This guide highlights the most alarming cybersecurity statistics and trends unfolding right now.
Today, our computers, smartphones, and other internet-connected devices have become indispensable parts of personal lives, as well as our businesses. As a result, cybercriminals are everywhere, and cybersecurity has become super important.
Unfortunately, right now it seems that the bad guys are winning. To illustrate the problem, I’ve compiled this list of the scariest cybersecurity statistics of 2019. The list is current as of July 2019. But given current cybercrime trends, I’m afraid we will look back on this list with nostalgia by the time 2020 rolls in.
Here are the 2019 cybersecurity statistics that scare me right now:
1. Ransomware is everywhere
Hackers infesting our computers with viruses and spyware is bad enough.
Ransomware takes the annoyance factor to another level. In case you are not familiar with the term, ransomware is a type of malware that locks up (encrypts) files on your computer, or the entire system.
To regain access to your stuff, you have to pay a ransom to the hackers. That ransom is typically in the form of cryptocurrencies, although some of these sleazy crooks will accept Visa, Mastercard, or other credit cards!
Ransomware has become a huge business, with an estimated cost of over $11 billion in 2019 alone. And the targets aren’t just kids who downloaded some dubious files from a porn site. Major companies get hit with this stuff, and so have dozens of cities, including Atlanta, Georgia; Baltimore, Maryland; and Augusta, Maine.
Baltimore alone estimates the cost at over $18 million, between the costs of recovering from the attack and potential lost or delayed city income due to everything being shut down.
While I was researching this article news broke about another city that was hit. On June 19th, the Palm Beach Post published a story detailing how the city of Riviera Beach, Florida paid $600,000 in ransom in hopes of getting the city government’s computers back online.
2. Industrial control systems may be the next big ransomware targets
According to Morey Haber and Brian Chappell at BeyondTrust, the systems that control national infrastructures could be the next big target for ransomware.
If little cities like Riviera Beach, Florida (2017 population 34,674) will pay $600,000 to get their computer systems back online, imagine the kind of ransom you might demand after taking control of a portion of the US power grid, or the control systems of a nuclear power plant.

Even scarier is the thought that a hostile power might get control of your country’s critical infrastructure. This is all too possible. For example, there have been numerous reports on how the US power grid is vulnerable to cyber attacks.
The possibilities are truly terrifying.
3. Data breaches will affect virtually everyone
According to the IT Governance Blog, data breaches resulted in the theft of nearly 1.8 billion records in January alone (2019). And the hits just keep on coming.
A company called IdentityForce keeps a running list of major data breaches on it website. At the time of this article (July 2019) this list included 81 major breaches affecting who knows how many billions of records. These breaches affect all types of institutions:
- social media platforms (Facebook and Instagram)
- online games (Fortnite)
- government agencies (US Customs and Border Patrol, Oregon Department of Human Services, and many more)
- hospitals (UConn Health and many others)
- popular apps (WhatsApp and Evernote)
We have no way of knowing how many smaller breaches took place. Nor do we know how many major breaches are currently being covered up by the victims, or haven’t even been discovered yet.
Even more concerning is the fact that companies are ramping up their data collection efforts. From a marketing and advertising perspective, data collection is good for business (but not customer privacy). A recent Bloomberg article highlighted this trend in the hotel industry:
At some properties, hotel brands are already collecting data on what temperature you like your room and how you like your eggs, betting that knowing that stuff can translate into better service. Other kinds of customer data—the annual conferences you attend or the date of your wedding anniversary—are largely untapped marketing opportunities. Some companies are also experimenting with putting voice assistants in their rooms or using facial recognition to streamline check-in.
Private companies in all sectors are collecting more data from their customers. This trend, together with a growing number of data breaches, increases the probability that every one of us will be affected sooner or later.
4. The cost of a data breach keeps on growing
Not only is the quantity of data breaches increasing, so is the average cost. Each year the Ponemon Institute conducts a study titled, “Cost of a Data Breach.” IBM was the sponsor of the 13th annual study, which was conducted last year (2018).
According to that study,
…the global average cost of a data breach is up 6.4 percent over the previous year to $3.86 million. The average cost for each lost or stolen record containing sensitive and confidential information also increased by 4.8 percent year over year to $148.
