
Akamai researchers have disclosed startling findings about phishing campaigns targeting the United States Postal Service (USPS), revealing that certain fake domains receive as much web traffic as the official USPS website during peak periods.
This discovery comes as part of an in-depth analysis conducted by the cybersecurity team at Akamai, spotlighting the sophisticated tactics employed by cybercriminals to exploit the high traffic volumes associated with holiday seasons.
Akamai researchers observed a suspicious smishing attempt directed at a team member and embarked on an extensive analysis of DNS traffic data sourced from Akamai’s CacheServe DNS servers. The researchers meticulously compared five months of DNS traffic from both legitimate and illegitimate domains that purportedly represented the USPS.
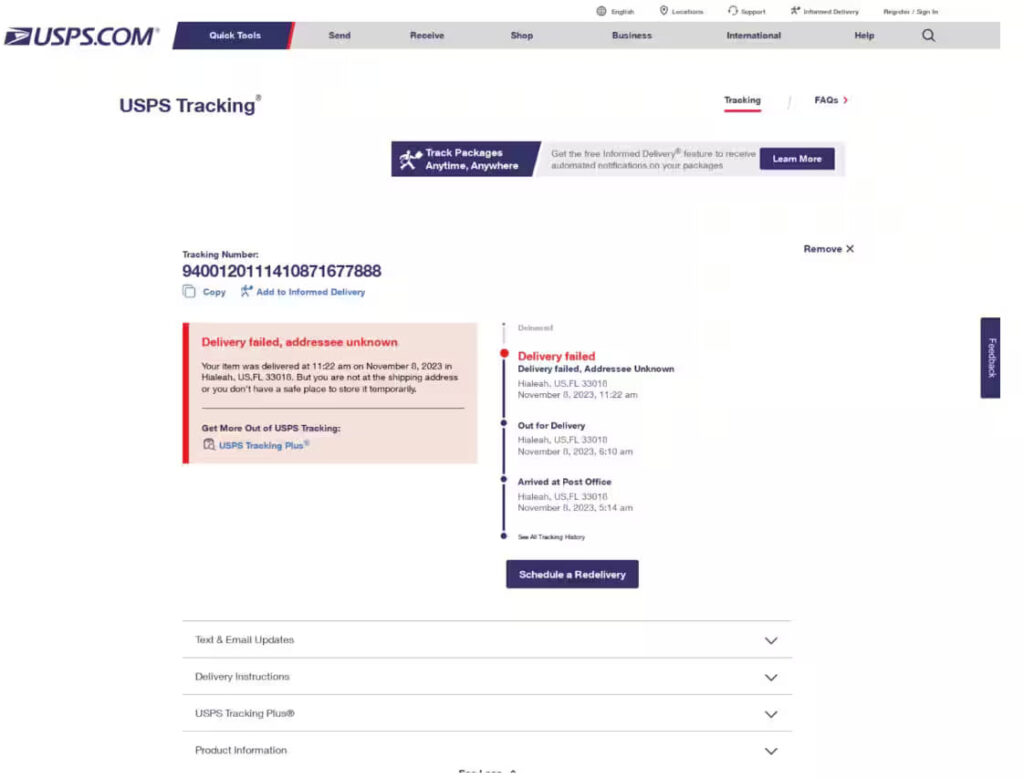
They found that during the 2023 holiday season, traffic to these fraudulent domains, referred to as combosquatted domain names, not only matched but occasionally surpassed that of the legitimate usps.com.
The analysis relied on stringent criteria to filter out legitimate domains, focusing exclusively on those with clear signs of impersonation.
Akamai
Key findings and insights
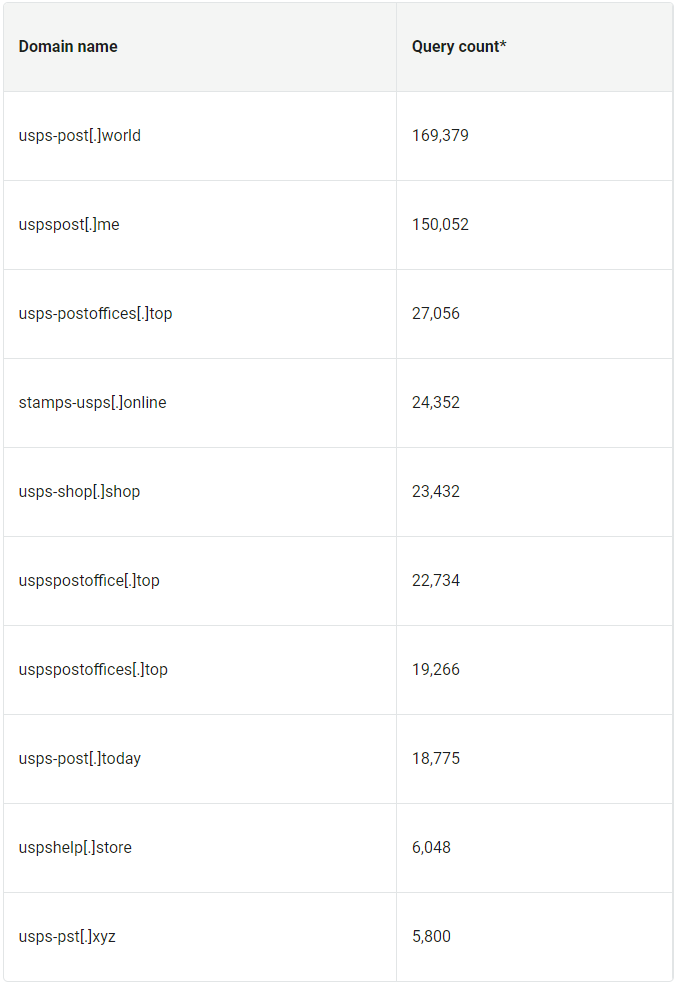
The team identified a series of malicious domains, such as usps-deliveryservice.icu and usps-lookup.com, which used similar JavaScript file hashes or HTML patterns indicative of phishing activities. Notably, two domains, usps-post.world and uspspost.me, drew significant attention due to their high query counts, together accounting for 29% of the traffic within the dataset.
Further investigation into the top-level domains (TLDs) revealed that .com and .top were predominantly used for registering these malicious sites, with .com domains providing a veneer of credibility and familiarity to potential victims.
Akamai
The report also highlighted the operational tactics of these phishing campaigns. By strategically launching attacks around major U.S. holidays like Thanksgiving and Christmas, scammers capitalized on the increased parcel traffic and the heightened likelihood of users interacting with deceptive messages.
Given the significant overlap in DNS query volumes between legitimate and malicious USPS domains, the Akamai team emphasizes the critical need for heightened vigilance, especially during high-traffic periods.
Users are advised to double-check the authenticity of any communication purportedly from the USPS, particularly those received via SMS or email around holidays. Furthermore, the public should regularly consult the USPS’s official warnings and guidelines on identifying and reporting phishing attempts.







Leave a Reply