
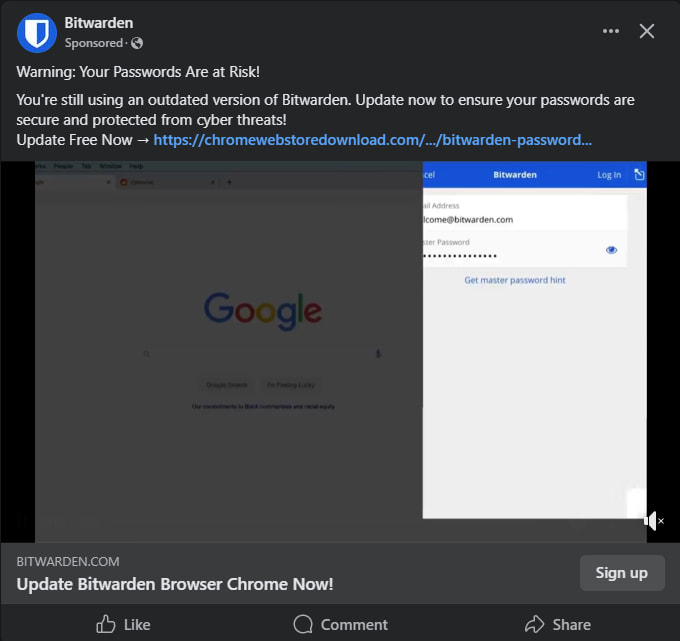
Bitdefender Labs has uncovered a malicious advertising campaign exploiting Facebook to target Bitwarden users with fake security updates. Launched on November 3, 2024, this campaign impersonates the popular password manager to distribute a harmful browser extension.
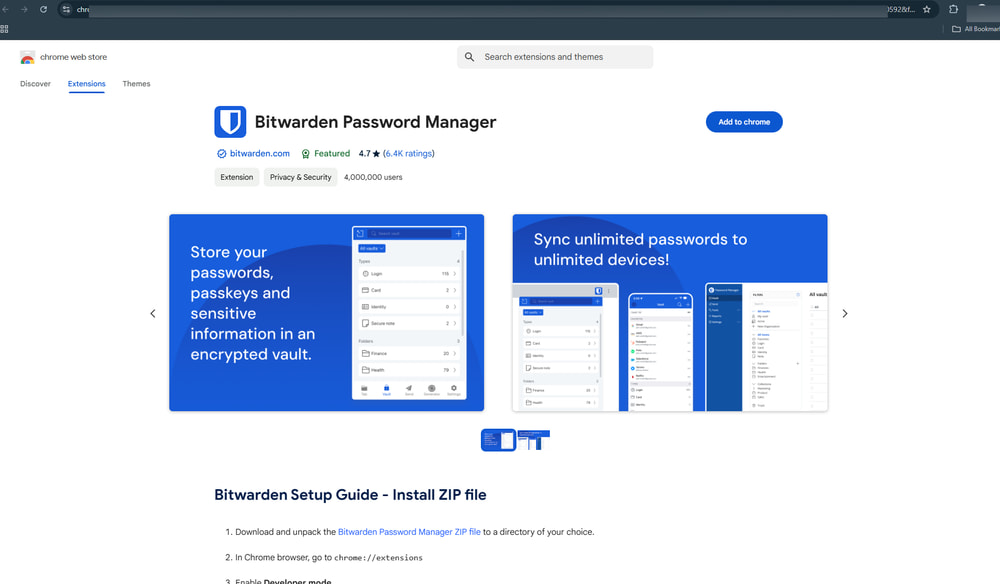
The attackers use Facebook's ad platform to deliver seemingly legitimate ads under the guise of a Bitwarden-branded security alert. The ads redirect victims through multiple domains, eventually leading to a phishing page mimicking the Chrome Web Store. From there, users are prompted to install a browser extension packaged as a ZIP file via a Google Drive link.
Bitdefender
To install the extension, victims were guided to bypass browser security by enabling developer mode and sideloading the unpacked extension. This process allows the malware to operate undetected, granting it extensive permissions to manipulate the user's browser and access sensitive information.
Bitdefender
Key permissions requested by the malicious extension include access to cookies and storage, the ability to modify network requests, and full control over tabs and page content.
Malware collecting data
The extension's main script, background.js, activates immediately after installation. It harvests sensitive data, focusing on Facebook accounts and business assets. The following steps outline the malware's operation:
- The script retrieves Facebook cookies, specifically targeting the c_user cookie, which contains user IDs.
- The malware collects IP and location data via external APIs.
- Using Facebook's Graph API, the malware gathers personal details, business account information, ad account data, and associated payment methods.
- Stolen data is transmitted to a Google Script URL, serving as the command-and-control (C2) server for attackers.
The campaign initially targeted users aged 18 to 65 across Europe, affecting thousands. However, its scalability and use of global platforms like Facebook and Google Drive mean it could easily expand worldwide. The stolen data has serious implications, including financial losses for individuals and businesses due to unauthorized access to advertising budgets and personal accounts.
Defense tips
Bitdefender Labs suggests that users monitor for excessive browser extension permissions, such as access to cookies and network requests, which can indicate malicious extensions. Moreover, it is recommended to look for unusual activity, like calls to graph.facebook.com APIs or obfuscated code initiated upon installation.
Extension sideloading is a high-risk operation that should be avoided. Instead, users should always verify update prompts with official sources.






Leave a Reply