
UPDATE July 2, 2021: Numerous false reports are circulating online about the LimeVPN hack, including the total customer size, financial data, and the live site being “hacked”. We have been in contact with both the hacker and LimeVPN since the hack was first announced on a hacker forum and have only reported what we could verify. Below are corrections to some of the false reports circulating online now, with exclusive statements obtained from LimeVPN today.
LimeVPN has also posted an update on the situation here.
1. What was hacked exactly?
When we first analyzed all available data on June 29th, we could identify usernames and passwords in cleartext, as well as transaction data (but no credit cards or sensitive billing information). The hacker claimed to have hacked LimeVPN's backup database only (not the live website or live VPN server nodes).
Here's is further clarification that LimeVPN sent us today:
We had an old backup server which was intend to move our billing system into a new server which was not active past few months. The leak seems to have happened in that server.
The only information that is stored in whmcs (our billing system) is a customers name/email/address (if they provide one). We do not and have never stored or logged any payment information. No credit cards are stored as well.
Secondly, this is restricted to billing system alone and our VPN nodes are not impacted. Our VPN node infra is secluded from our web app infra.
– LimeVPN statement to RestorePrivacy July 2, 2021
2. 800 LimeVPN users, not 69,400+
In our original report, we noted that the hacker claimed to have credentials for around 10,000 LimeVPN accounts. In his hacker forum post, he claimed 10,000, and in encrypted messages to us, he claimed the number was closer to 12,000.
Today, there are numerous reports circulating about 69,400+ LimeVPN customers, with this screenshot as “evidence”. We also obtained this information from the hacker a few days ago, but were able to see that:
- The number is actually 694,071, not 69,400.
- This is just an activity log of customer interactions, which is common with customer support management systems. It is not the total userbase of LimeVPN.
LimeVPN does not have 69,400 users and the hacker never claimed to have data on 69,400 users. To further clarify, LimeVPN provided us with this statement:
The total no of live accounts on these nodes are less than 800. And most of other data is related to our old orders (and they are not necessarily customers). So the backup, even if it had impacted any of the current user, its less than 800.
We have reset all access credentials, shut down wire guard servers and separating our billing infra from marketing info.
– LimeVPN statement to RestorePrivacy July 2, 2021
The screenshot is of the activity log. (It is not the no of users).
3. LimeVPN's website was not hacked
We are also woke up today to see numerous reports of LimeVPN\'s website was down and it had been \”hacked\” by the same threat actor who gained access to the old database. But neither the hacker nor LimeVPN ever claimed to have hacked the website.
We reached out to LimeVPN for comment and they had this to say:
As with our website, it has been having frequent ionode excess issue due to high traffic past 30 days. This is not related to this event. And finally there is no impact on VPN security the infra is seperated and has no impact. There is no way someone can map a user email to a live server session as these are not on any of these infra. We do not log any web sessions as well.
– LimeVPN statement to RestorePrivacy July 2, 2021
4. About 25 WireGuard keys for beta testing (not all private keys)
In our interactions with the hacker, he also claimed to have private keys for all LimeVPN users. According to LimeVPN, however, this is also incorrect and these were only about 25 keys for testing WireGuard with a few users:
The keys which is being referred are wireguard keys which was under beta testing. So there are less than 25 users who are using this and this was already suspended as soon as the information was made aware to us. This was a new feature we intended to launch shortly.
– LimeVPN statement to RestorePrivacy July 2, 2021
We have reset all access credentials, shut down wire guard servers and separating our billing infra from marketing info.
Note that WireGuard is a unique VPN protocol in that it uses keys for identification and encryption, while OpenVPN uses certificates. (See more in our explanation of WireGuard VPN.)
5. Transaction data (not sensitive financial data) was obtained by the hacker
In our original report, we noted that we could only see transaction data, which did not include sensitive financial information like credit card numbers or banking details. LimeVPN has corroborated this with the following statement:
There is no credit card / payment data. The only data is name/email/address along with the transaction id, amount and payment method. (This is auto logged by whmcs). We do not / never billed credit card on our internal systems. The only update we receive/log is transaction ids . Hence credit card leak is not true.
We were curious how the hacker had transaction data from as recent as June 30th, when LimeVPN had claimed this was from a months-old backup database. We posed the question to LimeVPN and they provided us with this explanation:
There is a API admin user which was on WHMCS which had access to the live updates. This API was the interaction between our order page and WHMCS. So when backup was leaked, this API credential was also leaked. This updates the order information between main website and WHMCS . (name, email, order id, payment method) . No payment is handled at our end. We only receive a webhook notification from gateway.
