
Check Point Research has unveiled a novel cyberattack method leveraging the Godot Engine, a popular open-source game development platform. Hackers are using this engine to execute malicious GDScript code, delivering malware across multiple platforms, including Windows, macOS, and Linux, with minimal detection. The attack, driven by the GodLoader malware, has already compromised over 17,000 systems and operates largely undetected by most antivirus solutions.
Godot engine's appeal to threat actors
Godot is an open-source game engine widely used for developing 2D and 3D games. With its ability to export games to platforms like Windows, macOS, Linux, Android, and iOS, as well as its Python-like scripting language GDScript, Godot's flexibility makes it a natural choice for developers—and, unfortunately, cybercriminals.
The malware exploits Godot's pack (.pck) files, typically used to bundle game assets, to hide and execute harmful scripts. By embedding malicious GDScript into these files, attackers trigger malware execution without modifying the core executable, bypassing many security tools.
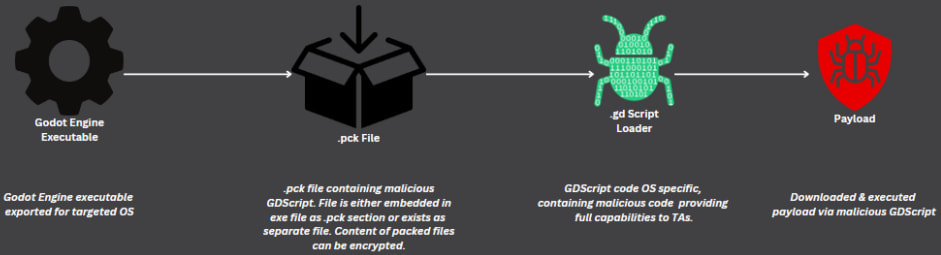
Checkpoint Research
GodLoader and the Stargazers Ghost Network
Since June 29, 2024, cybercriminals have been deploying GodLoader, a malware loader exploiting Godot's capabilities. Distributed via the Stargazers Ghost Network, a GitHub-based malware-as-a-service network, this campaign has utilized over 200 repositories and 225 fake accounts to create the illusion of legitimacy.
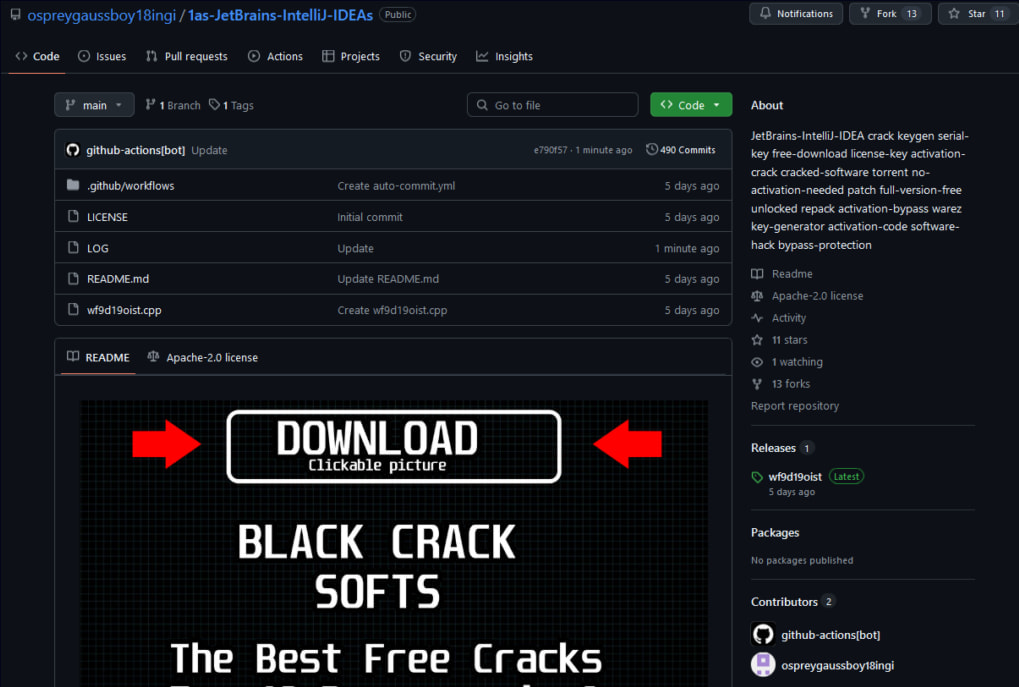
Checkpoint Research
Campaigns occurred in waves on September 12, 14, and 29, as well as October 3, 2024. The targets of these campaigns were developers, gamers, and general users downloading software or game mods.
