
Sophos has identified a new malicious tool, dubbed “EDRKillShifter,” employed by cybercriminals behind the RansomHub ransomware. This tool is designed to disable endpoint detection and response (EDR) systems, a critical line of defense in modern cybersecurity.
The discovery was made during the investigation of a failed ransomware attack in May 2024. The attackers attempted to deploy RansomHub ransomware on a target organization's system but were thwarted by the system's security features. A deeper analysis of the incident led to the identification of EDRKillShifter, a sophisticated “EDR killer” utility that specifically targets and disables EDR software, potentially opening the door for further malicious activity.
EDRKillShifter operation
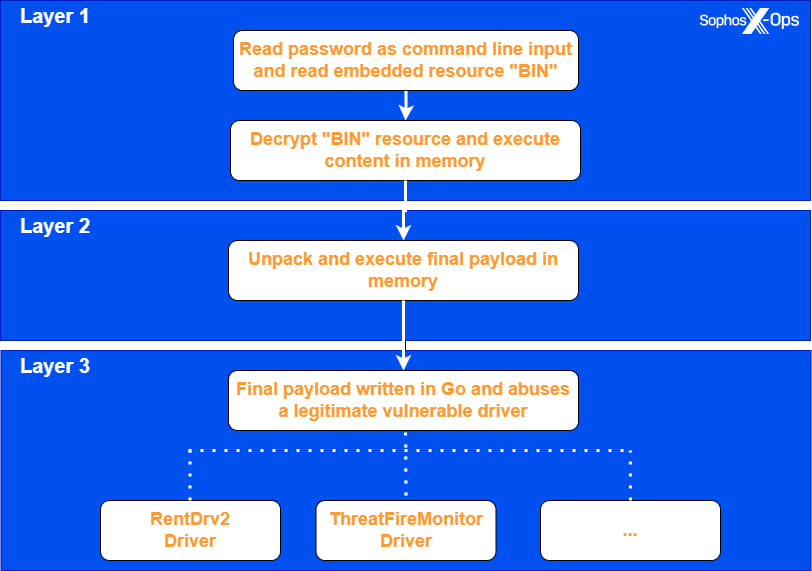
EDRKillShifter is categorized as a “loader” executable, which means its primary function is to deliver a vulnerable driver to the target system. This technique, known as “bring your own vulnerable driver” (BYOVD), allows the attacker to exploit legitimate software drivers that have known vulnerabilities. The process begins with the attacker running EDRKillShifter with a specific command-line password. Once the correct password is provided, the tool decrypts an embedded resource within itself, which then loads the final payload—a malicious driver—into memory.
Sophos
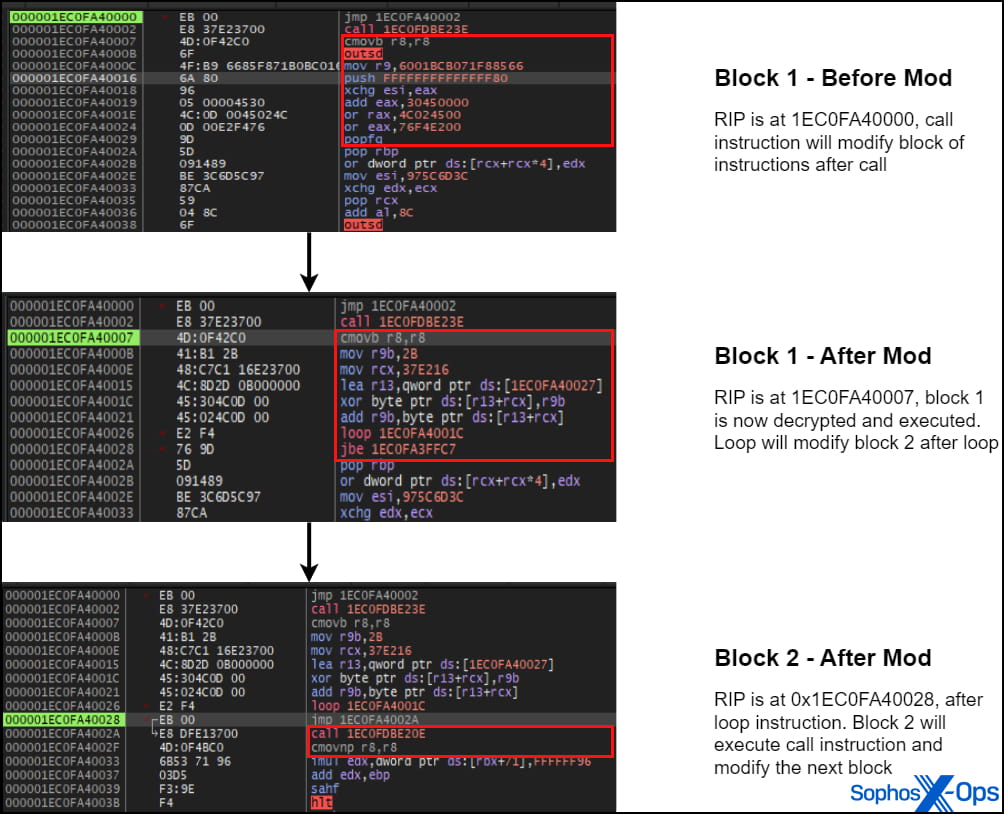
The loader uses advanced techniques to obfuscate its operations, including self-modifying code that alters its own instructions during runtime. This makes it particularly difficult for security researchers to analyze the malware. Once the vulnerable driver is loaded, the malware gains the necessary privileges to disable EDR tools by unhooking their protections. The final payload is written in the Go programming language, further complicating the reverse engineering process due to the use of obfuscation tools like gobfuscate.
Sophos
Deeper look
The threat actors behind RansomHub attempted to use EDRKillShifter to terminate the Sophos protection on the target system. Despite their efforts, the attack failed when Sophos's CryptoGuard feature, designed to block ransomware activities, was triggered. This failure highlighted the increasing sophistication of ransomware groups and their use of advanced tools to bypass security measures.
The binary code of EDRKillShifter suggests that it was compiled on a system with Russian localization settings, and the executable was disguised with metadata that mimicked the popular computer game “ARK: Survival Evolved.” This level of detail indicates a deliberate attempt by the attackers to evade detection and complicate attribution.
Analysis and recommendations
Sophos researchers were able to analyze the inner workings of EDRKillShifter using specialized tools, revealing that all samples shared common characteristics, such as embedding a vulnerable driver in the .data section of the binary. These drivers, once deployed, allow the malware to enumerate and terminate processes associated with EDR tools. The malware can even accept additional command-line arguments to target specific processes, making it highly adaptable to different attack scenarios.
Sophos suspects that EDRKillShifter is a modular tool, with the loader and final payloads possibly being developed by different threat actors. The loader, capable of deploying various payloads, might be sold separately on dark web marketplaces, making it a versatile weapon in the hands of cybercriminals.
To defend against such threats, Sophos recommends the following measures:
- Ensure that your endpoint security product has tamper protection enabled to prevent unauthorized changes to security settings.
- Maintain strict separation between user and admin privileges to limit the ability of attackers to escalate privileges and load malicious drivers.
- Regularly update systems to patch known vulnerabilities, including those in legitimate drivers that could be abused by BYOVD attacks.







Leave a Reply