– LimeVPN statement to RestorePrivacy July 2, 2021
We have suspended the API access as well. As a precaution and to reassure users, we will be shutting down our current live server and migrate our live site to a new server with a new billing server deployed tonight.
6. What passwords were breached?
In the hacker\'s original post, he claimed to have usernames and passwords for 10,000 VPN accounts, with the passwords stored in cleartext, and provided us with a few screenshots for verification. While we could have downloaded a LimeVPN client and tested the credentials on live servers, we felt this was an ethical line we did not want to cross.
However, today we have finally gotten more information on these passwords from LimeVPN:
As far as access credentials are concerned, whmcs stores all passwords in secure hash.
The only password that was leaked is VPN connection password which was immediately suspended as well. This password is autogenerated and customers cannot set these so its unlikely any customer could be reused this anywhere.
The whmcs client area logins are secured.
– LimeVPN statement to RestorePrivacy July 2, 2021
7. Overview of the hack
Now that we have obtained more information from LimeVPN today, it appears that the hack is less significant than it is being made out to be by both the hacker and various news outlets. And after examining all evidence from the hacker and obtaining updated statements from LimeVPN, it looks like the hack did not affect the live VPN environment, but rather just a backup server.
Nonetheless, this backup server was still enough to obtain the following records:
- LimeVPN usernames and emails
- VPN transaction information (but no sensitive financial data)
- Other internal records
We\'ll keep an eye on the situation and continue to update this article with more information. Below is our original report, with corrections and updates based on new information we obtained from LimeVPN today.
Millions of people around the world use VPN services to achieve higher levels of privacy and security. Normally, this is a good idea, especially if you are using a high-quality VPN that has passed independent security audits. But as with everything in life, there are exceptions to the rule. Enter LimeVPN.
Earlier today (June 29, 2021), a hacker posted an ad on RaidForums to sell all of the data he obtained from hacking LimeVPN. As you can see in our screenshot below, the hacker is offering the full database of the VPN provider, including credentials from all registered users (email and password), along with billing and transaction information.
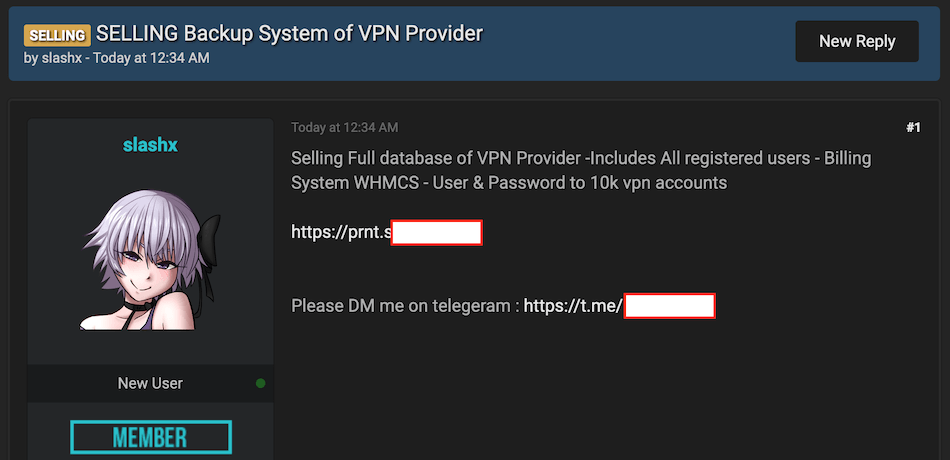
We examined the data sample on the forum and then reached out to the hacker for more information to write this report. The seller, who goes by \”slashx\” on the hacker forum, is asking only $400 for the complete data set, which includes:
- Credentials for all 10,000+ LimeVPN users (email address and passwords)
- Transaction records from WHMCS (the billing management systems used by LimeVPN)
- Internal VPN databases and records
We reached out to the hacker and were able to get more information, including the scope and impact of this data breach. He provided us with screenshots and samples of the data for sale.
