
Sabian Cymbals is dealing with a widespread IT service outage that has impacted all its internal systems.
Sabian is a Canadian cymbal and drumming accessories manufacturer, one of the largest of its kind in the world, selling its products worldwide.
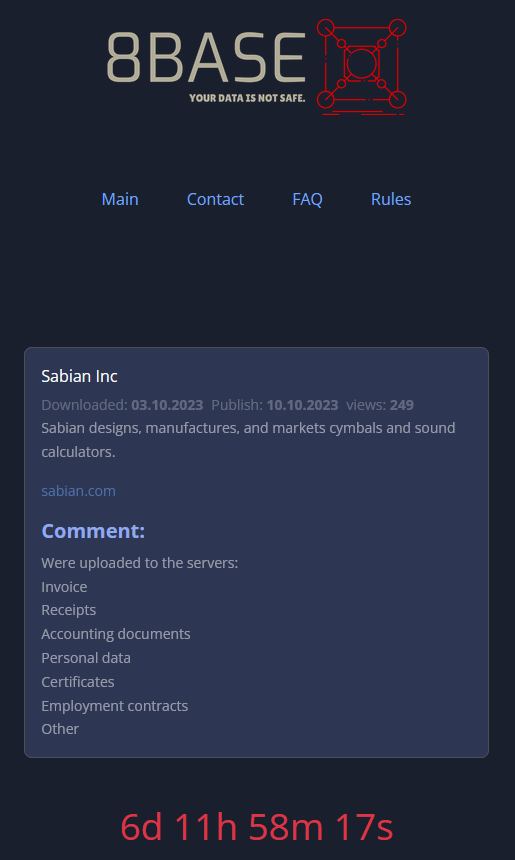
Today, the 8Base ransomware group posted Sabian on its extortion page on the dark web, claiming to have breached the company’s network and stealing invoices, receipts, accounting documents, personal data, certificates, employment contracts, and other documents in the process. The attackers give the firm a week to respond to their demands.
RestorePrivacy contacted Sabian immediately to learn more about the attack, receiving confirmation about an unexpected interruption that has disrupted the operation of all internal systems.
“We are not able to access the programs needed to issue return authorizations, check order status, enter warranty orders, or any other like service,” Sabian told RestorePrivacy, adding that their phone services are also down.
“Our IT team is working diligently to resolve this issue, and we hope to be back online soon,” concludes the response, confirming that the issue is of an IT nature.
Although the firm has not mentioned a ransomware attack or even a cyberattack as the causes of the outage, the status of its systems and the fact that they characterize the interruption as “unexpected” leaves little doubt that this is related to 8Base’s claims.
At this time, we are waiting for additional clarifications on whether the outage also impacts Sabian’s production operations or if the problems are limited to the provision of services to customers. We will update this post as soon as we receive more information from Sabian.
As ransomware attacks typically involve the exfiltration of data, there’s a significant risk that Sabian employees and customers who bought products from the brand’s online shop have had their personal information exposed to cybercriminals.
8Base launched its data leak site in May 2023 after almost a year of conducting data-encrypting attacks. This launch coincided with a significant spike in the threat group’s activity, listing 35 victims on its extortion portal by the end of next month. The group’s locker is based on the Phobos ransomware strain, which, unfortunately, has not been cracked by decryptor developers yet.







Leave a Reply