
Yanluowang ransomware group has just claimed Cisco Systems as its latest victim. We have analyzed the file tree sample provided by Yanluowang to verify the legitimacy of the group's claims and also reached out to Cisco for comment.
Update: After this story went live on August 10 at 1:12 PM, Cisco Systems provided RestorePrivacy with a statement confirming that it suffered a “security incident” in May 2022. The full statement has been added below, along with a summary of how these events transpired.
Earlier today, the Yanluowang ransomware group published the latest victim to its dark web cybercrime website. Yanluowang is claiming to have breached Cisco Systems, the technology conglomerate based in San Jose, California.
On the group's dark web blog site, you can see an entry called “Hot news straight from Cisco” that is dated today (August 10th).
Back in June, we observed Yanluowang to have also claimed Wal-Mart as a victim. However, Wal-Mart has officially disputed these claims according to some news reports.
Below is the dark web blog post that went live earlier today on Yanluowang's website:
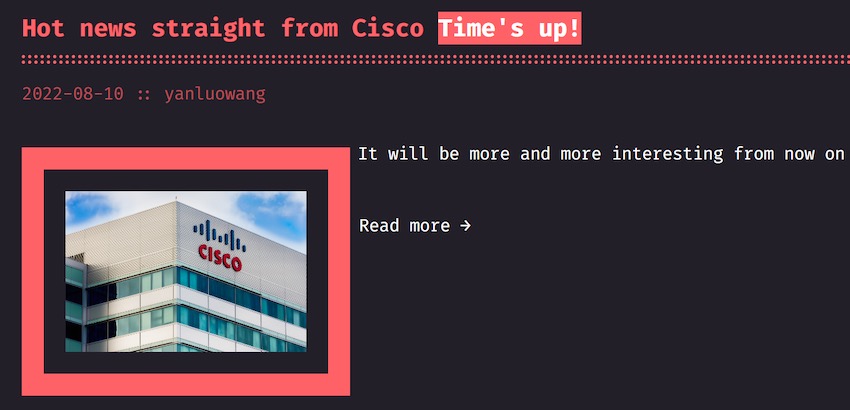
In addition to the announcement declaring Cisco as the group's latest ransomware victim, Yanluowang also published a .txt list of files allegedly obtained in the cyber attack.
Yanluowang publishes list of Cisco files allegedly obtained from the cyberattack
On Yanluowang's dark web blog site, one can download a text file that the group is claiming to have obtained from Cisco. We examined the list and it includes approximately 3,100 files of various types. A small sample from the file tree that we examined is below.
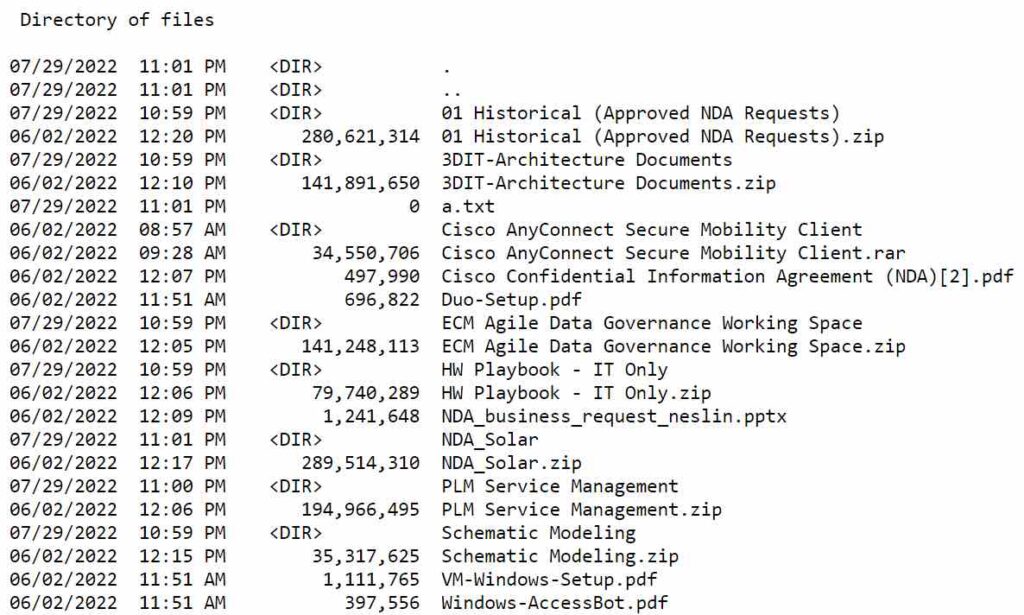
In total, there appears to be about 2.8 GB of data and 3,176 files that Yanluowang claims to have exfiltrated from Cisco.

