
Microsoft has rolled out patches for two critical zero-day vulnerabilities within its Windows operating system, exploited by the SmokeLoader malware operators.
The first vulnerability, designated CVE-2024-28493, allowed attackers to gain elevated privileges on the affected systems, bypassing standard security measures to execute malicious code with increased permissions. The second, CVE-2024-29988, was a remote code execution flaw, offering attackers the ability to control an infected machine remotely.
Both vulnerabilities were not just theoretical threats; they had been exploited in the wild as part of sophisticated malware campaigns, highlighting the real-world implications of these security gaps.
Microsoft's Security Response Center (MSRC) swiftly addressed these vulnerabilities, incorporating the fixes in its latest security update. The company's prompt action reflects its commitment to protecting users from evolving cyber threats. By closing these security loopholes, Microsoft has significantly mitigated the risk of unauthorized access and control by malicious actors.
Parallel to the zero-day fixes, an intriguing cybersecurity development unfolded with the discovery of a new campaign involving the notorious SmokeLoader malware. Detailed investigations by cybersecurity experts at Sophos revealed a sophisticated attempt to distribute a backdoor masquerading as a legitimate signed application. This campaign, leveraging the newly patched vulnerabilities, underscores the complexity and stealthiness of modern cyberattacks.
Sophos
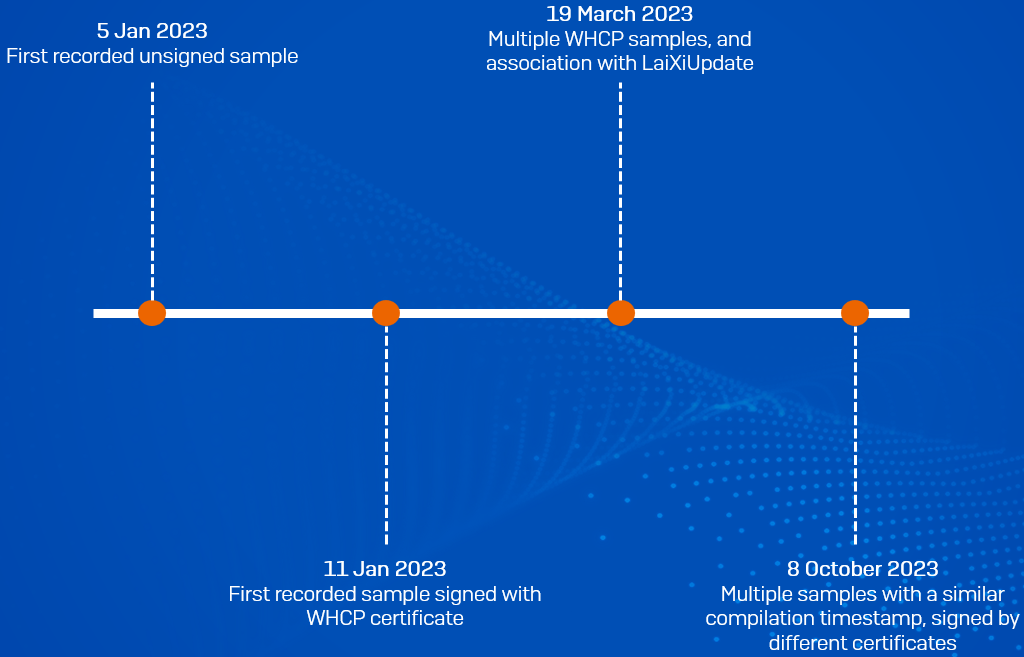
SmokeLoader, a well-known malware strain, has been previously associated with various cybercriminal activities, including the distribution of additional payloads and the exfiltration of sensitive information. The recent campaign involving SmokeLoader introduced a signed backdoor cleverly designed to evade detection by security software. This tactic of using legitimate digital certificates to sign malicious software is a testament to the evolving sophistication of threat actors.
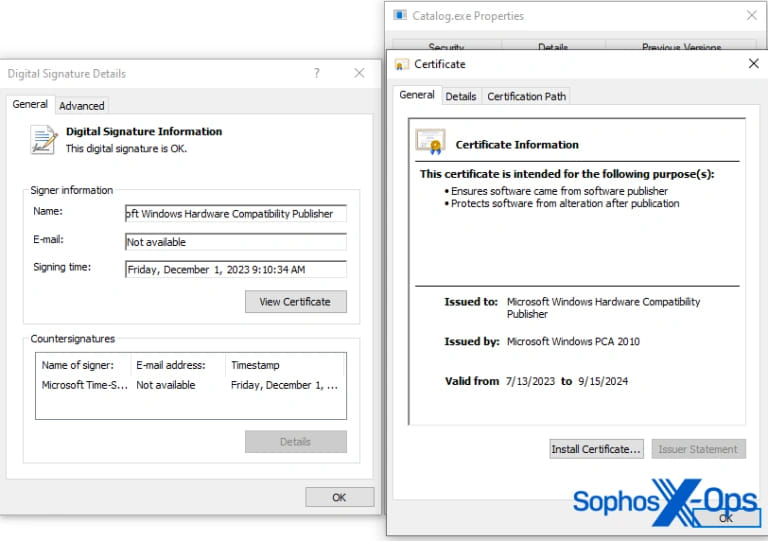
Sophos
The backdoor, once installed, can perform a range of nefarious activities, from stealing personal information to installing further malicious payloads. Its discovery, alongside the exploitation of the zero-day vulnerabilities, serves as a stark reminder of the multifaceted nature of cyber threats today. It also highlights the importance of comprehensive cybersecurity measures, including the prompt application of security patches.
Microsoft's recent patches close critical security gaps that had been actively exploited, reinforcing the tech giant's role in securing the digital ecosystem. However, the discovery of sophisticated campaigns like that involving SmokeLoader serves as a reminder of the need for relentless vigilance and proactive cybersecurity practices. Users are advised to update their systems promptly and stay informed about potential threats to maintain a strong defense against cyberattacks.







Leave a Reply