
In a comprehensive security analysis of CD Projekt Red's GOG Galaxy 2.0 gaming platform, researchers have identified two significant vulnerabilities that could compromise user security.
GOG Galaxy is a digital distribution platform developed by CD Projekt Red, the renowned video game developer behind titles such as “The Witcher” series and “Cyberpunk 2077.” Designed to provide gamers with a convenient way to purchase, download, and manage their game libraries, GOG Galaxy stands out for its commitment to DRM-free gaming.
According to a report by Anvil Secure, the GOG Galaxy gaming platform is susceptible to a Denial-of-Service (DoS) attack (CVE-2023-50915) and a Local Privilege Escalation (CVE-2023-50914).
The discovery process, initiated as part of a broader research project, began with investigating the platform's interaction with the file system and the Inter-Process Communication (IPC) between its client process and its privileged service. The analysis led to identifying the vulnerabilities, with the initial focus on a potential DoS vulnerability, which researcher Alex Popovici later expanded upon to include a local privilege escalation issue.
Vulnerabilities in GOG Galaxy
CVE-2023-50915 – The DoS vulnerability arises from how GOG Galaxy's client and service processes handle log files in the installation directory. Both processes write log files with different privilege levels, leading to a scenario where a low-privileged process can influence the behavior of a high-privileged process. This flaw allows attackers to potentially corrupt critical Windows system files by redirecting the privileged process to overwrite them, necessitating a system restore or complete OS reinstall.
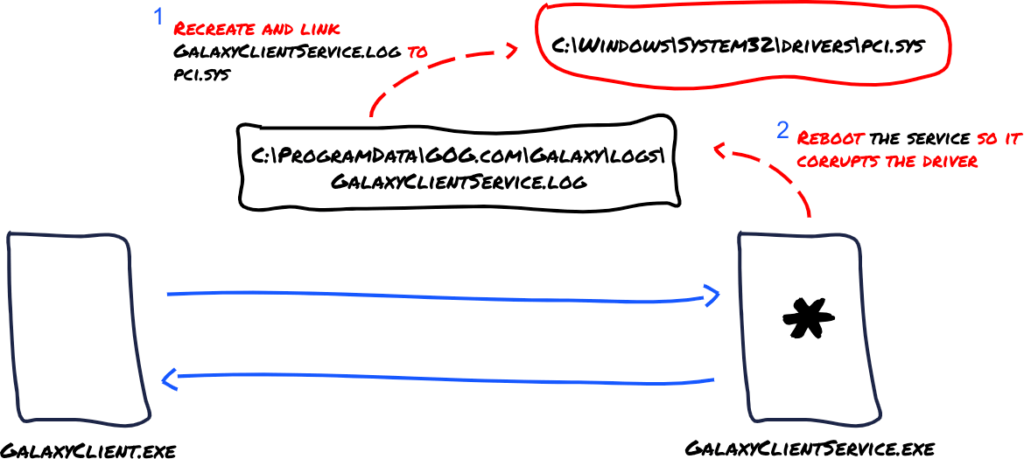
CVE-2023-50914 – The privilege escalation vulnerability was uncovered following the discovery of the DoS issue. It exploits the IPC mechanism between the GalaxyClient.exe and GalaxyClientService.exe processes. By manipulating the service process's behavior through custom packets or DLL injection, an attacker can gain elevated privileges on the system. This could allow for the execution of arbitrary code with system-level privileges, posing a significant security risk.
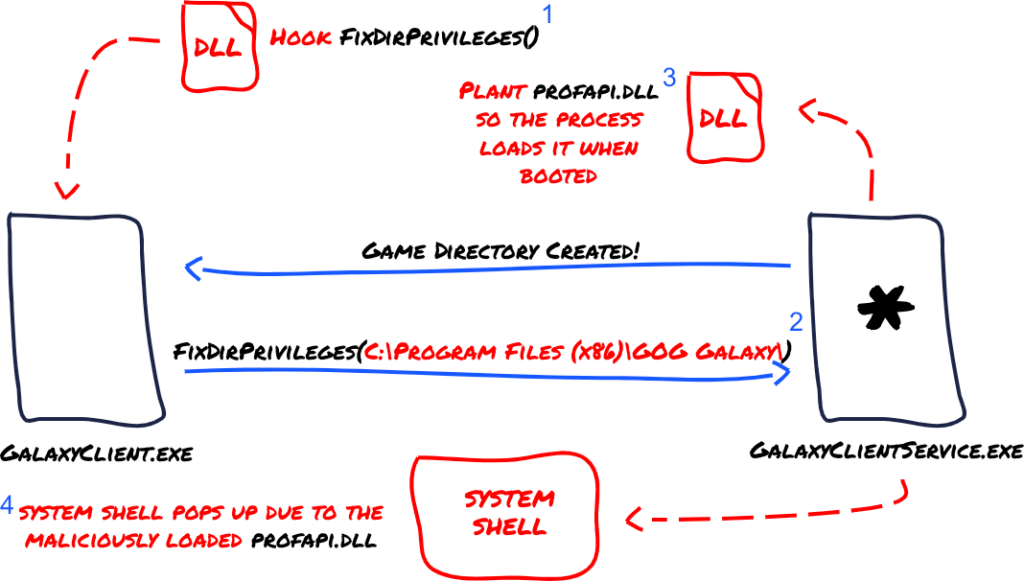
No fix available
Anvil Secure's investigation highlights the critical importance of securing IPC mechanisms and properly managing file and directory permissions in Windows applications. The researchers have provided detailed technical insights into their findings, along with proof-of-concept scripts and demonstrations on their GitHub repository and YouTube channel.
Following a responsible disclosure timeline, the researchers contacted GOG with their findings and adhered to a 90-day disclosure policy. Despite multiple communications, there was no definitive response from GOG regarding a fix or mitigation plan at the time of disclosure. This case underscores the challenges and importance of responsible vulnerability disclosure and the need for developers to promptly address identified security issues.
In light of these findings, users of the GOG Galaxy platform are advised to stay informed about any updates or patches released by CD Projekt Red that address these vulnerabilities. Maintaining an updated system and being cautious of the permissions granted to applications can mitigate the risk of exploitation.







Leave a Reply