Let those numbers sink in: $3.86 million for a data breach, along with more breaches, each costing significantly more than the year before.
This is bad news all around – and it\'s not getting better.
5. More systems are coming pre-hacked
If you\'re a real tech geek, you have probably read about the United States Government’s concerns about 5G telephone systems made by the Chinese company, Huawei.
In a nutshell, the concern is that Huawei equipment has back doors built into it that could allow the Chinese government to spy on anyone who uses the Huawei tech. This seems like a realistic fear since Huawei devices have been found to have spyware pre-installed on them in the past.
And Huawei isn’t the only concern. Last year, Bloomberg reported that Chinese spies managed to get tiny chips installed on servers that ended up in the US Department of Defense, the CIA, and in the onboard networks of US Navy ships. Who knows where else the little buggers ended up. Before that, there were problems with Chinese spy chips embedded in printers destined for US Government facilities.
According to BeyondTrust’s 2019 Security Predictions, it is only a matter of time before corporations become the targets of these kinds of attacks (if they aren’t happening already).
And let’s not forget that the Internet of Things (IoT) trend is just getting started. The billions of tiny, Internet-connected computer systems in, well, virtually everything are going to be prime targets for hacking before or after they are installed. More on this in the next section.
6. The Internet of Things (IoT) is an open door for hackers
One of the hottest trends in technology is the expansion of the Internet of Things (IoT). Advocates claim all sorts of benefits can be gained by connecting pretty much everything to the Internet. Whether that is true or not, one thing is certain: many IoT devices are incredibly vulnerable to hacking.
The internet-connected portion of IoT devices is usually low-powered and slow, with few resources available for “secondary” features like cybersecurity. As a result, there have already been numerous IoT cybersecurity disasters. Here are just a few examples:
- Back in 2015, two researchers demonstrated the ability to hack into Jeep Cherokee SUVs and take control of the steering wheel or parking brake, while the vehicle was driving on the highway.
- My Friend Cayla, a toy doll that was so vulnerable to hacking that in 2017 the German Government called it, “an illegal espionage apparatus” and advised parents to destroy it immediately.
- Also in 2017, the FDA discovered that certain heart pacemakers could be hacked to run down the battery or even deliver shocks to the person using the device.
While some progress has been made here, IoT devices are still relatively vulnerable to hack attacks. On June 18, 2019, Avast published a blog post detailing how self-described “white hat” hacker Martin Hron hacked a smart coffeemaker. Not only did he tell it to stop making coffee, but he turned it into a ransomware device and a gateway to spy on all the connected devices on that network.
This video from Avast shows just how easy it can be to hack a smart device and get access to the entire network.
The IoT trend is yet another example of business decisions that conflict with personal privacy. Your ability to \”opt out\” is also getting more difficult as companies release a growing lineup of \”smart\” devices.
With billions of the things we use every day being converted into IoT devices, this problem will only grow.
7. More Americans are afraid of hackers than burglars, muggers, or terrorists
According to an October 2018 Gallup poll, Americans spend more time worrying about hackers and identity theft than they do about traditional problems like burglaries, muggings, even terrorist attacks.

/
More specifically, the poll shows that 71% of Americans frequently or occasionally worry about having their personal or financial information stolen by hackers. The second most common worry for Americans was identity theft (70%) another crime that is primarily perpetrated online these days.
Next, after these cyber-crimes, came the fear of a home being burglarized (25%) while the occupant was not home, with 25% of Americans frequently or occasionally worried about this possibility. Getting mugged, and being a victim of terrorism were even further from people’s minds, with about ¼ of the people surveyed worrying about them.
It is clear that cybersecurity issues are major worries for Americans and probably the citizens of other technologically advanced countries.
8. Cybercriminals could cost the world 2 trillion dollars this year alone
Estimates are that the costs of cybercrime will exceed $2,000,000,000 worldwide in 2019, predicts Juniper Research. It seems that efforts to stop cybercriminals from getting access to our systems are not working well enough.
According to venture capitalist Betsy Atkins, writing for Forbes.com, businesses should expect to focus more on detection of breaches and creating response plans for when breaches occur. This approach makes sense to me, as the Ponemon study cited earlier states that a company typically takes 197 days (more than 6 months) to discover that its systems have been breached.