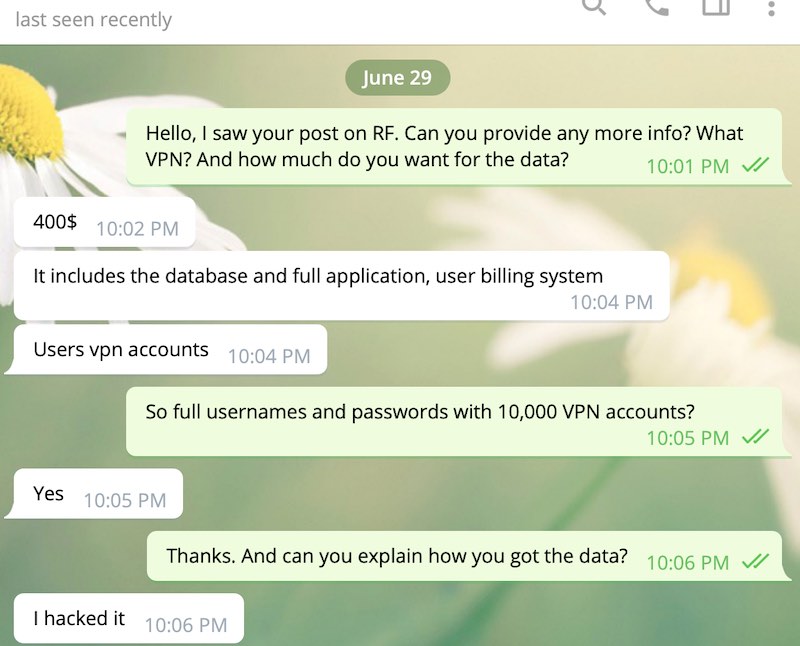
When pressed for details on how he obtained access to LimeVPN's system, the hacker would not elaborate. However, he did say, “I hack for a living” and claims to have the entire database from LimeVPN. This was the screenshot posted to RaidForums, showing a sample of some of the files in the LimeVPN database:
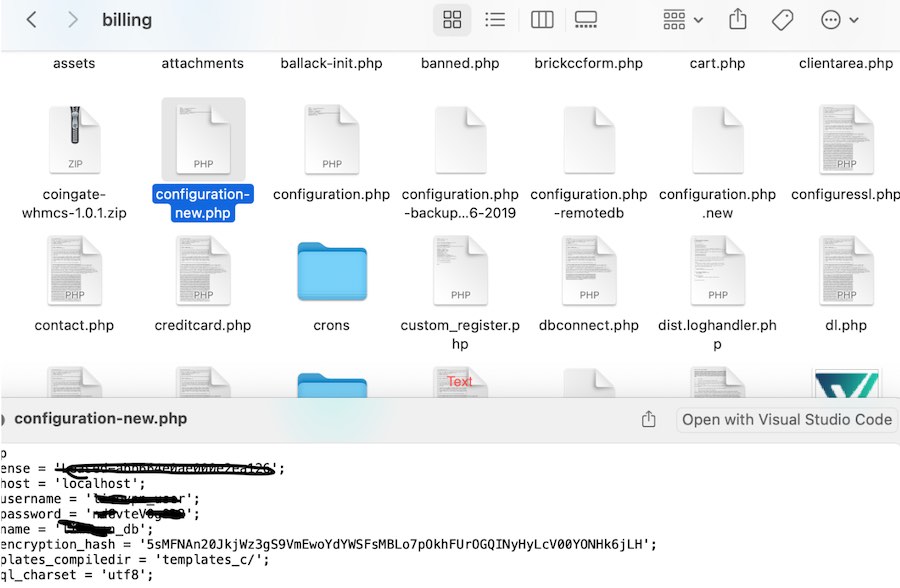
Now we will break down each aspect of this hack and how it affects LimeVPN users.
Credentials for LimeVPN users
In the original advertisement, the hacker claims to have login credentials for 10,000 users. In further correspondence, he told us that the number is closer to 12,000. We asked for a sample of this user credential data, which he provided.
Here is one of the LimeVPN user accounts that the hacker provided for verification. Notice the username is the personal email address of the VPN user and the password is not hashed:
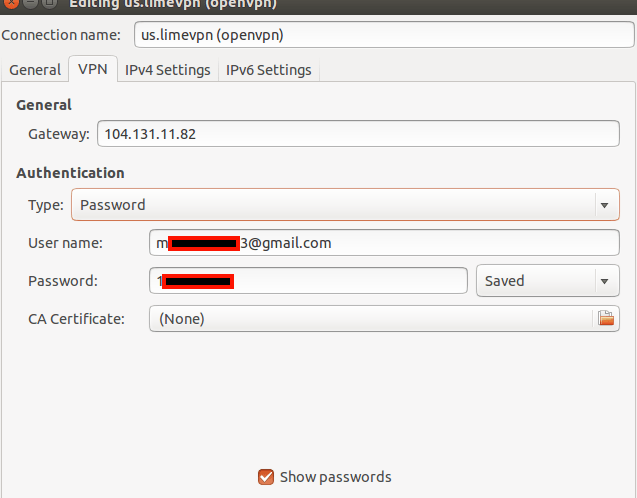
Additionally, he told us that he could decrypt VPN user traffic because he has the public and private keys for every LimeVPN user. If true, this of course de-anonymizes the VPN user and puts them at risk of further exploitation and traffic monitoring.
