
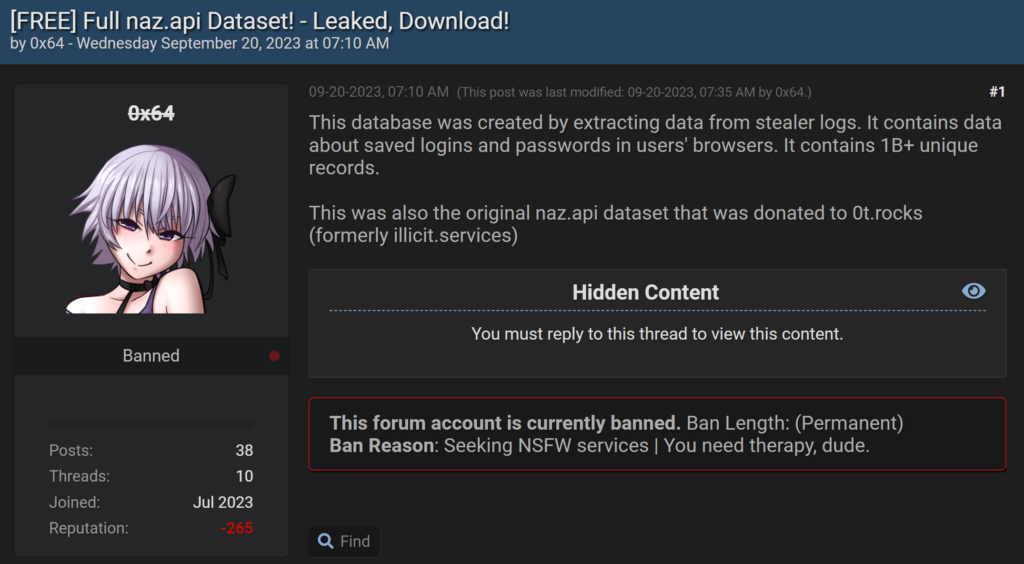
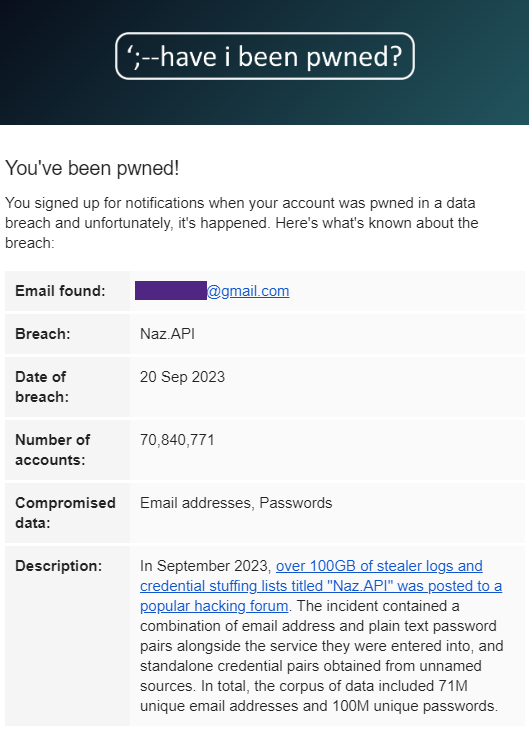
The account holders of roughly 71 million emails received a notice of password breach by alerting service Have I Been Pwned (HIBP), after the platform added a massive dataset confirmed to have been exposed online.
The dataset comes from Naz.API, a humongous collection of compromised credentials allegedly containing a billion accounts, which was circulated among cybercriminals last September, on hacker forums.
Troy Hunt
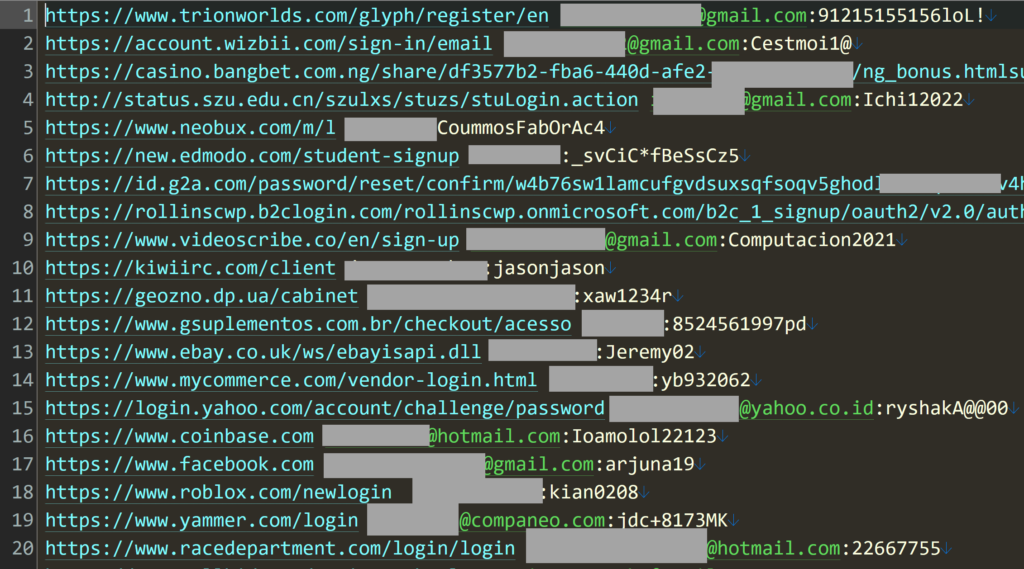
The data was derived from “stealer logs,” which are data chunks exfiltrated by info-stealing malware infecting people’s computers, typically under the guise of popular software like VPN tools, social engineering, or deceptive YouTube videos.
