
Microsoft and cybersecurity researchers from Kaspersky have uncovered a critical zero-day vulnerability in the Windows Desktop Window Manager (DWM) core library, which QakBot malware exploited to deliver various payloads.
Tracked as CVE-2024-30051, the vulnerability allows for privilege escalation to SYSTEM through a heap-based buffer overflow.
Discovery
The vulnerability was first flagged by Kaspersky security researchers while investigating a previously exploited zero-day in the same Windows component, identified as CVE-2023-36033. Their suspicions were raised by a document uploaded to VirusTotal on April 1, 2024, which described a similar exploitation technique to gain elevated privileges but pertained to a different, unrecorded flaw.
This document, characterized by its poor English and lack of complete details, initially seemed dubious. However, Kaspersky's subsequent validation confirmed its legitimacy as a new zero-day vulnerability. Microsoft was promptly notified, leading to an official patch released on May 14, 2024.
Researchers from Google Threat Analysis Group, DBAPPSecurity WeBin Lab, and Google Mandiant also contributed to reporting this flaw, indicating its potential widespread exploitation.
QakBot exploitation
The exploitation of CVE-2024-30051 was detected shortly after its discovery. Kaspersky observed its use alongside QakBot, a malware originally developed as a banking trojan but which has evolved into a versatile malware delivery tool involved in ransomware attacks and data theft. This suggests that multiple cybercriminal entities have gained access to and are actively utilizing this exploit.
The severity of this vulnerability is underscored by its capability to provide attackers with SYSTEM privileges, the highest level of rights on a Windows system. The attack requires no user interaction, has low complexity, and only requires low-level privileges to initiate, making it particularly dangerous.
Security recommendations
To safeguard against potential exploits leveraging CVE-2024-30051, users, and administrators are urged to apply the latest patches from Microsoft's Patch Tuesday release immediately. Kaspersky has updated its antivirus products to detect and prevent exploits associated with this vulnerability, listing multiple detection signatures:
- PDM:Exploit.Win32.Generic
- PDM:Trojan.Win32.Generic
- UDS:DangerousObject.Multi.Generic
- Trojan.Win32.Agent.gen
- Trojan.Win32.CobaltStrike.gen
CVE-2024-30051 has been fixed today as part of Patch Tuesday, the monthly Windows security update package. Users are recommended to apply the update as soon as possible. The latest cumulative update, KB5037771, brings a total of 30 fixes.
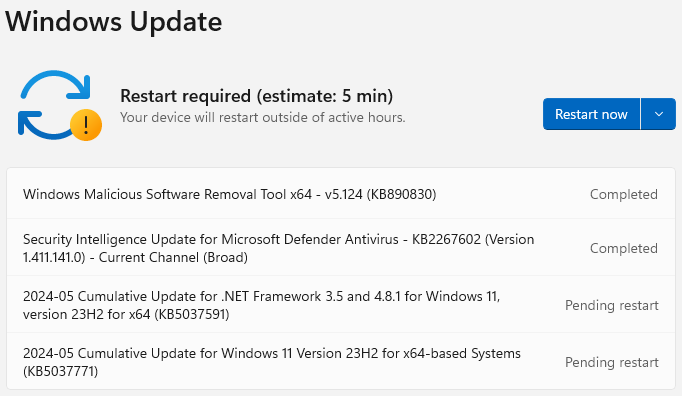
To install the update, head to Start > Settings > Windows Update and click ‘Check for Updates' to start the process. After all packages are installed, a restart is required for the fixes and changes to apply.







Leave a Reply