
On June 21, ANY.RUN announced via their official X page that they had been targeted by a phishing attack. Today, the company has provided a detailed account of the incident, outlining the timeline, initial response actions, and ongoing investigation.
The breach, which involved a compromised employee account, highlights vulnerabilities in their security protocols, prompting a comprehensive review and enhanced security measures.
ANY.RUN is an interactive online malware analysis service used by cybersecurity professionals to analyze and understand malware behavior. It provides dynamic and static analysis tools, allowing users to interact with malware samples in a controlled environment to study their behavior. ANY. RUN's customers include cybersecurity analysts, researchers, and IT security teams across various industries who rely on its platform to identify, analyze, and mitigate cyber threats effectively.
Incident summary
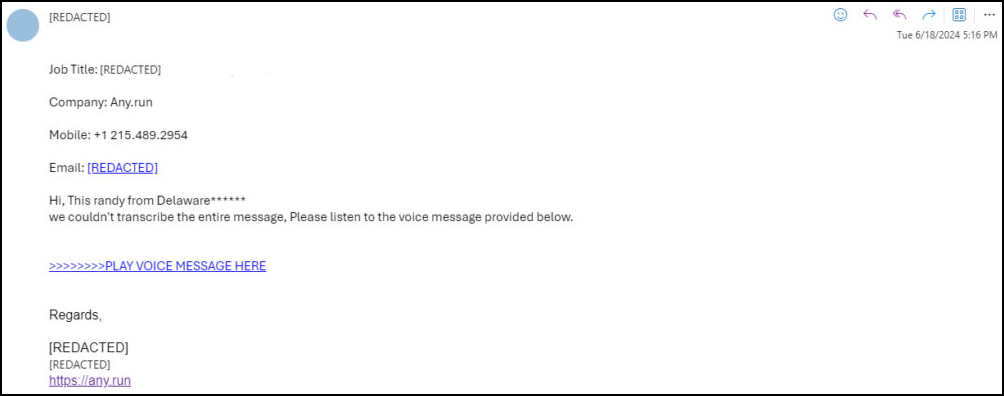
The phishing incident was first detected on the evening of June 18, 2024, when all ANY.RUN staff members received a phishing email from what appeared to be an internal employee. The email, sent to the entire contact list, directed recipients to a malicious page disguised as a Microsoft sign-in form. It soon became apparent that the employee's account had been compromised, facilitating a business email compromise (BEC) campaign.
The company's investigation traced the earliest unauthorized login to May 27, 2024, from IP address 45.61.169.4 in Sheridan, Wyoming. The breach was initiated through an adversary-in-the-middle (AiTM) phishing campaign. An employee received a phishing email from a compromised client.
ANY.RUN
Due to insufficient access controls and flaws in the multi-factor authentication (MFA) policies, the attacker managed to register their own mobile device with the MFA service, maintaining access to the compromised account.
Over 23 days, the unauthorized entity accessed the mailbox multiple times, utilizing PerfectData Software to potentially back up the entire mailbox.
Timeline
- May 23: An email with a phishing link was received by a sales team employee from a trusted client.
- May 27, 07:37: The employee uploaded the email to a sandbox environment, failing to detect the malicious content due to an improperly configured MITM proxy mode.
- May 27, 08:22: The attacker added their mobile device to the MFA service, securing persistent access.
- June 5,: The attacker installed PerfectData Software (Azure App ID: ff8d92dc-3d82-41d6-bcbd-b9174d163620), enabling the theft of email contents.
- June 18, 17:16: Using the compromised account, the attacker sent out phishing emails similar to the initial one, targeting the employee's entire contact list.
Unauthorized activities were detected on June 18, 2024, at 17:18:00. Access was terminated by 17:21:55, and compromised accounts were disabled, with credentials reset and active sessions revoked.
Additional account activity monitoring was implemented to prevent lateral movement. Robust access controls and restrictive MFA and conditional access policies are being implemented to ensure only compliant and trusted devices gain access.
ANY.RUN says it also implemented eradication measures, including artifact removal. Persistence techniques, such as adversary-controlled MFA devices and the PerfectData Software application, were identified and removed. Outlook rules associated with the attack were also eliminated.
ANY.RUN says it has decided to disclose this incident to the community to demonstrate their commitment to security. The company is analyzing the phishing samples and will share comprehensive findings in the future. The security firm admitted that this breach serves as a catalyst for improving their security infrastructure and enhancing their products for user safety.







thanks for info.