Troy Hunt
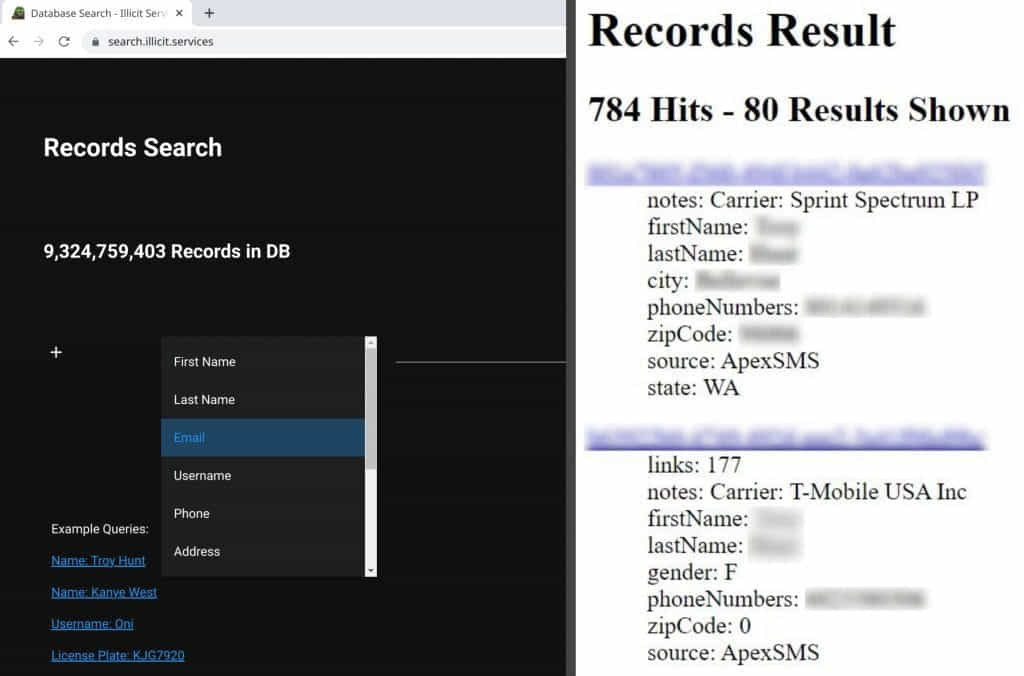
Previously, the Naz.API dataset fueled the catalogs of the now-defunct service ‘Illicit Services,’ which offered a powerful search system to allow cybercriminals to quickly locate any information about their targets.
Troy Hunt, the creator of HIBP, received a validated list of 319 files totaling 104GB in size, which contain over 70 million unique email addresses. Of those, roughly 35% are new entries for the service, meaning that they were never before reported as breached by another service. That equates to nearly 25 million email addresses and passwords confirmed breached for the first time.
HIBP validated the authenticity of the data using multiple passive confirmation methods that don’t involve attempts to log in with the leaked credentials. Those methods showed that the data is legitimate, with some passwords dating to 2020 or earlier.
What does this mean for users?
Practically, the addition of the Naz.API combo-list on HIBP does not change anything regarding the security of the exposed users, as it mostly contains data that cybercriminals have had ample opportunity to exploit in the recent past. HIBP is strictly an alerting service, so users cannot download any details from it about usernames, passwords, or any other specific info.
RestorePrivacy
The matter serves more as a reminder for the recipients of the notices that their account credentials stolen by info-stealing malware and other means are circulated out there, shared among cybercriminals, and could be used for phishing, account hijacking, impersonation, and many other dire scenarios.
Those combolists are commonly used in automated systems performing large-scale credential stuffing attacks, trying them out against many websites and reporting any successful attempts back to their operators.
Since there are no details on HIBP yet about which accounts were exposed, or the times of breach for each, the best course of action for the notice recipients would be to reset all their account passwords, picking unique and long passphrases if possible.
Also, enabling two-factor authentication wherever the option is available is always a good idea, as that would prevent account takeover even in the unfortunate cases when their credentials are stolen/leaked.







Leave a Reply