
A seven-year-long surveillance and monetization operation by a threat actor dubbed “ShadyPanda” has compromised over 4.3 million users via malicious browser extensions on Chrome and Edge.
An investigation by Koi Security reveals that ShadyPanda orchestrated a multi-phase campaign beginning as early as 2018. The threat actor used a patient, trust-building strategy to distribute seemingly benign browser extensions, only to later weaponize them with remote code execution (RCE), spyware functionality, and affiliate fraud mechanisms. The campaign is divided into four major operational phases, reflecting the actor's growing sophistication and strategic adaptation.
Koi's researchers identified the actor after tracking behavioral anomalies in multiple browser extensions. The threat intelligence uncovered a common infrastructure, code obfuscation techniques, and update mechanisms that tied together years of activity under a single coordinated campaign.
Koi Security
ShadyPanda's evolution
The ShadyPanda campaign evolved through several distinct phases:
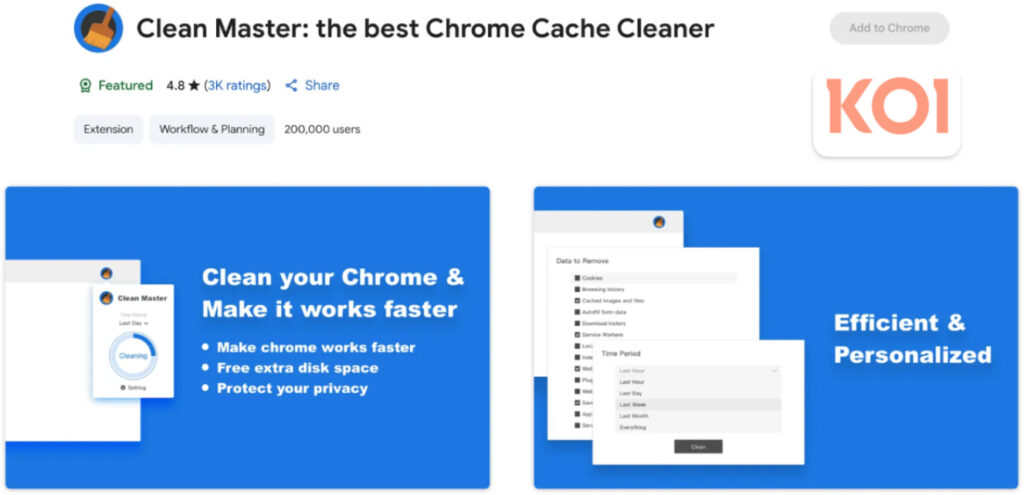
Phase 1: The Wallpaper Hustle (2023)
ShadyPanda launched 145 extensions disguised as wallpaper and productivity tools, publishing 20 to the Chrome Web Store and 125 to Microsoft Edge under aliases like “nuggetsno15” and “rocket Zhang.” The purpose was affiliate fraud, injecting tracking codes into shopping sites like Amazon and Booking.com to earn commissions, while silently collecting user browsing data via Google Analytics.
Phase 2: Search Hijacking and Cookie Theft (early 2024)
The attacker grew bolder, using extensions like Infinity V+ to hijack search queries through trovi.com, a known adware domain, while exfiltrating cookies and user input in real time. Domains such as nossl.dergoodting.com and s-85283.gotocdn[.]com received highly granular data, including search keystrokes and session cookies, all transmitted over unencrypted HTTP, exposing users to interception and profiling.
Phase 3: The Long Game (2018–2024)
ShadyPanda seeded legitimate extensions as early as 2018, such as Clean Master, gaining Google “Featured” and “Verified” statuses. After years of trust-building and over 300,000 cumulative installs, they pushed a mid-2024 update containing a fully functional RCE backdoor. The malware fetched and executed arbitrary JavaScript hourly from api.extensionplay[.]com, enabling capabilities like complete browsing history exfiltration, fingerprinting, and even potential session hijacking via service worker abuse.
The update mechanism leveraged Chrome and Edge's auto-update systems, ensuring malware was deployed silently without user interaction.
Phase 4: The Spyware Empire (2023–Present)
This phase marks the largest and still-active surveillance operation. Five extensions under Starlab Technology, a publisher linked to the earlier campaigns, have amassed over 4 million installs on Edge, including WeTab 新标签页 (New Tab Page) with 3 million users. These extensions are currently live in the Microsoft Edge store and continuously exfiltrate data to 17 servers, many located in China.