The infection chain begins with the loader downloading and decrypting malicious .pck files, executing malware payloads on the host system. Initial samples included the RedLine Stealer and XMRig cryptocurrency miner, hosted on platforms like Bitbucket.org.
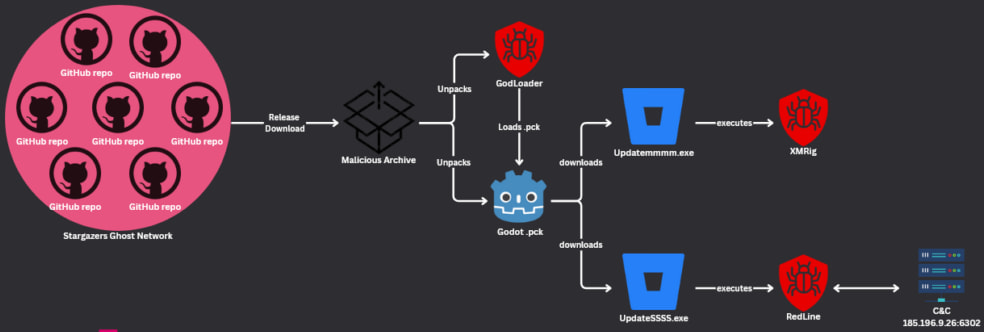
Checkpoint Research
The GodLoader malware is highly versatile, capable of targeting multiple operating systems. Initial proof-of-concept (POC) demonstrations by researchers showed that malicious payloads, such as calculators or ransomware, could be deployed on macOS and Linux systems using crafted GDScripts. The malware also employs several sophisticated techniques to avoid detection:
- Anti-sandbox measures: Checks for 3D video acceleration or sufficient free disk space to determine if it's in a virtualized environment.
- Obfuscation: Uses encrypted .pck files and stealthy execution chains.
- Admin privilege escalation: Adds entire disk drives to Microsoft Defender's exclusion list, effectively disabling detection.
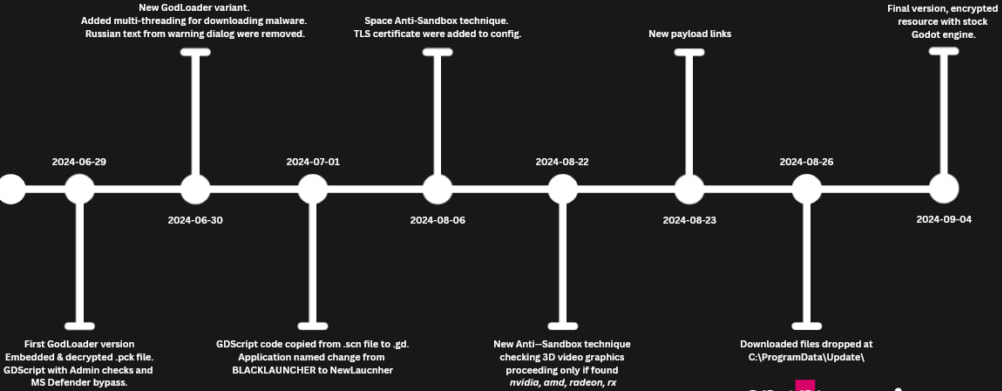
Checkpoint Research
Impact on the gaming community
The attack raises concerns for over 1.2 million users of Godot-developed games. Threat actors could exploit legitimate games by replacing authentic .pck files with malicious ones or tampering with Godot executables. This scenario resembles DLL hijacking and could devastate popular game communities, spreading malware disguised as downloadable content or mods.
To counter this growing threat, Check Point Research advises developers and game publishers to encrypt .pck files using asymmetric encryption methods to prevent unauthorized modifications and regularly monitor and validate file integrity using checksums or hashes.
Users are advised to avoid downloading games or mods from unverified sources, particularly GitHub repositories with few contributors or reviews, and use comprehensive security software that includes behavioral analysis and anti-exploit features.







Leave a Reply