
Avast Threat Labs has identified a new variant of the Diamorphine rootkit, a notorious Linux kernel rootkit, operating undetected in the wild. This variant was found in early March 2024 and is notable for its advanced evasion techniques and expanded functionality.
Discovery and analysis
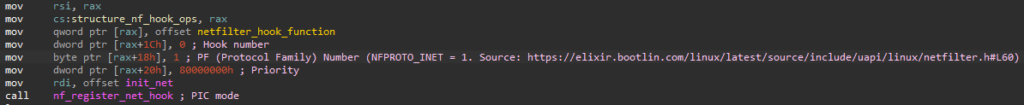
The rootkit was discovered by Avast researcher David Álvarez. Upon examining the sample, Álvarez identified that it masquerades as the legitimate x_tables Netfilter module and was compiled for the Linux kernel version 5.19.17. This variant retains the core functionalities of Diamorphine, such as hiding files and processes and elevating privileges, but introduces several new features.
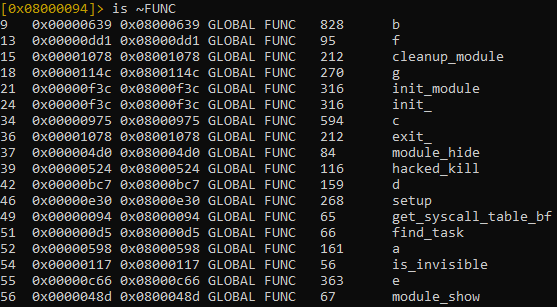
Using Radare2 for analysis, Álvarez noted the presence of standard Diamorphine functions (e.g., ‘module_hide,' ‘hacked_kill,' ‘get_syscall_table_bf,' ‘find_task,' ‘is_invisible,' and ‘module_show') along with additional payload functions labeled a through f. This indicates an enhancement in the rootkit's payload capabilities.
New Diamorphine variant
- Stop Diamorphine via xx_tables Device: Attackers can unload the rootkit by sending specific commands to the xx_tables device.
- Arbitrary Command Execution: The rootkit can execute arbitrary OS commands using magic packets, a method previously unseen in Diamorphine.
Avast
To deploy this variant, attackers need a Linux system running kernel version 5.19.17, with Ubuntu 22.04 being a likely candidate. The rootkit's integration with the xx_tables device allows seamless communication between user mode and kernel mode, utilizing a character device structure to manage operations.
The rootkit's dev_write operation is managed by the g function, which reads commands from user mode and executes them if they meet specific criteria, such as the input string “exit”, which triggers the rootkit's self-removal.
Avast
Impact and mitigation
The Diamorphine rootkit creates a device named xx_tables at the init_module function to facilitate user-kernel communication. It hooks into system calls to remain undetected and uses magic packets containing specific values encrypted with XOR to execute arbitrary commands.
The exit function, responsible for cleanup, effectively restores the system by destroying the created device, unregistering Netfilter hooks, and restoring original pointers in the syscall table.
To mitigate the risk of infection from this advanced rootkit, users and administrators should:
- Regularly update all software and system components to patch vulnerabilities.
- Use secure connections, such as VPNs, to protect against remote exploitation.
- Do not download or execute files from untrusted sources.
- Minimize the use of root privileges and perform tasks with the least necessary permissions.
- Employ comprehensive cybersecurity solutions like Norton, Avast, Avira, or AVG to detect and block malware.
The discovery of this new Diamorphine variant underscores the ongoing evolution of Linux kernel rootkits. The added functionality of magic packets and improved stealth mechanisms pose significant challenges for detection and removal.






Leave a Reply