How much is being spent on cybersecurity this year?
Gartner Forecasts estimates that in 2019 alone, more than $124 Billion will be spent on cybersecurity worldwide. Growing concerns over data privacy are pushing this number higher every year:
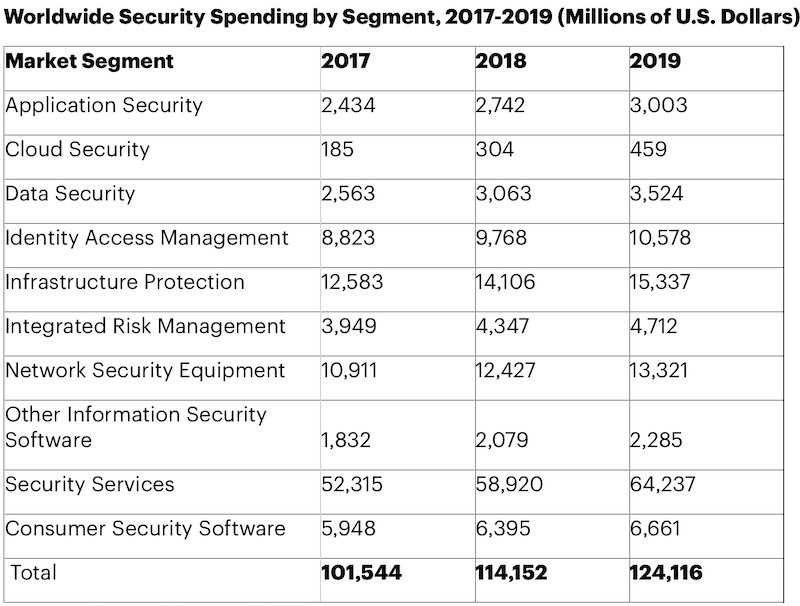
Stopping hackers is getting alarmingly expensive.
The key to surviving it is to get better at detecting the breaches and faster at fixing the problems and vulnerabilities.
9. More hackers are seeking to destroy your business
While it seems that most hack attacks aim to steal data from their targets, there is something even nastier going on out there. According to Symantec’s 2019 Internet Security Threat Report, nearly 10% of attacks in 2018 aimed to destroy the data on the infected computers. This number is an increase of approximately 25% over 2017.
This uptrend is marked by the return of a new, more powerful version of Shamoon, malware which targets organizations in the Middle East and erases their data. On June 22, 2019, Christopher C. Krebs, the Director of the Department of Homeland Security’s (DHS) Cybersecurity and Infrastructure Security Agency (CISA) issued the following statement about Iranian hack attacks that wipe the data on affected computers:
10. Few businesses are ready for a cyberattack
Despite the seemingly endless stream of news reports on Cyber Attacks against businesses, according to a 2018 survey by Minerva Labs, most IT professionals think their organization is not secure against attacks.
From the perspective of a business owner, this means that you need to plan your company’s response for the near-inevitable day that you get hacked. And it isn’t just the immediate detection and cleanup you have to worry about.
According to this report by Deloitte, there are 14 Cyber Attack Impact Factors that can plague a company long after the IT folks deal with the initial attack. Here are a few of those Impact Factors:
- Attorney fees and litigation
- Public relations problems
- Increased insurance premiums
- Lost contracts
- Loss of intellectual property
- Devaluation of trade name
The long-term costs to a business and its brand image from a cyber attack can truly be devastating. Plan accordingly.
11. Phishing attacks are less frequent but more targeted
The cybercriminals who use phishing attacks (where the attacker pretends to be a trusted entity) have apparently upped their game. According to Ganesh Umpathy at SonicWall, their Capture Labs threat researchers saw a 4.5% drop in attacks from 2017 to 2018. However, he also pointed out that,
As businesses get better at blocking email attacks and ensuring employees can spot and delete suspicious emails, attackers are shifting tactics. New data suggests they’re reducing overall attack volume and launching more highly targeted phishing attacks.
The bad guys appear to be focusing more tightly on high-value targets. The attackers may spend some time studying their target and applying various social engineering techniques to maximize the chance of success against that particular target.