UPDATE: LimeVPN has clarified that only about 25 WireGuard keys were exposed for internal WireGuard testing.
LimeVPN user data exposed
As a brief recap, the hacker claims to have the following information for every LimeVPN user account:
- Username (personal email)
- Password (in plaintext)
- VPN subscription details
With usernames and passwords, one could attempt to launch credential stuffing attacks. With a credential stuffing attack, a threat actor can attempt to gain access to your other accounts by using the same email and password. And since many people recycle passwords (never do that!), this attack can yield results.
With a giant list of credentials, a hacker can use bots and automation to attempt to gain access to numerous different accounts.
UDPATE: According to LimeVPN, the passwords that were obtained by the breach were auto-generated VPN session passwords. Therefore these would not be useful in a credential stuffing attack.
RestorePrivacy Tip: One way to protect yourself when signing up for services is to use a temporary disposable email address (not your regular email address). That way, if the company's database is ever breached, only the burner email you used will be exposed.
LimeVPN transaction records
When analyzing the available sample data provided by the threat actor, it does not appear to contain direct payment methods, such as credit cards or bank details, of LimeVPN users. This is because the VPN uses a third party payment processor called WHMCS. However, the hacker claims to have obtained the entire WHMCS database with the LimeVPN hack.
34,423 transaction records
Additionally, the hacker told RestorePrivacy that the database contains 34,423 transaction records from LimeVPN users. This included the user\'s name and payment details. The screenshots below show recent transaction details, including up to today. These included the client\'s name and payment method, but no credit card details.
UPDATE: As confirmed by LimeVPN, the hacker had temporary API access and could see user purchases, but not billing information. This API access has now been suspended.
RestorePrivacy Tip: When purchasing subscriptions online, whether it is for a VPN or anything else, you can use an private or anonymous payment method. This is helpful because it does not link payment to your identity and can better secure your financial accounts if there is a data breach.
LimeVPN confirms their server was hacked
After verifying samples of the data from this hack, we attempted to alert LimeVPN to the problem and also get a comment on the situation for this article.
On June 30, 2021, LimeVPN replied back to our emails, confirming that their backup server was indeed hacked. Here is what they said:
We have verified that this is from our backup server and not from our main server. So the current customers are not impacted.
While we do see the hacker advertising the “backup system of VPN provider” for sale, we also see recent transactions from as recent as today (June 30, 2021). These lists include the full names of current subscribers.
LimeVPN has also added in an email to RestorePrivacy that, “We have reset all our access credentials and have started a system audit.“
Long-term implications of this hack
Trust is crucial for any VPN service. After all, you are trusting the VPN to secure all your internet traffic through their servers. If something goes wrong, that could give bad actors insight into everything you do online, and potentially worse, exploit the data they are able to collect.
When trust is breached with VPN services, many struggle to gain it back from their users. For example, we reported on the issue of IPVanish logging users for the FBI, all while claiming to be a \”no logs\” VPN service. Similarly, a few years ago, there was the case of PureVPN logging users while claiming to collect “zero logs”.
UPDATE: LimeVPN has confirmed they do not store any usage logs of their users. And I have not seen any records to indicate that usage logs (user activity, browsing, etc.) is being stored or available to the hacker.
And as we noted recently in our article on the LinkedIn data leak, hackers often put together various pieces of data to build data profiles of potential victims. The user accounts and data in this LimeVPN leak are just more pieces in the puzzle that can be used by bad actors. In many cases, threat actors will build up vast collections of data from various sources, such as we saw with COMB (Compilation of Many Breaches).
Updated Conclusion
While LimeVPN's backup server was hacked, the damage appears to be less than has been claimed by the hacker (and reported elsewhere).
A few years back, NordVPN also had a security incident, but this incident was even more limited in scope and did not affect any NordVPN users. With the NordVPN case, an expired TLS certificate was obtained for a single server in Finland. But this was of little to no value, as the certificate was expired and could not be used to access any customer data or decrypt traffic.
The website Have I Been Pwned is also useful to see if any of your usernames or passwords have been compromised.
To brush up on all the tools you need for digital self-defense, then check out our privacy tools page.







Leave a Reply