
Zyxel has issued hotfixes to address a critical OS command injection vulnerability, CVE-2024-6342, impacting two NAS products that have already reached the end of vulnerabilities support. Despite their end-of-life status, Zyxel advises users to apply the hotfixes immediately to secure their systems against potential attacks.
The vulnerability, identified in the export-cgi program of Zyxel NAS326 and NAS542 devices, could allow an unauthenticated attacker to remotely execute operating system commands by sending a specially crafted HTTP POST request. This critical flaw exposes users to potential compromise, making immediate patching essential for system protection.
The vulnerability could have severe repercussions for individuals and organizations storing sensitive, confidential, or personal data. An attack could lead to unauthorized access, data theft, or tampering, compromising the integrity and confidentiality of critical information. Given that NAS devices often store backups or serve as central data repositories, exploitation of this flaw could result in devastating data breaches, exposure of private information, and disruptions to business operations.
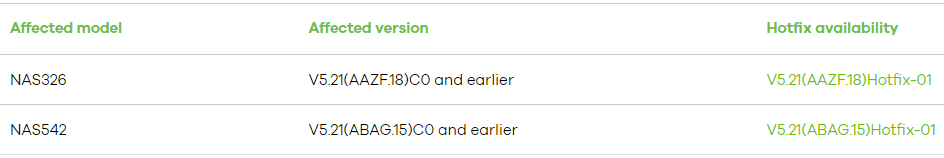
The affected products are the NAS326 running version V5.21(AAZF.18)C0 and earlier, and the NAS542 running version V5.21(ABAG.15)C0 and earlier. Zyxel has released corresponding hotfixes — V5.21(AAZF.18)Hotfix-01 for the NAS326 and V5.21(ABAG.15)Hotfix-01 for the NAS542 — to mitigate the risk.
Though both devices reached their official end of vulnerability support on December 31, 2023, Zyxel's provision of hotfixes underscores the severity of the issue. This vulnerability was reported by security researchers Nanyu Zhong and Jinwei Dong from the Vulnerability Assessment and Remediation Automation System (VARAS) at IIE, whose efforts were acknowledged in Zyxel’s security advisory.
Zyxel is a global provider of networking solutions, known for its routers, NAS devices, and other connectivity products. While the affected NAS models are older, many small businesses and home users still rely on them for data storage and access, making this vulnerability particularly concerning.
Despite the existence of a patch this time, users of the impacted models are advised to plan and execute their replacement in the upcoming period, as emergency hotfixes are more of an exemption than a rule, and the vendor may not be willing to allocate manpower and resources to address similarly critical issues in the future.







Leave a Reply