Other techniques used in phishing attacks include:
- Buying compromised user credentials to take over the email accounts of trusted persons and use those accounts to launch their attacks
- Tailoring attacks to evade the built-in security of specific software products, such as Microsoft Office or popular SaaS products.
Remain vigilant against phishing snipers.
12. Microsoft Office documents are popular attack vectors
As we discussed in the last section, phishing attacks are often tailored specifically to defeat the defenses of popular software. This makes Microsoft Office one of the most targeted products of all. And the bad guys are having success here.
According to the Cisco 2018 Annual Cybersecurity Report, files with Microsoft Office file extensions are the most popular way to attack systems via email.
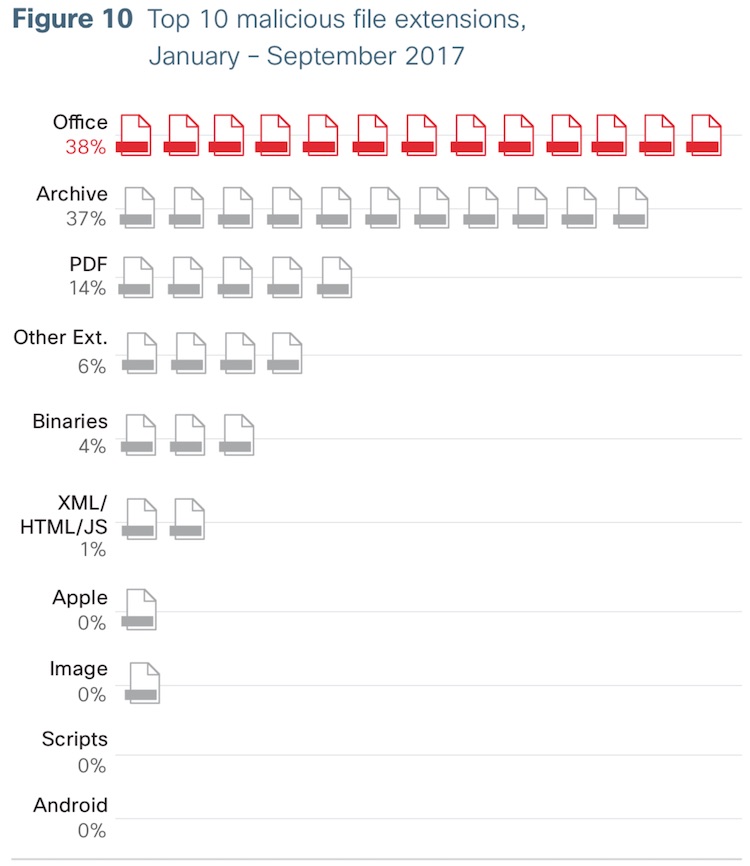
You can download the full 2018 report here.
13. Millennials are too lax about cybersecurity
As the baby boomers retire or pass on, the Millennial generation is becoming the majority. And if current trends continue, this transition means cybersecurity problems are about to get a lot worse.
Several studies including this one, and this one, and this one, indicate that the Millennials are far less interested in protecting their own privacy than preceding generations. They are also less likely to obey company policies related to data security. These characteristics will likely lead to nightmares for cybersecurity experts today and for decades to come.
According to a recent security report,
Millennials are almost twice as likely to go rogue compared to baby boomers, with 81% admitting they have used or accessed something on their work device without IT’s permission versus just 51% of older workers who have done the same.
/
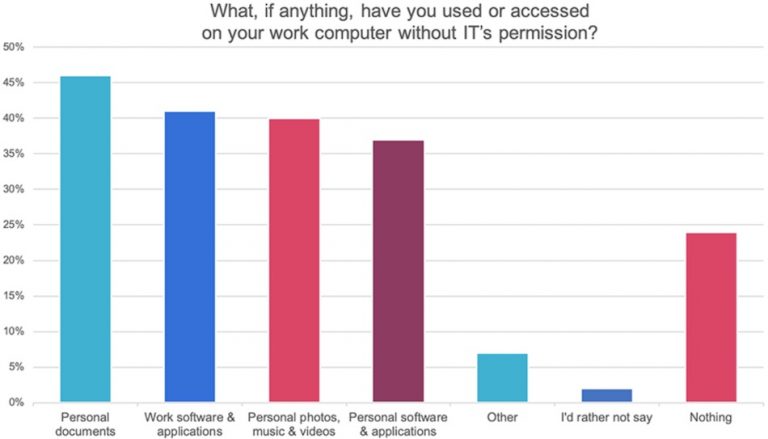
Hopefully millennials will up their cybersecurity game in the years ahead.
