
Czech security researcher Marek Tóth unveiled a new class of zero-day vulnerabilities affecting the browser extensions of some of the most widely used password managers.
The flaws, rooted in DOM-based clickjacking techniques, remain unpatched in products like 1Password, Bitwarden, LastPass, Enpass, iCloud Passwords, and LogMeOnce, leaving millions of users vulnerable to credential theft, credit card leaks, and personal data exfiltration.
Tóth’s research, presented during DEF CON 33, was independently verified and later published by Socket Security, which also disclosed the vulnerabilities to the affected vendors. Despite responsible disclosure beginning in April 2025, six password managers are still vulnerable as of this week. LogMeOnce failed to respond to any outreach. 1Password and LastPass dismissed the issue as “informative,” indicating they have no plans to issue fixes without significant user pressure.
A gap in manual autofill
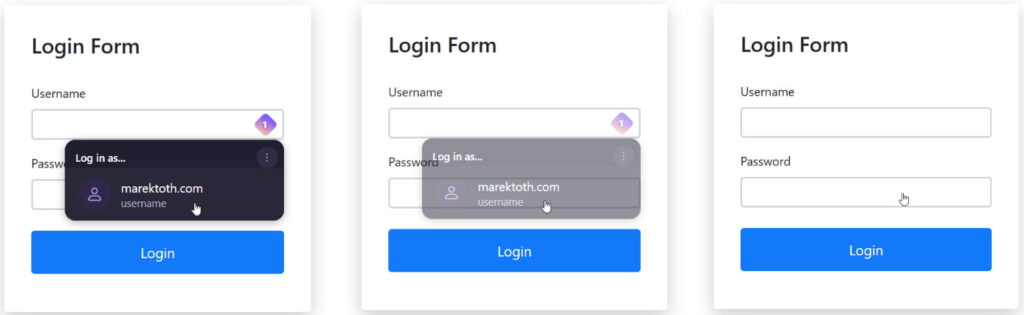
The vulnerabilities stem from a novel browser extension clickjacking technique that exploits how password managers inject interactive UI components such as autofill prompts into a web page's DOM. A malicious website can make these injected elements invisible through styling manipulations (e.g., opacity: 0) or overlay them with deceptive UI, tricking users into inadvertently triggering autofill actions.
Critically, only a single click such as accepting a cookie banner or closing a pop-up can be enough to leak sensitive information like login credentials, stored 2FA codes, passkeys, and even credit card numbers or personal addresses.
Proof-of-concept demos by Tóth illustrate how attackers can steal stored credit card details (Bitwarden, 1Password), exfiltrate personal data such as name, address, and phone number, and leak login credentials and TOTP codes if the attacker exploits a site with an existing cross-site scripting (XSS) or subdomain vulnerability.
The issue impacts manual autofill behavior widely used in password managers as a “safe” alternative to automatic filling. However, Tóth showed that DOM-based extension clickjacking defeats this safety assumption entirely.
The severity of the issue varies by data type and site context. On malicious websites, an attacker can trick users into exfiltrating stored credit card information or personal data with a single click. On vulnerable domains (via XSS/subdomain takeover), an attacker can hijack login flows, extract credentials and 2FA codes, and even exploit passkey authentication flows (e.g., via signed assertion hijacking).
Tóth documented multiple methods of DOM-based clickjacking including extension element manipulation, where attackers apply opacity: 0 to the injected UI component directly, parent element manipulation, making the element transparent while rendering a fake interface, and overlay attacks, inserting layers over the UI with pointer-events: none, so clicks pass through to the autofill component underneath.
Marek Tóth
The attack is modular, meaning that scripts can dynamically identify which password manager is present and deploy the relevant technique accordingly. Some managers’ UI elements remain manipulable via Shadow DOM or fail to detect high-risk overlay conditions.
Tóth demonstrated successful attacks against sites using popular passkey solutions such as Hanko, NokNok, and Authsignal, all of which failed to implement session-bound challenges, an essential security measure to prevent replay attacks.
Broad impact
The affected extensions are among the most widely installed browser password managers in the world. According to Chrome Web Store and other browser extension marketplaces, these services have a combined installation base of over 40 million users.
The following versions remain vulnerable:
- Bitwarden: 2025.7.0
- 1Password: 8.11.4.27
- LastPass: 4.146.3
- LogMeOnce: 7.12.4
- Enpass: 6.11.6
- iCloud Passwords: 3.1.25
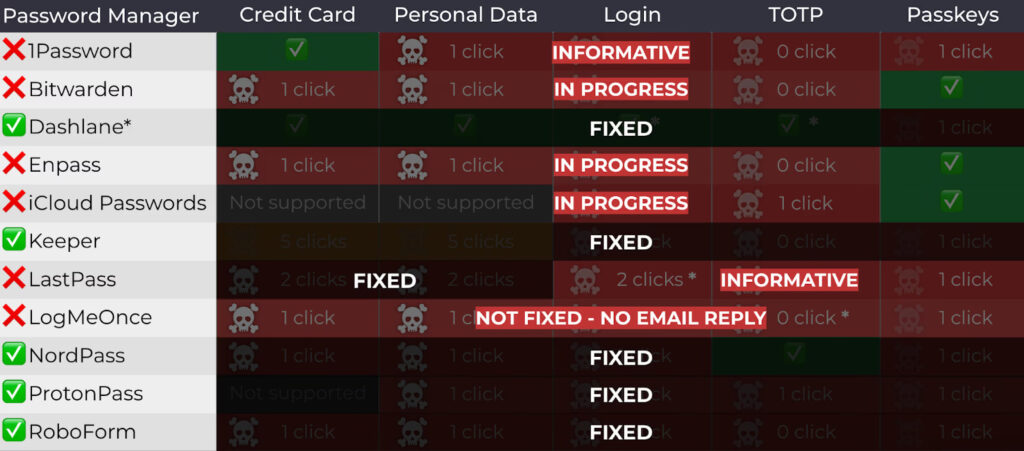
In contrast, password managers like Dashlane, NordPass, Keeper, RoboForm, and Proton Pass have implemented mitigations and are no longer vulnerable to the reported attacks.
Socket
1Password and LastPass have argued that defending against clickjacking is outside their control, placing responsibility on users to avoid malicious websites. However, Tóth’s research emphasizes that attackers can exploit even trusted domains if XSS or subdomain takeover vulnerabilities are present.
Bitwarden, Enpass, and Apple are actively working on patches, but the latest versions remain vulnerable. LogMeOnce did not respond to either Tóth or Socket Security and remains fully exploitable.
Update 1: Bitwarden sent us the following statement after we published the article:
This has been fixed in version 2025.8.0 rolling out this week. As always, users are advised to pay attention to website URLs and stay alert for phishing campaigns to avoid malicious websites. – Bitwarden







I could not help but notice all these hacks that have been going on have involved ONLINE password managers . OFFLINE password managers such as Keypass XC are orders of magnitude more secure . I keep all my passwords in my email account ; but you cant read the file even if you find it . Most people would not even know how too read it , much less decrypt it .
ok? it’s called convenience.
Doing all that, even after setting it up would inconvenience the vast majority of the population. Yes, it at least should be more secure because it wouldn’t have internet access, but at a big inconvenience.