
Security researchers ‘Russian Panda’ and ‘Gonja’ have uncovered the workings of CryptoLove, a notorious traffer group operating elaborate crypto scams for over two years. Leveraging custom malware, hierarchical operations, and social engineering, the group has managed to siphon millions from victims across the globe.
A hierarchy built for deception
CryptoLove is structured like a corporation, with roles such as developers, mentors, and profit handlers. The group recruits “workers” through advertisements on dark web forums and social media platforms. Workers are supplied with various tools, including custom launchers, stealer malware like LummaC2 and StealC for Windows, and AMOS Stealer for macOS. These tools enable them to compromise victims' devices and siphon cryptocurrency.
trac-labs.com
To appear credible, workers purchase verified accounts on platforms such as Twitter, Discord, and Telegram, often for as little as $15. They use these accounts to pose as recruiters, influencers, or representatives of fake NFT projects and Web3 tools. Victims are targeted globally, with explicit instructions not to engage users in Commonwealth of Independent States (CIS) countries.
Social engineering tactics and tools
Workers lure victims by exploiting trending topics, such as blockchain and NFTs, and by creating fake landing pages disguised as legitimate platforms. These include phony gaming portals like Argon 2.0, software platforms such as Zoom Land, and even fake PDF readers like VeriScroll. These landing pages are designed to deploy malicious launchers when victims attempt to download software or register accounts.
Key strategies include:
- Using verified social media accounts to establish credibility.
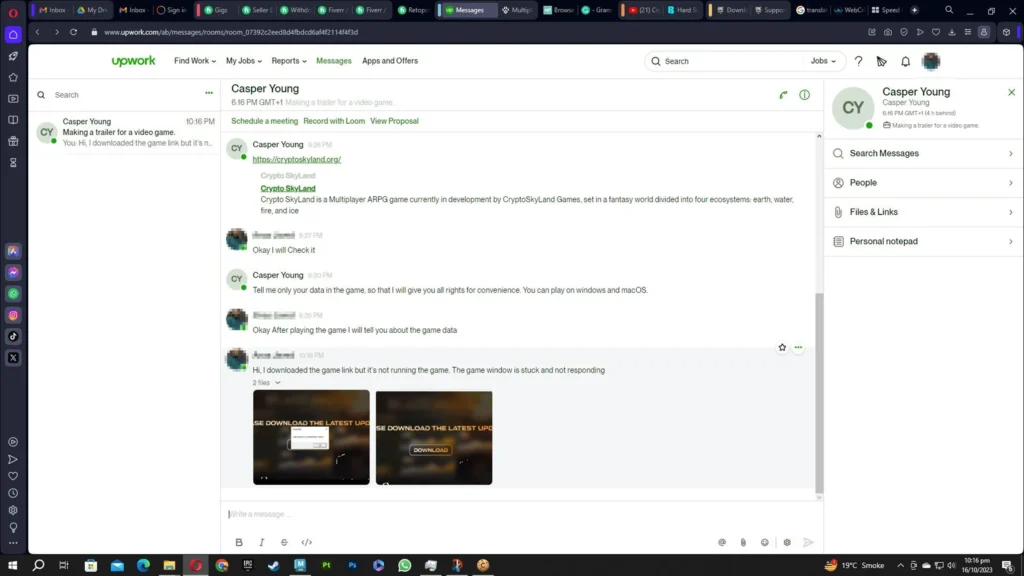
- Posing as recruiters on platforms like Upwork and Freelancer to trick users into running malware.
- Promoting counterfeit NFT collections and using airdrop scams to steal wallet credentials.
- Offering fake Zoom and WeChat installations that serve as malware delivery vectors.
Once the malware is deployed, it tracks user activity and exfiltrates sensitive data, including passwords, cookies, and wallet keys. CryptoLove affiliates then use this information to drain victims’ crypto wallets.
trac-labs.com
Scale of the CryptoLove operation
CryptoLove has logged over 22,000 unique IP addresses since November 2022. Workers receive payouts of 50% to 65% of the stolen funds, with top earners like “MxDuke” reportedly making over $55,000 from a single operation.
The group constantly evolves its tactics, most recently introducing a promo-code-based launcher system to enhance payload delivery stealth and ensure traceability to specific workers. The new launchers execute malware entirely in memory, avoiding traditional detection methods.
Some tell-tale signs of CryptoLove activity include:
- Unexpected prompts to install software like fake PDF readers or meeting tools.
- Suspicious URLs ending in .php?status=1&wallets=….
- Newly created folders like Cache_clientx86 or files named Morpheme32.exe.
CryptoLove exemplifies how sophisticated cybercriminal organizations operate in the crypto space, using a mix of technical expertise and psychological manipulation. As the group continues to adapt its methods, awareness and vigilance remain key defenses for individuals and organizations alike.






Leave a Reply