Unlike other recent attacks we have analyzed, Yanluowang is not fully releasing the documents themselves, but rather just a file list (for now).
However, there is also a list of non-disclosure agreements with different personnel within Cisco. In our attempt to verify the data, it does appear that the individuals match up with real-world people who are associated with Cisco.
About Yanluowang
Yanluowang ransomware has been gaining more attention over the past year.
Its website claims a number of victims going back to October 2021, with the first entry being for the company Timios Inc., a title and escrow company based in California.
Symantic has an interesting report that discusses how Yanluowang ransomware is being deployed against organizations around the world.
Symantic notes how Yanluowang ransomware carries out the following actions after it is deployed:
- Stops all hypervisor virtual machines running on the compromised computer
- Ends processes listed in processes.txt, which includes SQL and back-up solution Veeam
- Encrypts files on the compromised computer and appends each file with the .yanluowang extension
- Drops a ransom note named README.txt on the compromised computer
Interestingly, Yanluowang has primarily been targeting US-based companies over the past year.
We have reached out to Cisco for comment on the situation, but have not yet heard back at the time of publication (August 10, 2022 at 1:12 PM).
Update: Cisco provides RestorePrivacy with a statement — confirms a “security incident” transpired
Shortly after this article went live, we received a statement from Cisco Systems spokesperson. It is posted in full below:
Cisco experienced a security incident on our corporate network in late May 2022, and we immediately took action to contain and eradicate the bad actors. Cisco did not identify any impact to our business as a result of this incident, including Cisco products or services, sensitive customer data or sensitive employee information, intellectual property, or supply chain operations. On August 10 the bad actors published a list of files from this security incident to the dark web. We have also implemented additional measures to safeguard our systems and are sharing technical details to help protect the wider security community.
– Cisco Spokesperson statement to RestorePrivacy on August 10, 2022
In addition to the statement above, Cisco also provided RestorePrivacy with an executive summary of events.
The summary below comes from the Cisco Talos Intelligence blog here.
- On May 24, 2022, Cisco became aware of a potential compromise. Since that point, Cisco Security Incident Response (CSIRT) and Cisco Talos have been working to remediate.
- During the investigation, it was determined that a Cisco employee’s credentials were compromised after an attacker gained control of a personal Google account where credentials saved in the victim’s browser were being synchronized.
- The attacker conducted a series of sophisticated voice phishing attacks under the guise of various trusted organizations attempting to convince the victim to accept multi-factor authentication (MFA) push notifications initiated by the attacker. The attacker ultimately succeeded in achieving an MFA push acceptance, granting them access to VPN in the context of the targeted user.
- CSIRT and Talos are responding to the event and we have not identified any evidence suggesting that the attacker gained access to critical internal systems, such as those related to product development, code signing, etc.
- After obtaining initial access, the threat actor conducted a variety of activities to maintain access, minimize forensic artifacts, and increase their level of access to systems within the environment.
- The threat actor was successfully removed from the environment and displayed persistence, repeatedly attempting to regain access in the weeks following the attack; however, these attempts were unsuccessful.
- We assess with moderate to high confidence that this attack was conducted by an adversary that has been previously identified as an initial access broker (IAB) with ties to the UNC2447 cybercrime gang, Lapsus$ threat actor group, and Yanluowang ransomware operators.
- For further information see the Cisco Response page here.







Lady password hacker
https://www.bleepingcomputer.com/news/security/lastpass-developer-systems-hacked-to-steal-source-code/
https://www.forbes.com/sites/daveywinder/2022/08/25/lastpass-hacked-password-manager-with-25-million-users-confirms-breach/
Hi Bronco,
A good read, Thanks for posting
Not related, but directed to Sven.
Can you do a post on options for VOIP users who are forced to provide mobile numbers to providers such as Telegram, Twitter, and Facebook but they block these virtual numbers and only accept actual mobile numbers?
Yes, there are services to receive SMS messages online. I think it is just a matter of trying different numbers and services until you find one that works for registering.
Yanluowang, meaning king of hell in chinese. politically motivated to hack against US target. Am not surprise at all.
I HAVE BEEN A VICTIM MARCH 2022
Hi Sven,
My God! Cisco?
Isn’t Cisco our backbone infrastructure?
Great reporting from RP.
Great incident response from Cisco.
Regards,
BoBeX
the stupid name made me be curious.
!no,no,,CN and US,,buddy buddy…
especially for filthy rich.
Wonder what will be a threat for clamav and immunet both antiviruses reccomended by restoreprivacy here. They are both cisco systems. Cisco backed.