
Update 6/26: LockBit has posted files of what looks like parent directories, torrents, and compressed archive files belonging to Evolve Bank and Trust. Based on this, their previous claims about breaching the U.S. Federal Reserve were most likely a bluff, although the threat actors could release more information soon.
The notorious ransomware gang LockBit 3.0 has claimed responsibility for breaching the U.S. Federal Reserve, threatening to release 33 terabytes of sensitive banking information soon.
The group's announcement, posted on a newly established extortion portal, has sent shockwaves through the financial sector. However, the threat actors' claims have yet to be confirmed by any official sources.
The U.S. Federal Reserve, the central banking system of the United States, plays a pivotal role in the nation's economy by managing monetary policy, supervising and regulating banks, and maintaining financial stability. Its twelve regional banks oversee the distribution of money within their respective districts, making any breach potentially catastrophic. The Federal Reserve's responsibilities extend to implementing national monetary policy, providing financial services, and ensuring the stability of the financial system.
LockBit details the alleged breach on the new extortion portal, asserting that the Federal Reserve's operations across its twelve banking districts, including major cities like New York, Chicago, and San Francisco, have been compromised. LockBit 3.0 claims to possess extensive data that reveals critical banking secrets of American citizens.
The threat actor's post, dated June 23, 2024, explicitly states: “33 terabytes of juicy banking information containing Americans' banking secrets. You better hire another negotiator within 48 hours and fire this clinical idiot who values Americans' bank secrecy at $50,000.”
This statement indicates a failed negotiation attempt, but it's important to note that none of this has been verified. The Federal Reserve has yet to comment on the veracity of LockBit 3.0's claims or the steps it is taking to address the situation.
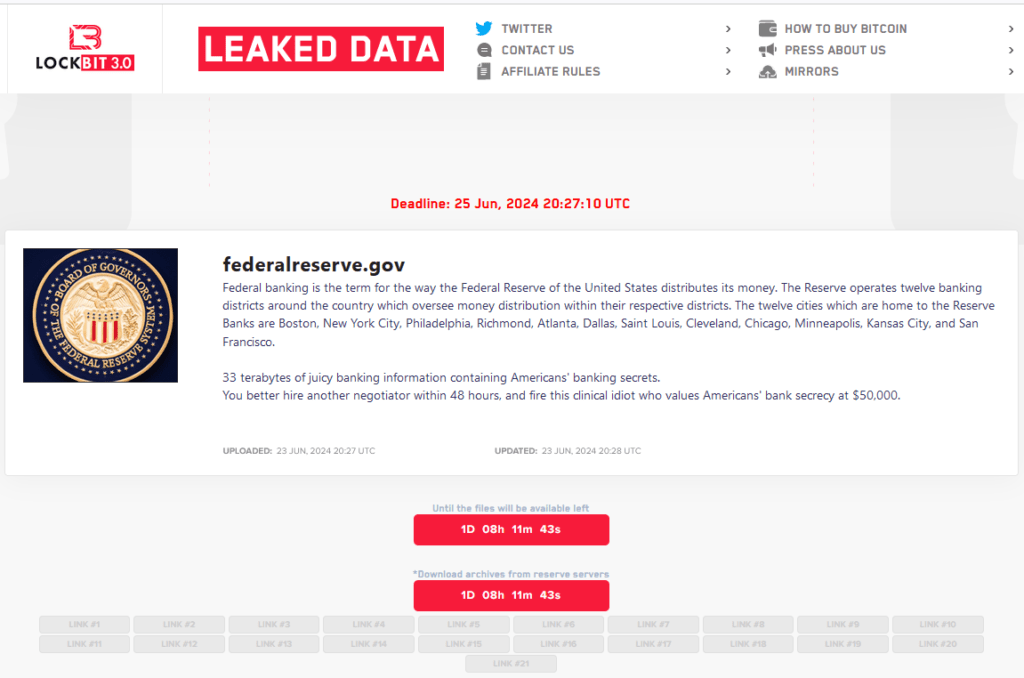
LockBit 3.0's extortion portal provides a countdown timer that expires in roughly 24 hours. The threat group has also listed multiple download links, implying that the data could be disseminated publicly if their demands are not met within the stipulated time. This strategy increases pressure on the Federal Reserve to respond swiftly to prevent the potential leak of sensitive financial data.
Recently, the LockBit ransomware group faced significant disruption due to a major international law enforcement operation, dubbed Operation Cronos. This effort, led by the U.K.'s National Crime Agency (NCA) and the FBI, involved the seizure of LockBit's technical infrastructure, arrest key members, and confiscating substantial financial assets.
Despite these setbacks, LockBit has retaliated by increasing its attacks on U.S. government entities, demonstrating their unwavering resilience and ongoing threat to cybersecurity. The claim against the U.S. Federal Reserve is a stark example of this, with the ransomware gang boldly taunting the authorities, targeting highly sensitive state organizations and leaking data allegedly stolen from them.







Leave a Reply