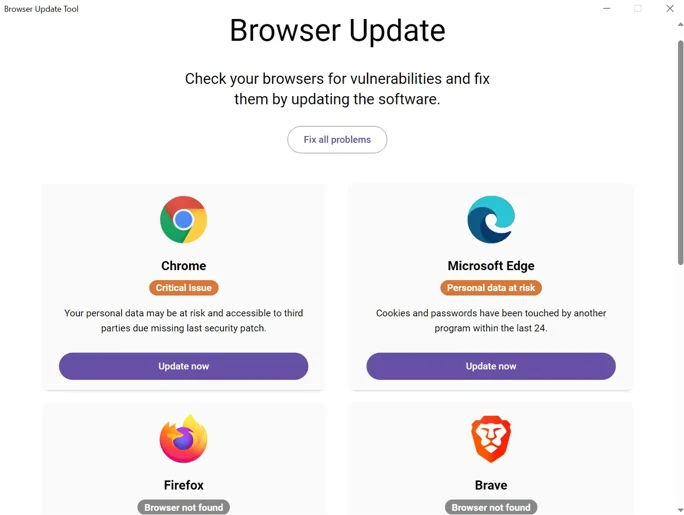
Morphisec
To further obfuscate its execution, CoinLurker uses Microsoft Edge Webview2, a browser component that creates a fake update interface resembling legitimate software prompts. Any user interaction — whether clicking on buttons or attempting to close the window — triggers the payload execution. Webview2's reliance on pre-installed components makes sandbox analysis ineffective, as automated environments often fail to simulate user interactions accurately.
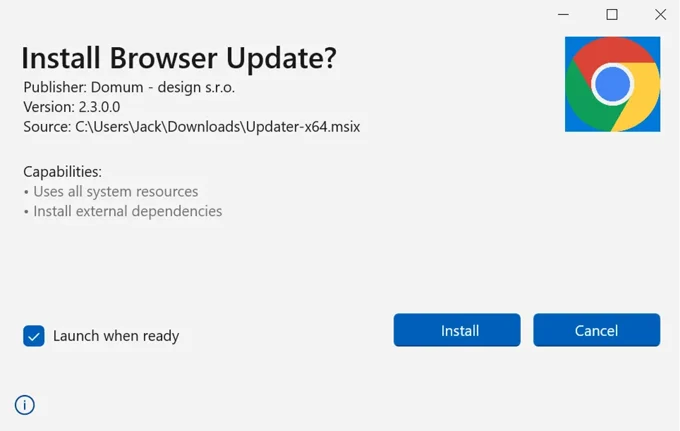
Morphisec
EtherHiding and other obfuscation tricks
CoinLurker's infection chain employs advanced obfuscation techniques to evade detection, with a process that spans multiple trusted platforms. It begins with Binance Smart Contracts, where encoded data containing payload instructions is embedded in blockchain infrastructure. Leveraging the decentralized and tamper-proof nature of blockchain, attackers ensure the data cannot be easily removed or altered.
Once the encoded instructions are retrieved, the malware connects to actor-controlled command-and-control (C2) servers, where further payload instructions or links are dynamically fetched. The infection chain concludes with the use of Bitbucket repositories that initially host benign executables. These files pass early security scans undetected but are later replaced with malicious versions. The tactic capitalizes on Bitbucket's reputation as a trusted platform, minimizing suspicion during the malware's distribution phase.
Notably, CoinLurker enhances its deception by signing the executables with Extended Validation (EV) certificates, likely stolen, to bypass security warnings and increase legitimacy. Between August and October 2024, filenames observed in these campaigns included BrowserUpdater.exe, UpdateNow.exe, and SecurityPatch.exe—all aligning with themes of system utilities and browser updates.
CoinLurker's injection and persistence
CoinLurker's execution process reveals multiple layers of obfuscation and stealth mechanisms. The malware employs a multi-layered injector to deploy its payload into legitimate processes, primarily msedge.exe, ensuring it blends seamlessly with normal system operations. This injection strategy allows CoinLurker to evade behavioral detection systems monitoring process behavior.
To prevent reinfection and maintain persistence, CoinLurker uses a heavily obfuscated function to validate whether a system is already compromised. It dynamically constructs unique registry keys, such as SOFTWARE\-, based on system-specific data. If the registry key exists, CoinLurker terminates execution, ensuring it does not re-infect the same machine.
Further complicating analysis, CoinLurker dynamically decodes command-line arguments, transforming obfuscated strings at runtime through multiple layers like Base64 decoding and UTF-16 conversion. Examples of arguments include strings like WSCOGJJEZZWL and NTOCBJPKZPNT. These strings are decrypted in memory during execution, leaving minimal traces on disk and making static detection nearly impossible.
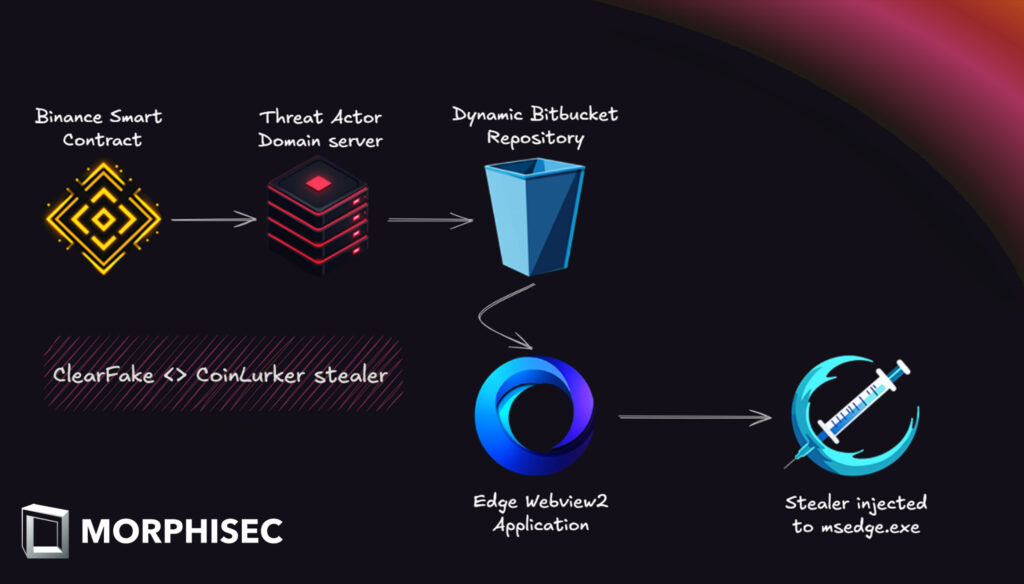
Morphisec
Focus on cryptocurrency and financial data
Morphisec's analysis highlights CoinLurker's primary goal: exfiltrating cryptocurrency and financial data. The malware systematically scans directories associated with major cryptocurrency wallets, including Bitcoin\wallets, Ethereum\keystore, and Ledger Live\Local Storage. Additionally, CoinLurker targets lesser-known wallets such as BBQCoin and Lucky7Coin.
Beyond cryptocurrency wallets, CoinLurker also focuses on financial applications and communication tools, accessing directories like Telegram Desktop's tdata folder, Discord's Local Storage, and FileZilla. This comprehensive targeting underscores the malware's adaptability and its emphasis on harvesting valuable account credentials.







Anybody experienced with computers knows the value of compartmentalization. If you are playing with code that somebody else wrote , that just seems like asking for it .