Security researchers have revealed significant vulnerabilities in F5’s Next Central Manager, a crucial component of F5’s latest BIG-IP product line.
These vulnerabilities, if exploited, could enable attackers to gain complete administrative control and create hidden, unauthorized user accounts across F5-managed assets.
The vulnerabilities were identified by Eclypsium during ongoing security research into F5's systems, known for their widespread use in networking and application infrastructure.
The discovery included a total of five vulnerabilities, though only two were deemed critical enough to warrant CVE identifiers: CVE-2024-21793 and CVE-2024-26026. Despite F5's swift response to publish fixes, the fact that only two CVEs were assigned raises concerns about the comprehensive security of the updates provided.
Flaw details and impact
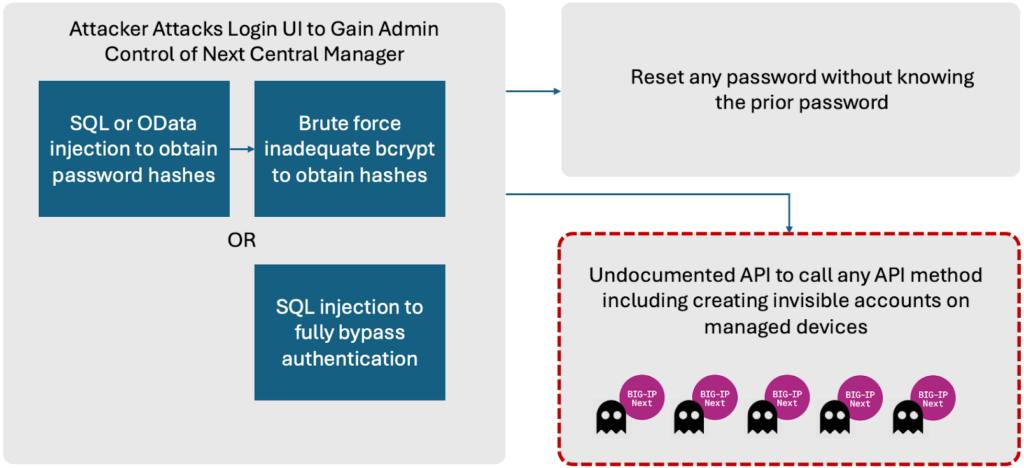
- CVE-2024-21793 (Unauthenticated OData Injection): This vulnerability allows attackers to manipulate OData queries to leak sensitive information like administrator password hashes, provided LDAP is enabled.
- CVE-2024-26026 (Unauthenticated SQL Injection): This flaw could enable attackers to execute SQL statements that bypass authentication mechanisms to access administrative user password hashes.
The researchers also pointed out less critical issues that were not assigned CVEs, including an SSRF vulnerability allowing unauthorized API calls, inadequate bcrypt hashing for passwords, and the ability to reset admin passwords without prior knowledge.
Eclypsium
F5 has responded by releasing software version 20.2.0 to address these critical vulnerabilities, particularly in configurations ranging from version 20.0.1 to 20.1.0 of the Next Central Manager. Users of affected versions are urged to update their systems immediately to mitigate potential risks.
Organizations using the affected F5 products should:
- Upgrade to the latest firmware release (20.2.0) as recommended by F5.
- Limit management access to the devices to trusted users and secure networks.
- Monitor network activity for any anomalies that may suggest exploitation attempts.
Currently, there is no indication that these vulnerabilities have been exploited in the wild at the time of their report. Still, it is imperative that system administrators apply the available security updates as soon as possible to mitigate the risk, as proof of concept (PoC) exploits that demonstrate the exploitation process were made available in Eclypsium’s report.







Leave a Reply