14. Hackers are increasingly targeting public WiFi networks
Many people are aware of the threats associated with using public WiFi, such as in airports, coffee shops, and hotels. But the problem is actually worse than most of us would like to acknowledge.
Hackers are increasingly targeting hotels in pursuit of high-value targets. A recent Bloomberg report describes how hackers check in to hotels to hack other guests and break into hotel networks to steal valuable data:
They’ve even used Wi-Fi to hijack hotels’ internal networks in search of corporate data. Just about all of the industry’s major players have reported breaches, including Hilton Worldwide Holdings, InterContinental Hotels Group, and Hyatt Hotels.
Before they’d checked in to their room, the leader had used his phone’s hotspot to create a new Wi-Fi network, naming it after the hotel. Within minutes, six devices had joined his spoofed network, exposing their internet activity to the hackers.
Mark Orlando, chief technology officer for cybersecurity at Raytheon IIS, advises corporate clients to avoid using personal devices altogether while on the road. That could mean requesting a loaner laptop or buying a burner phone. Even ordinary travelers should use virtual private networks to connect to the internet when outside the U.S., he says.
Exploiting public WiFi to collect data is incredibly simple and cheap, which explains this growing attack vector.
Motherboard (Vice) wrote a good overview of the problem, where they describe the $99 \”WiFi Pineapple\” that allows virtually anyone to exploit public networks.

According to the report,
The Pineapple is an invaluable tool for pentesters, but its popularity is also due to the fact that it can be used for more nefarious purposes. Hackers can easily wield the device to collect sensitive personal information from unsuspecting users on public Wi-Fi networks.
The real danger of a Pineapple attack is on public networks—places like your local coffee shop or the airport are all prime places for an attack.
If you must get on public Wi-Fi, your best bet is to get a VPN. VPNs are a secure way of surfing the net by first connecting to a VPN server before venturing onto the World Wide Web. The VPN server encrypts your data before routing it to its destination, essentially creating a protective shell for your data that makes it unintelligible to prying eyes. So even though an attacker may be able to see that your device has connected to their Pineapple, if you’re using a VPN they won’t be able to see the data they are routing.
As I pointed out in the best VPN report, VPNs are becoming mainstream for basic privacy and security. Unfortunately, many people remain oblivious to the inherent dangers of public WiFi, but awareness is growing. If you are a frequent traveler and want to remain connected with your devices, a good VPN is a must-have privacy tool.
Key takeaways and solutions for staying safe in 2019
Short of ditching all electronics and moving to a remote wilderness cabin, cybersecurity risk is an element to be mitigated rather than entirely eliminated.
- Be smart and vigilant. Common sense plays a huge role in staying safe online, where many people fall victim to suspicious links, malicious email attachments, and targeted phishing schemes.
- Keep all your devices up to date with the latest software and security patches. Whether it\'s your wireless router, phone, or work computer, security vulnerabilities are regularly being identified and patched.
- Limit vulnerabilities. It\'s clear that smart devices are a security risk, which will only get worse as the devices age (and the manufacturer does not keep the firmware updated). Therefore it may be wise to limit the smart devices on your network. And if you don\'t mind the hassle, going back to a wired (ethernet) connection will be more secure and also offer better performance.
- Having a good antivirus that respects your privacy may also be a wise choice depending on your OS. In terms of security, an antivirus is no silver bullet, but it can certainly help mitigate risk.
- Use a VPN for more security, which also has the added benefits of masking your IP address and location, in addition to encrypting and securing your traffic.
- Using strong passwords together with a reliable and secure password manager is also important. I like Bitwarden, a free and open source password manager, which also offers secure browser extensions.
- Limit the data you share. Given the growing trend of data breaches and the fact that companies are working hard to collect more of your data (for marketing and ads), the safest solution is to limit the data you share with third parties. Large corporate databases will continue to be hacked.
That\'s all for now, stay safe and secure in 2019!
Last updated on July 15, 2019.







Leave a Reply