Security researcher ‘Mobile Hacker’ has demoed a zero-click attack that leverages recently disclosed Bluetooth vulnerabilities to install a Metasploit payload on unpatched devices.
For the demonstration, the researcher used proof-of-concept (PoC) exploitation scripts released by Marc Newlin earlier this month, which are publicly available via GitHub. The scripts leverage the flaws tracked as CVE-2023-45866, CVE-2024-21306, and CVE-2024-0230, to force-pair emulated keyboards via Bluetooth on various OS architectures, enabling keystroke injection.
The scripts work in devices where Bluetooth is enabled and which are currently active, meaning in an unlocked state. The attack can originate from another mobile device in Bluetooth range and does not require interaction with the victim, nor does it produce any discernible evidence of a breach.
Bluetooth attack demo
Mobile Hacker uses a rooted OnePlus 7 Pro device with a custom NetHunter Kernel supporting Bluetooth scanning and an external Bluetooth dongle connected with an OTG adapter to discover nearby targets. The scanning software used in this case is the Kali NetHunter Bluetooth Arsenal.
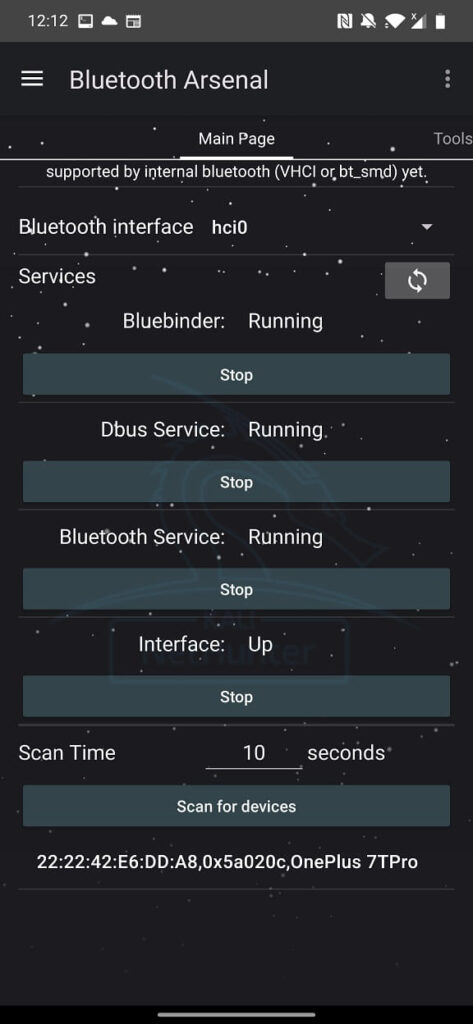
The researcher cloned exploitation scripts from Newlin’s repository and used tools like Pydbus to interact with the Bluetooth protocol. The attack requires specifying the target’s MAC address, shown in the scans if set to “discoverable.” During testing, the researcher injected a series of Tab key presses, observing that it works on console output.
The worst scenario demonstrated by ‘Mobile Hacker’ involves hosting a Metasploit payload on a remote server and then using the exploitation scripts to open the target’s browser, navigate to the hosting URL, download the payload, and execute it.
Metasploit is a popular penetration testing framework that cybersecurity professionals use for exploiting vulnerabilities, and it includes a wide array of payloads for different purposes. In this case, a Metasploit payload running on an Android device could give the attacker full control over the device, including access to sensitive data, control over the device’s functions, and the ability to use the device as a launchpad for furthering the attacks on the victim’s network.
Broad impact
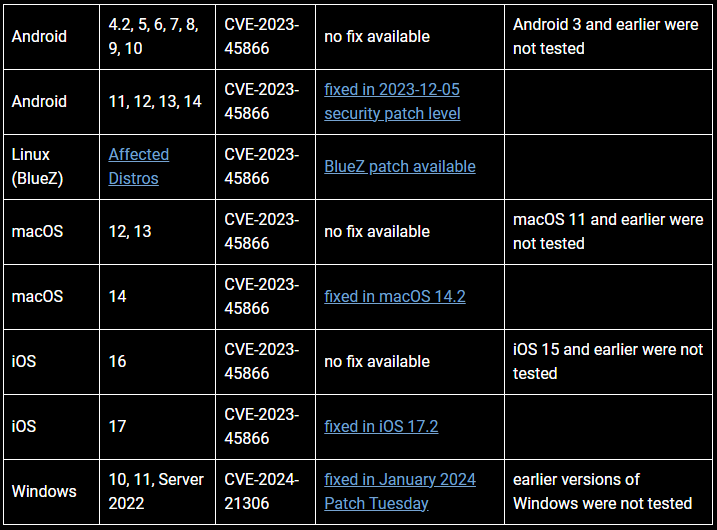
The mentioned Bluetooth vulnerabilities impact a range of operating systems across different devices, but in most cases, they have been addressed by recently released security updates. The situation is particularly bad in the Android space, where vendors end support for devices after only two years, follow infrequent (quarterly) updating circles, delay the release of security updates sometimes for months, etc.
Specifically, all Android devices running version 10 and older are vulnerable to the mentioned Bluetooth flaws, and hence, are susceptible to zero-click attacks. For Android 11 to 14, which are actively supported releases, the flaws were addressed in the December 2023 patch.
Regarding iPhones, the flaws were addressed by Apple in iOS 17.2, but no fixes were made available for previous iOS versions used by older models.
Impact on Linux depends on the distribution; macOS fixed the flaw in 14.2, and Microsoft released fixing updates for Windows 10, 11, and Server 2022 in the January 2024 ‘Patch Tuesday.’ Older macOS versions like 12 and 13 are vulnerable, and no fixes will be made available.
Mobile Hacker
Owners of impacted devices who are unable to upgrade to a safe version are recommended to either disable Bluetooth or keep their phones locked when in public spaces with many people in close proximity.
Further reading:
- Apple and Google Propose Specification to Stop Bluetooth Tracking
- iOS Apps with Bluetooth Access Could Listen to Siri Conversations
- CyberGhost VPN for Windows Vulnerable to Command Injection
- Kaspersky Shares Method for Detecting Spyware on the iPhone
- Abuse of IPFS to Host Malware and Phishing Kits on the Rise







Leave a Reply