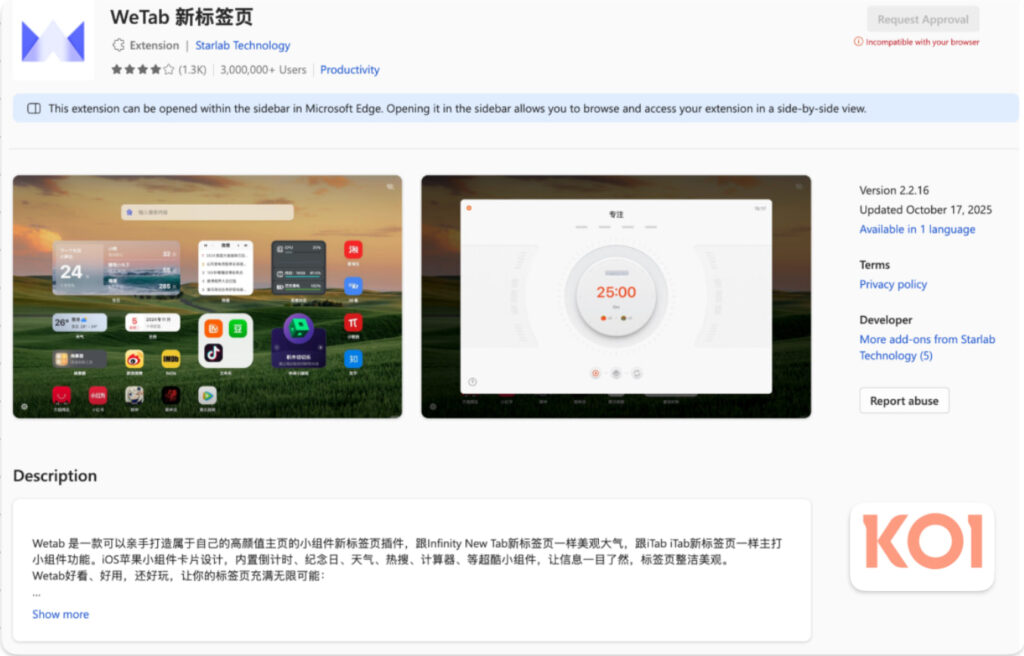
Data collected includes:
- Complete browsing histories in real-time
- All search queries and mouse click locations
- Browser fingerprints and page interaction analytics
- Access to localStorage, sessionStorage, and cookies
With permissions already granted, ShadyPanda could push an update at any moment that introduces the same RCE backdoor used in Phase 3.
Koi Security
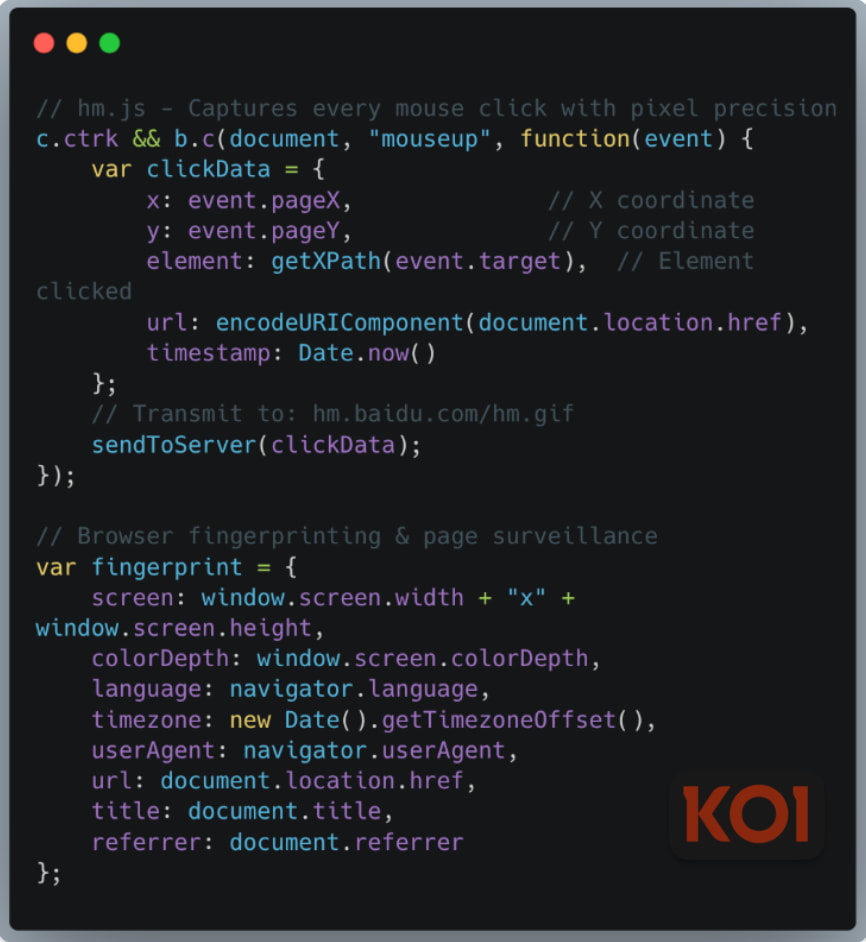
Koi Security's analysis shows ShadyPanda used a layered attack strategy. Infected extensions implement an RCE backdoor, polling api.extensionplay[.]com for payloads that run with full browser access. Exfiltrated data is AES-encrypted and sent to domains like cleanmasters.store and dergoodting[.]com. To evade detection, the malware uses obfuscated code, developer tool detection, and an embedded JavaScript interpreter. It also leverages service workers to intercept HTTPS traffic, enabling credential theft and session hijacking. While some Chrome extensions have been removed, Edge versions remain live and actively harvest data.
Users should check Koi's report for the complete list of extensions (by ID) and remove them from their browsers immediately. Also, it is recommended to disable automatic extension updates where possible.







Leave a Reply