
Unit 42, the threat research division of Palo Alto Networks, has uncovered a tactical shift in the operations of Bling Libra, the cybercriminal group behind the notorious ShinyHunters ransomware.
In a recent incident response engagement, Unit 42 revealed that Bling Libra has moved from selling stolen data to directly extorting their victims, specifically targeting cloud environments like Amazon Web Services (AWS).
Tactical evolution
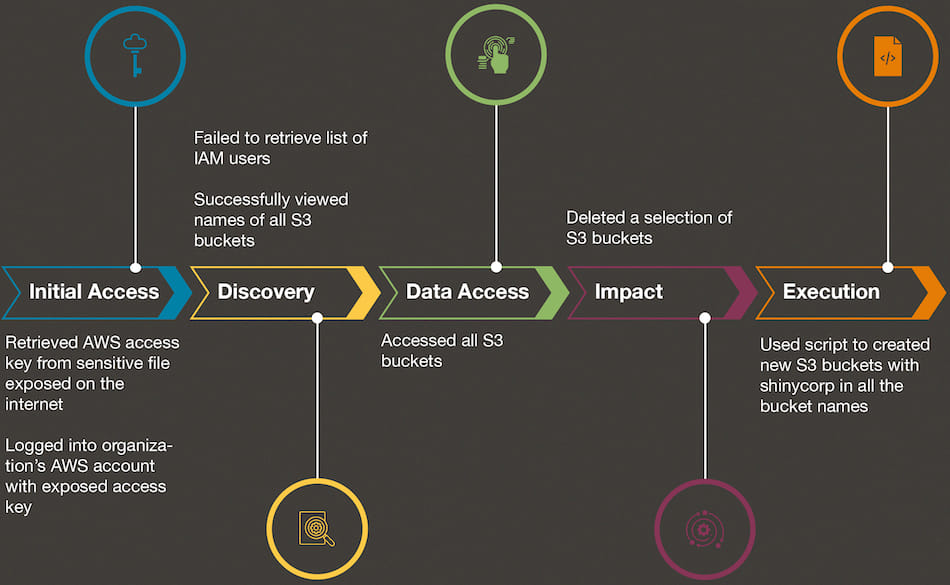
Bling Libra, first emerging in 2020, is known for high-profile data breaches such as the Microsoft GitHub and Tokopedia attacks. Traditionally, the group exploited legitimate credentials to access and sell sensitive information, but their latest strategy involves leveraging those credentials for extortion. The group's most recent attack on an unnamed organization's AWS environment highlights their new approach.
The attack began when Bling Libra obtained AWS credentials from a sensitive file exposed on the internet. These credentials allowed them limited access, confined to Amazon's Simple Storage Service (S3). Despite the restricted permissions, the group conducted extensive reconnaissance within the AWS environment, utilizing tools like the S3 Browser and WinSCP to analyze and manipulate S3 bucket configurations and data.
Once inside the AWS environment, Bling Libra employed a combination of manual and automated API calls to explore the organization's cloud infrastructure. The use of tools such as the S3 Browser and WinSCP allowed them to navigate S3 buckets, gather data, and eventually delete select buckets. Despite their destructive actions, the absence of detailed logging within the affected AWS environment left gaps in the incident trail, complicating the investigation.
- S3 Browser: This tool facilitated the initial exploration of the S3 environment. It generated specific API calls to list buckets, retrieve bucket locations, and even delete data. The group's usage of this tool shows their familiarity with AWS-specific tools to carry out sophisticated operations while remaining partially hidden from standard logging practices.
- WinSCP: Known primarily for file transfer, WinSCP was used by Bling Libra to view and delete files within the S3 buckets. Although it's not designed specifically for S3 management, WinSCP allowed the group to perform basic operations with the stolen credentials, further emphasizing the need for organizations to monitor all tools interacting with their cloud environments.
Unit 42
Extortion and impact
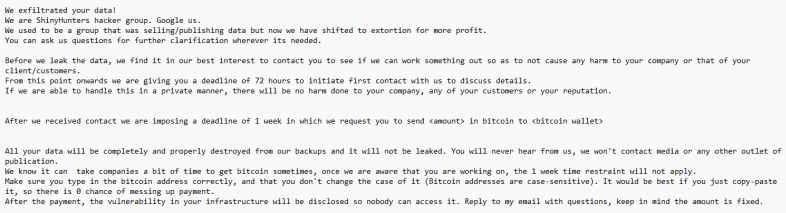
After completing their attack, Bling Libra sent a ransom note to the victim organization, claiming they had shifted from deploying ShinyHunters ransomware to pure extortion due to the profitability of this method. They demanded payment within a week, under threat of further actions or the public release of the compromised data. The incident reflects a broader trend in ransomware attacks, where data theft is increasingly followed by extortion rather than the immediate sale of stolen information.
The impact of the breach was limited to the S3 environment, thanks in part to the restricted permissions of the stolen AWS credentials. However, the attack serves as a stark reminder of the risks posed by exposed credentials and overly permissive access policies in cloud environments.
Unit 42
Defense measures
As cloud adoption grows, so does the sophistication of cyber threats targeting these environments. The Bling Libra attack underscores the need for robust security measures, especially around access management and logging.
To defend against similar attacks, Unit 42 recommends the following:
- Enforce strict access controls, ensuring that cloud credentials grant only the minimum necessary permissions.
- Leverage tools like Amazon GuardDuty, AWS Config, and AWS Security Hub can provide continuous monitoring and alerting on suspicious activities.
- Enabling detailed logging, especially for critical resources like S3, can significantly aid in detecting and responding to incidents.
- Conducting regular audits of IAM policies and cloud configurations can help identify and mitigate potential security gaps.







Leave a Reply