
Mullvad VPN announced that macOS users may experience traffic leaks after applying recent system updates due to a firewall malfunction.
According to a bulletin published earlier today on Mullvad’s blog, the macOS firewall fails to enforce certain routing rules properly, allowing some applications to bypass the VPN tunnel and send traffic outside of it.
Mullvad has found that Apple’s own apps and services are excluded from the firewall, and hence sensitive user traffic is sent directly to its destination without getting encrypted. This includes iCloud, Siri, location services, the App Store, Apple Mail, and Messages, so the potential for privacy breaches and exposure to internet service providers (ISPs) or other intermediary observers is now present.
Most worryingly, the issue has been observed from macOS version 14.6 up until the most recent beta of 15.1, so it impacts a large number of Apple users.
A similar issue was discovered by Mullvad VPN prior to the release of macOS 14 Sonoma, in September 2023, but Apple fixed it before the OS was rolled out to eligible devices. Apparently, the traffic leak due to firewall misconfigurations has now been re-introduced by to a faulty system update.
The Sequoia release has had its fair share of VPN problems since its release. Users reported on Reddit last month that they encountered problems setting up a secure connection with some products. Experts claimed the issue stemmed from how the built-in firewall handled UDP traffic, causing DNS failures and also impacting security tools.
This time, the cause of the problem is unknown, and Mullvad VPN says it has already contacted Apple to ask for a resolution. Meanwhile their investigation to discover exactly what causes the leaks is still underway.
Impact and testing
Mullvad told RestorePrivacy that while they have not tested other VPN software on macOS to determine their operational status, it’s safe to assume that it affects any software that uses the packet filter (PF) firewall in macOS.
The VPN vendor also provided instructions for users in critical need of internet traffic security and privacy on how to check whether or not they’re leaking traffic.
To run the test, enter the following commands on a terminal:
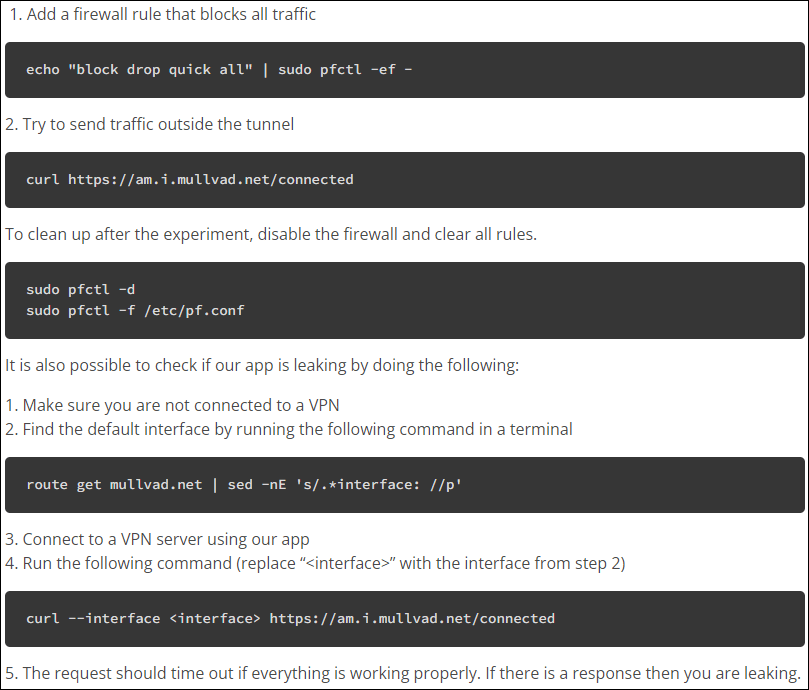
Note that that running the test will temporarily block all traffic, so you will lose internet connectivity on your device until the changes are reversed. Also, the commands provided by Mullvad temporarily modify the packet filter rules, so if you have custom firewall rules, you should back them up before running the tests to avoid losing them.







Will there be 2024 privacy tools reviews soon ?
I am sure it is a lot of work but most interesting part of the site.
Yes there will be.
Have there been any data leakage with Nord VPN or Surfshark?
no idea but you could just use proton vpn instead since Proton VPN is open source and independently audited
things like this is why i stopped using apple. vpns never worked on ios like they should and there is no real kill switch on ios without using a supervised phone basically a iphone setup for business use that someone else controls they block the feature from normal users. iphone had leaks and still has leaks and apple said there was no issues since its intended behavior. android has leaks via network connectivity checks but on grapheneos you can disable those. I have not seen that feature on other android os’s and that feature is missing from calyos. i noticed you can disable network connectivity checks in ubuntu also. not sure if its possible on the new furi linux phone that has uses a hard fork of waydroid since i do not have one.
network connectivity checks are awful on regular android your real ip is being sent to google servers constantly outside of the vpn. apple allows even more to be sent outside of vpn on ios to apple servers.
Ya dont say . A company like Apple wanting its spyware too talk too the mothership at all cost . How strange .