
A new malware strain dubbed “Sharp Stealer” is making its rounds in the cybercrime community, targeting a lucrative market: gamers.
Recently uncovered by threat researcher Yogesh Londhe, and detailed in a GDATA report, this infostealer highlights the continued evolution and persistence of malware targeting personal and sensitive information.
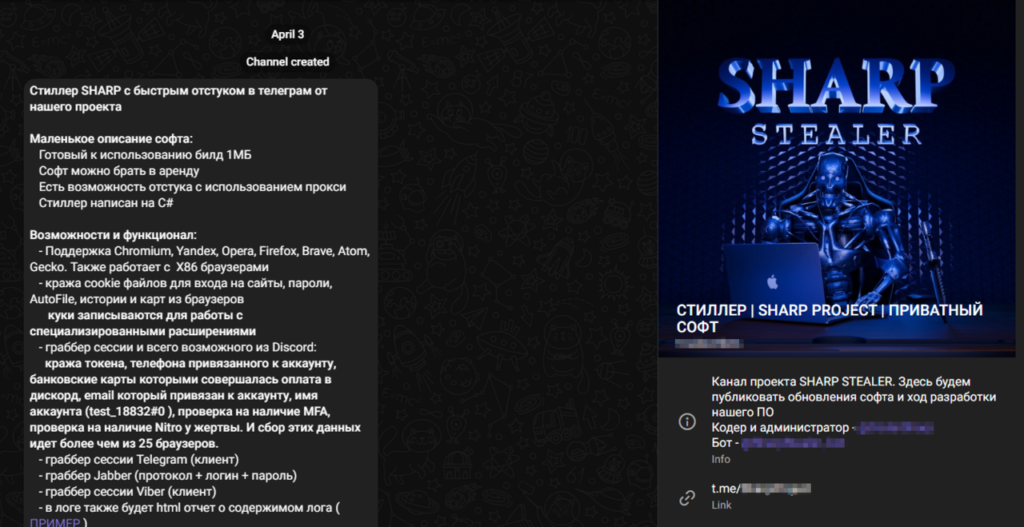
Yogesh Londhe took to X (formerly Twitter) to reveal findings about a new malware spotted in the form of an executable named “Sharpil RAT.exe.” Despite its designation as a RAT (Remote Access Trojan), the software's primary function aligns more closely with that of an infostealer. The discovery unfolded when Londhe investigated the non-obfuscated .NET application, which led to further samples and the identification of the “Sharp Stealer” family.
Sharp Stealer details
“Sharpil RAT.exe” operates by connecting to a Telegram bot, initiating commands to extract data from several browsers and systems, particularly those prevalent in gaming environments. This includes data from popular browsers and gaming platforms such as Minecraft's “Vime World” server. The bot uses methods like “ParseLastMessage” to interpret commands from the threat actor, facilitating the theft of data, including system information, browser data, and more.
GDATA
The stealer itself, found through the name “sharp_build.exe,”” incorporates elements from other malicious software like Echelon and Umbral stealers, utilizing the Ionic Framework and cryptographic functions from the BCrypt library for data handling and obfuscation.
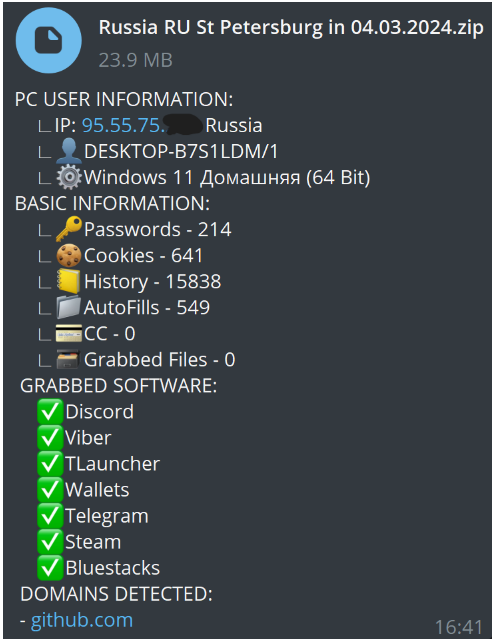
The focus on gamers is strategic. The malware targets data-rich applications such as Discord, Steam, and various other gaming and messaging platforms, where it can extract valuable information like game cookies, account details, and even payment data. This data is particularly valuable on the dark web where in-game items and accounts are traded for profit.
GDATA
Though Sharp Stealer has not yet gained significant traction in the underground market, this could change soon, given its capabilities. Also, the malware has a visible presence on systems and lacks sophisticated evasion techniques like sandbox detection, which are common in more mature infostealers, so there's still work to be done. As noted by malware analyst Anna Lvova, its simplicity and direct method of data exfiltration through a Telegram bot suggest that we may see more from Sharp Stealer as its developers refine its features.
For users, particularly gamers, the emergence of Sharp Stealer underscores the importance of robust cybersecurity practices. Actionable tips include:
- Ensure all software, especially gaming applications and browsers, are up-to-date with the latest security patches.
- Use comprehensive security solutions that include behavior-based detection to catch unusual activities typical of infostealers.
- Avoid downloading software from unofficial sources, which can often be laced with malware.
- Stay informed about common phishing tactics, as these are often the first steps in a malware infection.







Leave a Reply